Magnetic locks are often used on glass doors, or door sets that don’t have a center post.
Ever since humans have embarked on the road to civilization, physical means have been used to control the entry and exit of people, livestock, and products. From a simple door on a house or a fence around a farmer’s field, the ability to control entry and exit has been a cornerstone of security. Modern access control is the combination of physical barriers, such as doors, parking garage gates, and turnstiles, with electronic devices that allow users to input their credential data, which is then compared with a software database that allows or denies the entry of the user based on who their credential says they are, along with such criteria as the time of day, day of the week, and other information.
In order to control access to an area, there must be some type of barrier, such as a gate, door, or turnstile that stops people from entering unless the access system allows them in. The first thing to evaluate is what type of barrier must be connected, and how that entry can be electrically locked and unlocked (such as a door) or activated (such as a parking garage barrier).

Because they often can be used with existing door hardware and locksets, strikes are the most common devices used to electrically operate a typical door.
DOOR CONTROL HARDWARE
The most common application for access control systems is a personnel door, where people enter and leave a building, room, or area. Door hardware constitutes various types of devices that can lock and unlock the door via an electrical connection. The following are brief descriptions of typical door hardware arrangements and their implications for access control usage:- Electric strikes – Installed on the mechanical lock side of the door, electric strikes are the most common door control apparatus. Powered by low voltage AC or DC, strikes can be selected to be fail safe, meaning that the door is open if power fails, or fail secure, where the door remains locked in the absence of electrical power. Door strikes allow the use of panic hardware, so that a person inside the room or building can push the release bar to exit the building even if the strike is in the closed position. Electric strikes are typically used on framed wooden and metal doors, and are generally the least expensive way to control doors.
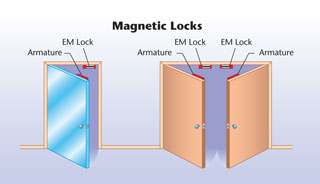
- Magnetic locks – Some door types, such as glass doors or double doors that do not have a center post cannot be controlled with a strike. Magnetic locks use an electromagnet to provide a powerful locking force to a door. The electromagnet is installed in a fixed position, while a metal plate is installed on the moving portion of the door, lined up with the magnet. Magnetic locks can provide various amounts of holding pressure, from 300 to 1,200 pounds. These devices are by nature fail safe, as removal of power, whether by the access system’s controlling relay or by power failure, will release the door. Power supplies with backup batteries are often used to provide emergency power to magnetic locks.
- Door bolt locks – Some doors cannot have a strike installed, and the usage of a magnetic lock may be impractical or aesthetically inappropriate. An example would be an ornate arched door in a church. Door hardware vendors supply various types of electrical bolt locks, which throw a smooth bolt typically into the top or sometimes the bottom of a door, providing an electrically controlled locking mechanism.
DOOR POSITION DEVICES
The physical state of a door, open or closed, determines the security of that particular portal into a building or room.Door position devicesprovide the open or closed status of a door to the access control system, allowing it to engage locks, annunciate alarm conditions, and other actions that provide security integrity. For example, an authorized user may access a door and prop it open, allowing the unauthorized entry of other people and/or the removal of property. A door position device will detect the opening of the door upon the presentation of a valid credential, which starts a programmed timer within the access system for perhaps 20 or 30 seconds. When the door position device indicates that the door has shut, the access system can be set to relock the door control mechanism. If the door is propped open past the timer duration, local and remote alarm signals can be set off and transmitted.There are two basic types of door position devices. The most common type is a door contact, either mechanical or magnetic, typical of those used for intrusion detection systems. Such contacts can be surface mounted or concealed, and are typically wired into the access control panel to terminals designated for a particular reader and/or door. While almost any type of door contact can be used for this function, it is important that this device’s contacts be used only for the door position function, and not also connected to the intrusion detection system. If it is desirable to only install one contact set on a door, DPDT (double pole double throw) contacts are available that provide two electrically separate contacts, one for the access system and one for the intrusion system.
In some cases where it might be difficult to install a door contact set, door position sensing can be achieved by installing specific door strikes or wired hinges that include a door position output. Using these devices can reduce the cost of a system, because they can make the installation of a separate contact unnecessary.
These built-in devices are particularly attractive when installing an access system on a fire-rated door. Because fire doors are of a specific construction, drilling holes in the door for the mounting of a contact set magnet may well violate the door’s fire rating integrity, perhaps causing the replacement of an expensive door at the installing dealer’s expense.
