For many years, the card reader has been a given in an access control installation. First with proximity, then contactless smart cards, the technology has become so reliable and durable that it is easy to pick a reader, install it and move on. Potted, sealed and with no moving parts, readers rarely fail or cause trouble. Unless the user is adding doors or doing a complete card technology upgrade, once the reader is on the wall, it stays there for a very long time.
From a dealer’s or integrator’s point of view, this scenario doesn’t make for ongoing sales or revenue opportunity. Maintenance is almost nonexistent; and the sheer volume of card populations make wholesale changes a rare thing. But that doesn’t mean there is nothing to discuss with users when it comes to reader technology. If anything, the pace of technology advancements throughout the security industry make reader changes a certainty. And the challenge of figuring out how to either work with what is already on the wall, or plan for a daunting migration of card technologies is one that takes skill, forethought and a lot of preparation.
“It seems like technology is moving quicker and quicker,” says Aaron Barbe, product manager, Honeywell Security, Louisville, Ky. “There is always opportunity to stay on top of that and leverage it and make end users aware of the possibilities and technologies,” he adds.
“Our industry is driven by the end user,” says integrator Robert Carmichael, senior solutions engineer for the Southeast region, Securadyne Systems, Dallas. “As access evolves, so do we. That is where we see different levels of card reader technologies start to hit the market. No one I know of would change readers just to update to something newer unless there was something driving that.”
Glen Weston, director of field operations for Securadyne, agrees. “Readers stay around for a long time. Clients will migrate for a couple of reasons: The manufacturer stops producing them; they are locked into a technology with no growth plan; or they are trying to put more into technology. It really depends on what they are looking for. There has to be a driver.”
Still, many integrators understandably focus on the software side these days, because that is where so much is happening. If they do anything to the reader it is to install a multi-technology reader in an effort to “future proof” against upcoming technologies.
“We tend to upgrade more on the controller and software side first, due to the size of our customers,” says Ryan Waters, integrated security engineer, CSi, Allentown, Pa. “A lot of the new readers going in we are doing multi-credential. If we replace a reader, we tend to replace it with that to give them a more seamless transition.”
But is there more that could be said or done? Is there potential for recurring monthly revenue (RMR) or upgrades outside of the occasional call for a new reader or a long-term plan to slowly migrate from one technology to another?
Yes, says Dave Adams, senior director of product marketing for HID Global, Austin, Texas. “I think there is opportunity for them to create more business. Our readers are designed to last a lifetime. They are fully potted and can withstand quite a bit. But once you put it on a wall, is it still servicing the purpose for that customer or have their needs changed over time? Can that reader accommodate changes?”
There are a number of conversations security integrators can have with their customers about readers.
Lead With the Reader?
Most integrators don’t lead a conversation with the end user by talking about readers; maybe they should. One of the most basic choices about readers that often doesn’t merit much discussion is read range. Many manufacturers and integrators feel that “it is what it is,” and most users will automatically touch the reader anyway. But that is not always the case.
“It really boils down to choosing the right reader for the right application,” says Christopher Sincock, vice president, security business, DAQ Electronics LLC, Piscataway, N.J. “Most readers fall within whatever tech silo they are targeted at, and are designed to provide or accept different physical mounting requirements. A lot of times it affects price as well. If you ever see a mullion reader mounted on a wall, someone wanted to save $50. But there are trade-offs with that. It is designed to mount on a door mullion and there is reduced read range.
“End user expectations from proximity technologies they are used to is that they will be able to wave the card in front of the reader and it will work. Everyone has seen the ‘fanny swipe.’ Customers need to be aware that there will be trade-offs when they make the decision about which reader or technology to install.”
Smart card readers also come with reduced read range, due to FCC regulations. So when a user is upgrading from proximity to smart card (often a slow migration involving using both for a long time and a multi-technology reader), they need to understand that the proximity reader can be waved at, but the smart card reader might need to be touched.
Today’s new cars feature smart keys that can be kept in a pocket, similar to proximity technology — a convenience more users are being reminded of when it comes to access control, notes Russell Anderson, product trainer for ASSA ABLOY EMS & OEM Group, Phoenix.
“Maybe they want to move from a card to a fob they can keep in their pocket with their keys, or a wristband they can wear. Not all card readers can do that. But it is cool technology to have and it is everywhere now. It is a nice technology to be able to offer, especially if they have an older card reader technology.”
The industry has known for quite a while that proximity technology is less secure and can be hacked, but there hasn’t been enough of a reaction from users to motivate change. With last year’s widespread hacking incidents at Target and other stores, more and more stories in mainstream media and even a new TV series about cybercrimes, that awareness level is beginning to change.
