
Use an existing IP network or install a new one to transmit your client’s alarm and video signals. Each method has its own considerations.
ENGEBRETSON: By using IP communications, a company can connect its alarm or video system over the same wide area connection used for its computer network, which means that geographically diverse systems can be integrated. This gives the company a single system to manage and can result in real savings in guard and monitoring costs.
SDM: What equipment is needed at the
central station and at the customer premises
to support communication via IP?
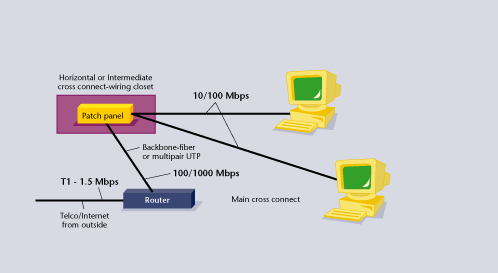
CHERNOY: There are several options available for making the connection at the protected premises, however today each still requires the same brand of equipment in the central station to match the units used in the field. Alarm controls are available with built-in IP, add-on IP or some have a patented device that plugs into the phone line jack of an existing non-IP panel and converts the phone dialing and signals to an IP signal. This IP output is then connected to an existing home or business network where the IP signals are routed (often through a firewall) and then onto the central station. These signals are received by an IP-connected central station receiver.
SDM: IP also can be used to transmit video images to a central station, guard booth or other remote location. How does that typically work? What equipment is needed at each end?
CHERNOY: Video signals are often stored in their entirety on-site and then retrieved remotely based on an alarm signal. This has created a big market for digital video recorders and storage systems. There are a number of firms providing remote “guard†service with always-on video feeds to the monitoring station. A single guard is often monitoring up to 36 video feeds with some type of alarm or motion indication to prioritize their attention. Most DVR makers provide some type of remote management software that runs on a standard computer at the central station.
ENGEBRETSON: Video systems that are to be installed and accessed over a client’s local area network (LAN) can be programmed to use the maximum allowable bandwidth without causing noticeable slowdown in enterprise data transmission. Connecting client sites over the Internet adds a “wild card.†Different connected buildings may have different types of connectivity, such as T-1, DSL, cable modem or dial-up. Each type of connection may require different equipment or configuration, and the quality and fps (frames per second) of each video stream may differ.
SDM: Often a customer already has an IP computer network. An alarm or video system can be connected to that network – or dealers can install an IP network just to support the alarm or video system. What are the pros and cons of those two options?
CHERNOY: Since the typical alarm application uses such a small amount of the available capacity of the network, most feel that you are better off sharing the existing network, because this means that it has a high priority for the business and will be well maintained. Not all networks are created equally, however, and it may be that the business does not have battery backup for all network components, or disconnects the network from the external world at various times for maintenance. Some IP managers insist that the security system be connected to a specific router or hub to ensure that messages can be transmitted in all instances. The biggest con of having dedicated IP equipment (other than cost) is that it is not often adopted by the local IT support team and the separate network has to be maintained by the security company separately from the corporate network.
SDM: What is involved when an alarm company needs to install a local area network at the customer’s premises? How long does it take and what does the installing company need to know to do the job?
CHERNOY: You can find all the parts you need at most hardware and office supply stores. While there are wiring guidelines for structured cabling, most of the wiring that is needed can be done with pre-molded cables in 5, 10, 25 or 50 foot lengths. You can pick up 4- or 8-port hubs with integral firewalls and routers for less than $100. If the network will be used solely for the security and video system it is really no more complicated than traditional wiring of similar components was in the past (many would say it is easier). There are a few things to be learned about IP addressing, router and firewall configuration, but since this is computer-industry standard information there are thousands of books and short courses, not to mention manufacturer’s guidebooks and manuals on the subject.
ENGEBRETSON: Knowledge of media converters, cabling distance limitations, and networking devices is needed to ensure that the complete system will provide the connections and bandwidth required to make the system functional. The dealer may also have to arrange connection to the Internet, VPN, or WAN to provide remote network functioning, viewing of video images, and storage of recorded video.
It’s very important to plan for protection against outside hackers and “inside†compromise of the security network components, software, and cabling. Securing any network against inside or outside electronic attack is not a simple, one step, lock-it-and-leave scenario. Securing the network is an ongoing process, using various security elements such as anti-virus software and employee screening. Network security needs to be managed, performed, and updated on a regular basis.
Physical security, such as door locks, access control and burglar alarm systems are a key part of protecting both the alarm and computer networks from attack. This is an aspect of network security that security dealers can readily provide.

CHERNOY: The alarm company needs to know how many devices (controls or video units) will be connected and where they will be connected. It needs to know what active (powered) devices are in the network and that the power for these devices is backed up. It needs to work with whoever assigns IP addresses and the dealer will need to make sure that the routers and firewalls in the system allow the messages from the security devices to exit the network to the outside world. Similarly, to allow remote control and programming there has to be a setting made to allow messages to enter and reach the security or video system.
ENGEBRETSON: Security dealers must have a thorough knowledge of networking, and particularly video bandwidth requirements, if they expect to convince the IT department that the installation of network cameras or video servers is a good thing. There are many ways to reduce the bandwidth requirements for the transmission of video images; the dealer needs to know how the proposed video products compress and transmit their images, and what options are available to achieve an acceptable bandwidth usage.
SDM: IP communicators can work over a variety of wide area connections, such as DSL, T-1, cable modems and others. That connection is often shared with the company’s computer network, even when there are separate alarm and computer networks on premises. What mechanisms are in place to ensure that the alarm signals get priority over that wide area connection?
CHERNOY: Depending on the capability of the router, firewall, and hub or switch, signals from a specific network connection can be given a higher priority. Since most security messages are small in comparison to other network traffic, there is usually very little delay.
ENGEBRETSON: IP networks are inherently “democratic,†with all properly connected and addressed devices being able to communicate with each other. While the signals generated by IP alarm transmitters and access control interfaces are relatively short and infrequent, video image transmission can be quite bandwidth-intensive.
Proper control of video bandwidth usage can allow for all network traffic, including enterprise, alarm, and video, to be delivered to their destinations within reasonable time frames.