Subsets of door position devices are latch position monitors, which can be included with electric strikes. These contacts provide an output for the position of a deadbolt lock, either locked or unlocked.
Whether a separate contact or an output from the locking device, door position devices are typically installed on each access-controlled door.

REX devices are usually installed with the detection pattern aimed to “look down†near the controlled door or doors.
REQUEST TO EXIT DEVICES (REX)
Take the example of an access-controlled door with a credential reader on the outside, which allows authorized personnel in. This door is equipped with a position contact that tells the access control panel whether the door is open or closed. When a person chooses to leave a building through this door, some type of input must be provided to the access panel, telling it to unlock the door for egress. This input can be another credential reader on the inside of the door, and the person can present a valid credential to activate the access system. However, placing another reader on the inside of the door is costly, and is generally only used in high-security applications where either anti-passback or building roster functions are needed.Instead, some type of input device is installed near the door, providing either manual or automatic release of the door when people approach it. This release input also allows the door to be opened from the inside without generating an alarm condition.
In some cases, the request to exit device is a labeled “mushroom†switch that is manually pressed. The request to exit input also can be included in the door’s panic release pushbar.
An electronic solution to this need for non-alarm generating exit is by installing a REX sensor, which typically uses motion detection technology, such as passive infrared detection, which senses that a person is standing in proximity to the door. When activated, the electronic REX will release the door for a specified time period, perhaps 30 seconds, and automatically relock the door when the connected door position sensor indicates a closed position. This provides a hands-free door release capability, with no manipulation or credential required to exit the door.
Sophisticated electronic REX devices provide a local programmable controller for a particular door’s functions. Time- and function-programmable relays control the door release, while integrating the inputs from the access control panel, fire alarm system, and door position switches. An included programmable sounder can be set to sound a local alarm if a door is opened improperly. This sounder can be activated either by the logic of the REX or by an external input from the access control panel, intrusion panel, or other activation.
In some applications, the capability of using sequential sensor input can provide added security to the door exiting procedure, while reducing nuisance alarms. An additional sensor, such as a PIR or pressure mat, can be located so that people walking towards the door trip the first sensor, which starts a timer in the REX. If the motion detection in the REX detects movement within 10 seconds, the REX will open the door. If the auxiliary sensor isn’t tripped first, the REX will not open the door.
Electronic REXs can provide a variety of door control options, reducing cable runs and labor costs, while providing an easy-to-use system for end users.
DEVICE POWER
Door release devices such as strikes and magnetic locks typically operate at 12 or 24 volts AC or DC. The planning of an access control application must include the selection of power supplies to provide adequate power to operate the connected door devices. A number of security equipment vendors provide power supplies specifically designed for use with access control devices.It’s important for fledgling access control companies to understand the concepts offail safeandfail secure, as they relate to door release devices. A system that is fail safe will open door release devices in the event of power failure, while a fail secure system retains the door release in the closed position. It is very important for access control system planners to have a clear understanding of the AHJ’s requirements for the release of labeled exit doors in the event of primary power failure or fire alarm system activation.
Security system dealers need to calculate the amount of current necessary to operate the door release devices, and how much standby battery power should be provided to maintain the operation of the access system in a power failure.
Two issues are essential when planning an access system’s power supply. First, the cabling type and distance from the power supply to connected door releases must be considered, because long cabling distances may require increased conductor size to compensate for current drop. Second is whether the AHJ requires that exit doors be automatically released when the fire alarm system goes into alarm, which may require interconnection of the access control power supply(s) and the fire alarm system.
CREDENTIAL TECHNOLOGY
A variety of different types of devices can be installed to provide an input for authorized users to open a door or access a specific device. Credential readers take the input from a user’s access card, keypad input, or biometric information and transmit it to the access control panel, which decides to allow or disallow the access request based on its programming and database.Generally, most credential readers, regardless of type, will use theWiegandcommunications protocol to communicate the credential input to the access control panel. This format provides a 26 to 37 bit transmission, which must be matched at the access control panel. Wiegand communications is typically accomplished using an overall shielded five-conductor cable, with the maximum distance being 500 feet from the credential reader to the controller panel. Many manufacturers will specify a specific cable vendors’ product to be used with their devices.

Combined keypad/fingerprint readers can be programmed to provide quick confirmation of a person’s identity.