“There are some customers who have been on proximity technology for ages that are finally saying ‘we can’t do this anymore. We must upgrade to a secure identity,’” Adams says. “That is where we are seeing big changes happening.
“I think some integrators are being very proactive in trying to move customers to new technology. But when these systems were put in, nobody forecasted out that they might have to budget for upgrade paths. We are now coming to a point where customers are realizing that they do have to put money into that budget. We are seeing more and upgrades happening. Integrators are doing their best to guide their customers in the right direction.”
But Anderson says there still needs to be more conversation about the security of technologies. “Basic proximity will let people in and out of a door. It depends on what security level is needed. There are a lot of different choices to explain. Sometimes the integrators are basically asking what the customer wants instead of explaining those options to make sure the customer is truly happy with what they are buying. It is really important. Access control is a huge decision for an organization to make and integrators need to sit down and have an in-depth conversation about what the customer is looking for.”
In some cases that still may be proximity and in others it may be something else. “We still see a lot of proximity with the lion’s share of installations,” says Bill Smoyer, Western regional sales manager, Access Hardware Supply, San Leandro, Calif. “But more and more facilities want a secured smart credential. In certain markets Bluetooth low energy (BLE) and near field communications (NFC) are becoming popular.”
Rick Focke, senior product manager, access control, Tyco Security Products, Westford, Mass., is surprised to still see proximity going in. “Really? Those are vulnerable. I think integrators need to do a little better job of putting out the different options. I think there is more to be done with the reader. We are all in the business to make money and it is easy to get it in and get the job up and running. But they might be short-changing the user if they don’t at least offer the option of smart cards instead of prox. Sometimes they don’t even ask the question.”
Many integrators take the approach of future-proofing whenever a new reader is added to an existing system, but this is an area that could use some fine-tuning, says Marcus Logan, senior manager of product marketing for Honeywell Security. “Proximity does have some inherent problems. Where security needs are higher and a smart reader would make sense, the integrators can’t always articulate it well enough. Prox has vulnerabilities and you should always look for that investment. There is definitely an opportunity for an upsell, but you need to understand the smart technology and really be able to articulate that well. Not all dealers have that capability.”
Another more secure technology experiencing a resurgence recently is biometrics, says Gary Jones, business unit director, MorphoTrak LLC, Anaheim, Calif. “We do see it as both a challenge and an opportunity, bearing in mind that the integrators are often the ones in an advisory role. There is no question there is a big opportunity gap there.”
Being able to clearly articulate why one technology might be better than another is especially critical when it comes to readers, where it is often on the integrator to convince the user to change from a perfectly useable and “fine” technology that is still working. Brushing up on some sales points to start the conversation can’t hurt.
“Future proofing is important but that is where a conversation really needs to take place,” Anderson says. “Some systems can do proximity and iClass at the same time. If they want to move that way you have to have the ability to do that. They may not want to do it right now. Maybe they don’t have the software capability to do it. It is definitely an option you should present to the customer. It’s important to explain the different types of card readers out there and let the customer make informed decisions about the product they think will be best for them based on their security needs and the cost associated with those needs.”
This is something integrator John Krumme, president and CEO, Cam-Dex Security Corp., Kansas City, Kan. is well aware of. “We like to present the return on investment of using a dual-technology reader and what it can do for the customer. They can move forward with a much safer technology by using a smart card instead of a 25-year-old technology. Many times we are using a dual-tech reader for an existing building.”
When the Reader Is Already There
For most integrators the opportunity to do “green field” projects is rare. Many reader installations will be part of an ongoing process over long periods of time. And in many cases, the integrator who is called to replace or add readers wasn’t the one who originated the project. Depending on what is being done, this can present a host of challenges for the integrator.
“You have to identify what you are working with,” Smoyer says. “With a keypad or proximity or even biometrics you need to determine whether it is a component of a system or actually performs as a system. The first step is to find out what you have. In this day and age of smart phones and mobile technology you can have a wealth of information out there in the field to do that troubleshooting.”
Knowing what is there is important, Adams says. “One integrator might put a reader on the wall and configure it a certain way, then five years later another integrator wins the maintenance contract. They don’t know how that reader is configured.”
Most of the time finding out what is there involves pulling the reader off the wall and looking at the specific model number, then either looking it up or contacting a manufacturer or distributor to find out how it will work with the changes you are trying to make.
“If it is an HID reader, the part number will tell us what that reader is capable of,” Adams says. “In the near feature there will be an app on the phone and they will just have to put it up to the reader to see how it is configured.” This app is in development and should be available within the year, he describes.
“It is critical to match up the reader with the cards,” Focke says. “So many times users want reuse cards and/or readers and a lot of effort needs to be put in up front to make sure the card/reader/panel combination works in the field.”