KEYPADS
Keypadsprovide a knowledge-based access credential, without the user having to carry or produce a physical card. A variety of keypad forms and environmental capabilities are available, allowing their use in indoor and outdoor installations. The advantages of keypads are that there is no physical card that could be potentially passed to an unauthorized user; however, it is a simple process for the keypad code itself to be told to another person.Keypads are also slower than card readers, as users must remember their code, punch it into the keypad, and wait for the door release. This issue should be carefully considered if high-volume user entry is required, for example if all employees must enter through one or more specific doors at nearly the same time. Some integrated access control and intrusion systems can use the alarm keypad to perform double-duty for both alarm setting (arm/disarm) and access control entry.
There are two primary uses for access control keypads; low-cost systems, as there is no cost for physical cards or credentials, and in conjunction with another access control credential, such as a card or biometric reader.
BIOMETRIC READERS
Fingerprints, palm prints, and the human iris possess individually unique characteristics that can be used to verify a person’s identity. Thisbiometricinformation can be stored within an access control system and read by specific devices. The primary advantages of biometrics are very high security and the elimination of specific credential devices (cards) and their related costs.There are a number of concerns when considering the use of biometric devices. These readers are generally higher cost than card readers, so access systems may be planned to include biometrics only at specific locations. Biometric personnel records are larger files than traditional card access strings, which can cause slow “lookup†time, which is the time lapse between when the biometric input is provided to the reader and when the door is released. These large files also must be stored within the access control system, which may limit the maximum number of users for a particular system. Biometric readers require physical enrollment, so system administrators cannot remotely issue a credential and ship it to a user; the user must be present at the reader for enrollment.

A specific frequency is emitted by the reader, powering the card, which then transmits its data.
PROXIMITY CARD READERS
The predominant technology in use today for access control credentials is theproximity card.The card reader transmits a specific RF frequency at all times. When a card containing the specific access control credential coding nears the reader, the reader’s transmitted energy is picked up by the card, which uses that energy to transmit its coded information to the reader on a different frequency.
Proximity readers can be either short- or long-range, with the long-range units providing a higher RF power output to allow for longer read distances.
There are several reasons why proximity technology is the most popular choice for access control credentials. The card can stay within a purse or wallet, not requiring the user to extract them. The access control information is in a simple, short format so card read times are very fast. Proximity card readers have no moving parts, so they are highly reliable. Also, there is no card slot, which can be jammed with glue or ice. Proximity cards also can be printed with the user’s photo and other information, providing a combination ID badge and access control card.

Smart cards contain a CPU and provide read and write capabilities. These cards can be used to hold biometric access data, debit card functions, and more.
SMART CARDS
In the evolution of card-based access control credentials, thesmart cardis the highest form available, providing multiple capabilities and functions within a single card.Smart cards contain a CPU, RAM, and ROM read/write data storage capability, which in essence makes the card a mini-computer with the ability to encrypt and authenticate the data held in the card’s ROM, providing sophisticated levels of security for communication.
There are two primary standards for smart cards: the ISO/IEC (International Standards Organization/International Electrotechnical Commission) 14443 and 15693. While both standards operate at 13.56 MHz, the two standards differ in terms of read range, maximum data storage capability, and data transfer speeds. The 14443 standard provides for a 4-inch read range, while the 15693 standard calls for a 3.3-foot reading distance.
Smart cards can be read using either acontactorcontactlessmethodology. Contact-type systems, where the card physically is inserted in the reader, are a more mature technology than contactless, providing faster read/write capability and greater memory storage. Contactless smart cards use RF to transmit data to a reader. Contact cards provide higher security, as the data from the card is not transmitted through the air. Contactless technology provides faster user interface and building access throughput.
One key advantage to smart card systems is the ability of a single card to store and transmit separate information for different systems. For example, a single card can be used to access a building via the access control reader, and also provide a separate set of user authentication information to allow access to logical resources, such as computers or programs within a computer system. A typical usage of smart cards is to combine access control and debit card functions within single-user cards at universities, hospitals, and other such enterprises.
One innovative use of smart card technology is to have the card contain the biometric characteristic file of the user. The user first enters a keypad code, presents his or her biometric input (fingerprint, iris), and has her card read. The access system then can verify that the user keypad code presented matches the biometric information contained on the user’s card. This can speed up the process of verification, while eliminating the centralized storage of sensitive biometric information. This is a common methodology used in the European Union.
It’s important to consider that the technologies described above can be used in various combinations. For example, a user can drive an automobile into a garage, and use a prox card to gain entry for parking. The same user/card combination may be presented at the entry door proximity reader to allow door entry, while the card may be used in combination with a biometric reader to allow entry to a sensitive room.
MULTI-TECHNOLOGY CARDS AND READERS
Legacy access control systems provide particular challenges to building owners and security installation companies. Theoretically, an existing system can be completely replaced with new credentials, readers, controller panels, and operating software. This approach is costly from an equipment/installation perspective, and may create substantial interfacing problems with existing data files.Multi-technology cards and readers provide a ready migration path from a legacy system to a new one, or can allow a new system to be integrated alongside an existing one, with users having to carry and use only a single card. For example, if a company installs a debit card system for its cafeteria, it can issue new access control credential cards that contain both smart card technology (for the debiting function) and prox capability to use the existing access control system.
There are many possible ways to achieve this multi-system functionality. Vendors provide single readers that can process multiple technologies, or separate readers can be installed near each other to achieve the same result. Another approach is to use multi-application smart cards, which can store separate sets of information on them. Contactless smart card readers are available that can read the information of the smart card, yet transmit it to an access controller panel in the legacy format required for that particular access system, such as Wiegand. So the card population can be changed along with the readers, but the rest of the access system can remain as is. This single-card approach may be the most cost-effective and convenient way to provide multi-system functionality for a particular system.
Credential cards can be purchased with multiple technologies built-in to them, such as magnetic stripe/prox or prox/smart card. Dealers should consider that the cost for these cards would be higher than the cost for the individual technologies if put on separate cards. Multi-technology contactless readers typically must be configured so that each technology operates at different frequencies to avoid interference.
CONTROLLER PANELS
Once the selections of door release, type of credential reader, door release power, and REX issues have been made, installers must consider what manufacturer and type of access controller panels will be used, and where they’ll be installed. Access controller panel features differ across manufacturer platforms, but most provide some standard functionality. The controller panel will typically have electrical connections for the selected credential reader, a relay output to control the door release, door position input, programmable inputs and outputs, and inputs for the REX.On the software side, access controller panels will possess a CPU to process incoming information and activate the system’s capabilities, while an on-board database contains the credential verifying information for the users of that particular controlled door or device. When a credential is presented, the access controller will compare the input to its database to determine whether access should be allowed to a particular door at a particular time and day.
Most current access controller panels utilize one of the Wiegand communication protocols, and panels will typically control two credential readers with their associated portals, although some can be expanded. Battery backup is available, or can be added separately.
The placement of the access controller panels must allow for credential cabling to reach the controlled doors within the maximum distances of the readers selected.
Most controllers are downloaded with their relevant credential database from a central host computer, and can make their own decisions whether to allow an entry or not. This decentralizes the access control process, allowing the controller panels to make programmed access decisions regardless of whether there is currently communication with the host computer.
In most cases, specific host or administration software must be used with specific access controller panels. This means that the same vendor’s software and access controller panels must be used within a single system. Credentials may possibly be used in a cross-platform situation, with the same card being programmed into two (or more) separate systems.
Communications between the access controller panels and the administrative computer(s) is typically carried over Ethernet, which allows for the remote connection of panels using WAN or Internet capabilities. Many older as well as some current panels provide connectivity via RS485, a protocol that provides up to 4,000 feet from the host computer to the remote panel. Some panels possess multiple communications protocols, leaving the communications options to the installing company.
Selection of access controller panels must include considerations of how many credentials a particular panel can store, and of what type (biometric information requires larger file storage space than an access card). Also, the CPU processing capability of the panel may affect how quickly the localized access decision is made, which can affect how quickly people can enter and leave controlled areas.
ACCESS SYSTEM TYPES
There are three broad categories of access control system types available today. Each type has its benefits and potential drawbacks.Entry systems– High-end intrusion alarm panels often include the option to control one or a few doors by connecting the door release, credential reader, door position switch, and REX to the alarm panel itself. This is often accomplished with an auxiliary circuit board purchased separately from the main alarm panel. This type of system can be considered for a limited number of controlled access points, provided that the installer takes into account the particular system’s limitations such as the number of users, the amount of stored access event data, and the overall capabilities of the system. With these systems the alarm panel functions as the access controller panel, so the cabling distances to the controlled door’s electronics must be within the device manufacturers’ specifications.
Mid-size systems– Using the access controller panel/host computer scenario, mid-sized systems are the most commonly used type in the market today. Individual controller panels can be connected to one or up to eight access-controlled doors, and the communications to the panels by the head-end host computer is handled via Ethernet or RS-485.