For example, when migrating a card population from proximity to smart cards, there may be instances where you have both a dual-technology reader and dual-technology card and you end up with misreads. The solution is to set the reader to one or the other technology to make it more efficient.
Or as smart card systems themselves age, some of the early adopters may have card or reader technology that is not compatible with the newer systems out there. “How do I know what that reader is capable of? There are so many card technologies out there now,” Adams says. “The days of having a closed system that only reads proximity are over. Most readers put out in the field today have the capability to read two or even three technologies simultaneously and knowing what those are can be tricky.”
It is important when setting up multi-technology readers to carefully consider the card population, he adds, because you can set up the reader to be more efficient for the bulk of users.
“If you have a card population that is two-thirds iClass and one-third Desfire, you can set the reader to read the iClass cards first,” Adams says. “It will do it serially and read the most populous cards first, so they get the best experience from the reader. You could see a noticeable difference between the card read speed of maybe a second. People do notice those things.”
When it comes to smart readers, if you don’t know what you have and how it is reading the card, you could even end up with a security issue that will make the card read even less secure than prox, Logan says. “There are encryption keys on the secure portion of the card, but the reader has to know that key and it has to be embedded.”
Matching the credential to the reader is what gives that secure read, which is a problem if you aren’t sure what you have, Barbe adds. “When you source components from different manufacturers and put them all together that is where you can get unsecure readers. We need to do a better job of getting that awareness out there. There is a lot of Mifare and Desfire technology using those unsecure reads unknowingly. It is different than proximity where you had one number. Smart cards have multiple. To be 100 percent sure you have to go an extra level down and understand what the firmware revision is and the formatting on the credential. The easiest way is for the dealer to take a picture of the back of the reader, the firmware and build date.”
Card and reader compatibility can trip up the integrator, says Charlie Thiel, general manager for CSi. “We have had problems where we had actually put in a multi-class reader and it was a takeover situation and we didn’t have all the information about the card. They were also using a multi-tech credential that had a customized prox portion of the card so when they held it a certain way it would read the wrong number. Just from testing enough, we determined the problem.”
Legacy situations can be tricky but are also incredibly common in the reader area, Jones says. “Legacy deployment impacts choosing new readers. It’s extremely rare to have a green field installation. Even with new construction they most often have cards they already have. The integrator needs to validate the cards. As long as they can tell the reader where to look for the data it needs, it will be fine.”
Beyond Future Proofing — What’s Next?
For years integrators have been optimistically installing readers that can handle two or more card technologies with the idea that the customer could upgrade to the new technology as budgets allowed. This future-proofing makes sense, but hasn’t necessarily led customers to flock quickly to new technologies.
Access control is not a fast-moving industry, but several factors are converging in the past few years to add up to changes that might just motivate reader changes — bringing with it more opportunities for the integrator.
“It is a combination of ‘cool technology’ and higher security,” Adams says. “Mobile credentials have been a great push to get people off the pot. We have been talking about hacks now for quite some time, but we still have people buying prox. They don’t care about the security. But the mobile is cool and suddenly everyone is talking about it. When the people carrying the card start complaining that they should be able to use their phone, now we have a force that can move a market because the actual card holder is pressuring the company to say ‘let’s get modern.’”
Mobile credentials based on NFC frequently use the same technology as smart cards, just in a different format, so anyone who has installed or is geared up to handle smart credentials can easily use mobile as well. BLE, however, requires a change to the reader.
Reader manufacturers such as HID understand the desire to leave a reader on the wall, so unless a customer is changing from proximity to something else, many smart readers can be adapted to handle Bluetooth and beyond. “We are designing readers today with a modular concept to be able to add Bluetooth to them or add new radios to an existing reader to allow you to use these technologies,” Adams says.
Krumme feels mobile credentials could eventually be a game changer, particularly for proximity. “When you can have an encrypted signal as an app on a smart phone that you can present from 20 feet away, that is what will change people’s attitudes about the card readers that have been on their walls for 15 years. Those old readers have been hacked. There will be upgrades to people’s buildings and card readers will be changed out because of that. The millennials all carry smartphones.”
Readers are also getting smarter. Many readers today offer two-way communications. An early but influential trend is the Open Supervised Device Protocol (OSDP). “The whole Wiegand standard is finally starting to go away,” Focke says. “It will be a long road because there is so much installed base, but there is a movement towards two-way protocol between the reader and panel. Changing the readers involves money. It is not a Tsunami yet but we do see activity. It is up to us to educate the customers.”
These two-way and modular readers have an extra benefit for the integrator — they will involve potential interactions and firmware upgrades after the installation, leading to RMR.
“Manufacturers are starting to adopt OSDP protocol with bi-directional communication,” Waters says. “We do a lot of remote monitoring and this gives us the ability to monitor more things, get more information from the reader and be more proactive in servicing our customers.”
Thiel adds, “We can’t really monitor card readers themselves now, but OSDP will allow that in the future. That would be something useful for a company like ours.”
Adams says if an integrator isn’t familiar with OSDP yet, it is time to start educating themselves on how to work with it. “If you are an integrator you had better get up to speed on it. Although it has been around for a while, OSDP is currently making significant strides forward and I think that integrators really need to understand how to install a reader with OSDP. There are so many things that benefit the integrator like upgrading the firmware or changing configurations with the click of a button.”
SIDEBAR: 7 Tips for Installation & Troubleshooting
While readers are generally very reliable, things do occasionally go wrong. Very rarely is it the reader itself causing the problem, but when it is, most mistakes happen in the beginning of the project at the installation itself. Here are seven “refresher” tips for a clean installation:
- Proper mounting.“The material the reader is being mounted on matters,” says Gary Staley, national sales director, RS2 Technologies, Munster, Ind. For example, if a proximity reader is mounted on metal it reduces the read range. “Often you will find card readers mounted too close together and that can cause cross-talk and read issues,” he adds.
- Cabling. “The trouble installers get into with readers has to do with the wrong type of cable,” says Christopher Sincock of DAQ Electronics. “Everything is impacted by voltage drop. Wire gauge is important. The shielding is important for the cable. Most installation sheets tell you to use shielded cable.”
- Glen Weston of Securadyne Systems, has even seen telephone cable used as a conductor for readers. “It will work for a while, but it doesn’t have enough to push through the voltage.”
- Wiring.John Krumme of Cam-Dex Security Corp. says the first thing he looks for in a troubleshooting situation is a cable or wiring problem. “We don’t see as many issues with card reader installations, but we do on the back side. The reader cable is terminated at the panel. We use a wire way system to properly manage that so it is neat, clean and documented instead of a bird’s nest of wire.”
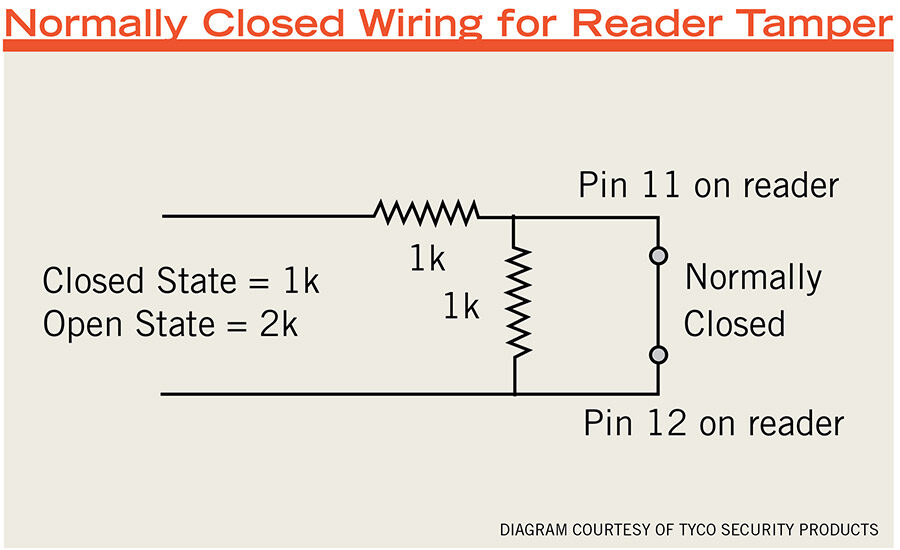
- Tamper switches.Rick Focke at Tyco Security Products recommends always using tamper switches on Wiegand protocol readers. The newer ones may have them built in, but in the Wiegand world there are a separate set of wires to set the tamper alarm. “It may cost a little more money to do the tamper. If they are reusing wiring it could get expensive, but even if the customer doesn’t want it right now, I would suggest it anyway.”
- Proper termination. “When you have a controller for several doors, make sure at the end of the loop everything is properly terminated and grounded,” suggests Pasquale Rocca, team lead technical support for access control, Genetec Inc., Montreal. “Cables running too close together can run interference.”
- Testing. “I can’t stress enough knowing the product you are dealing with,” Weston says. “Make sure you read the installation instructions, use the proper voltage and cabling. Pay attention to the environment. You don’t want to put it where it will limit the frequency and read range. Have a test bed area and test all the readers to make sure you don’t have any failures.”
- Good design. “We go through an engineering process up front,” says Charlie Thiel, of CSi. “It has to work on paper. That is something we strive for: Trying to avoid those pitfalls in the installation and mitigating potential problems makes for a more profitable job and a satisfied customer.”