In these types of systems, the computer used to program the access controller panels is usually not dedicated to the access control function. Also, in most cases, the remote access controller panels will make their specific access decisions and store the transactions without necessarily reporting them to the host computer. To gain the access records for a specific date, time or reader, the user must turn on the access control host software and communicate with each controller, requesting a download of historical information.
These mid-sized systems are perfectly functional for typical access control scenarios. A potential drawback is the necessity of either providing a separate computer to run the host software, or installing the host software package onto one of the end user’s computers.
Enterprise-level systems– For multi-location and multi-host workstation applications, enterprise-level access control systems provide the pinnacle of sophistication and programming options. Utilizing one or more dedicated PCs, these systems can control multiple systems simultaneously, while also partitioning the control of the systems.
A key to enterprise-level systems is the real-time viewing and integration that can be performed on multiple systems at the same time. Usually the enterprise computer is in regular communication with the access controller panels, gathering access histories and verifying functionality. This real-time integration allows for the connection of CCTV devices such as DVRs, which can provide recorded video call-up of specific alarm events, credential presentations, or locations.
These systems also can be integrated with human resource department data, so that when a person is hired or fired, their access status can be quickly granted or denied. This attribute can also be utilized to provide a form of time/date attendance.
Another use for an enterprise-level system is integration of building automation or energy management functions, so that when a user presents a credential, the lights turn on and the temperature is adjusted in the accessed area. These functions can be provided using the I/O capability in the access controller panels, connecting the inputs and outputs into building management panels. Also, the I/O connections can be used to activate other devices, so that, for example, if an invalid credential is presented at one reader, an output on a separate access controller panel can be activated to trip an intrusion alarm.
WEB-BASED SYSTEMS
One of the primary issues with mid-sized and enterprise-level access systems is that the hosting software must be installed on either a shared or separate PC, which then must be maintained for software updates and integrity.A growing trend is the development of Web browser-based systems, where network-connected access controller panels can be accessed and manipulated by authorized users utilizing a universal Web browser software such as Internet Explorer. Each controller on the network is in essence a Web server. This type of system portents great benefits to installation companies, because no software need be installed or maintained on the end user’s PCs. If the access controller panels are connected to a LAN and configured for Internet access, system software updates can be performed remotely by the security dealer from his office. E-mail alerts of alarm and/or invalid credential presentation can be enabled, and it can be anticipated that the full spectrum of Internet communication, such as instant messaging, will also soon be available in these products. Web-based systems can be a single controller panel, or many spread across multiple buildings and locations.
Although Web-based systems provide many benefits, security integrators should anticipate that the successful installation of these systems will require detailed interfacing with the client’s IT department, who will need to allow their connection to the enterprise network, manipulate firewall settings, and provide Internet access if the controller needs to communicate over same.
Web-based access control systems will grow in usage, as their cost of ownership by the client’s IT department is very low, with no separate computers or software to maintain or update.
SDM acknowledges the technical assistance of Paul McKitrick and Cindy Bracey of Bosch Security Systems to this article.
Sidebar: Life Safety and the AHJ
It is very important for security companies to carefully consider the life safety implications of the installation of access control systems. The first concept to grasp is that while access into a building can be denied or controlled, the egress or ability to leave a building cannot be impeded or unduly delayed. If the building is on fire, people in the building must be able to leave quickly without fumbling for keys or access control credentials.In general, access control system installers must consider the following scenarios and issues:
- Can people within the building leave through designated Exit doors without using a key or card? It is likely that they might leave their purse or wallet at their desk in their haste to escape. Remember that an audible alarm can sound at the door when it’s opened, or the door opening may create an alarm condition on the access and/or intrusion detection system. But the person can still get out the door.
- Will controlled doors unlock or be locked when primary power fails to the building? Can people go through exit doors unimpeded during the power outage?
- What happens when the building fire alarm system is activated? In many cases, the local Authority Having Jurisdiction (AHJ) will require that door control devices such as magnetic locks be powered down when the fire alarm system has activated. This is accomplished by connecting an alarm output relay in the fire alarm panel to the magnetic lock power supply.
The specifications for life safety considerations of access control equipment are listed in various NFPA documents. The key to the proper design of access control life safety functions is to have a clear understanding of the particular AHJ’s requirements and his interpretation of national and local building codes. Receiving the AHJ’s approval prior to the start of an installation is the only correct procedure.


