Having all the most sophisticated security technology inside a building is important; but a more ideal situation is controlling who enters, and thereby eliminating threats before they even get on premises. One of the most effective tools for doing that is a good intercom system that allows operators, either on location or in a central station, to truly interact with visitors trying to gain access by seeing and speaking with them.
A good intercom provides users with all the information they need to make informed decisions about which visitors to allow inside a facility, says Bruce Czerwinski, U.S. general sales manager, Aiphone Corp., Redmond, Wash. “The units provide two-way voice and video, allowing users to take control of their entries and maintain a higher level of security. These systems also work well protecting critical indoor entries.”
Brad Anderson, U.S. national sales manager, Commend USA, Mahwah, N.J., describes a model of a “concentric ring” in which all communications should be considered. “When securing a facility you begin at the proverbial fence line,” Anderson says. “So between that line/ring there may be a number of traps or sensors —for example, access control at gates, video and video analytics, motion detectors, and license plate recognition. All or part of these may be in play before someone gets to a door or gate where you would find an intercom.” He says that any help points in the area leading up to the entry should be considered as outbound devices for calling, along with inbound calling.
How big a piece of the overall security plan the actual intercom should be really depends on the business or what the opportunity is, says Ryan Gregory, director, new systems and solutions, Axis Communications, Chelmsford, Mass. “In education it could be used for door entry into buildings, into dorms, unattended deliveries at night, or maybe in a warehouse door out back,” Gregory says, adding that most intercoms on the market have relay control so operators can use them to open and close doors or electric strikes.
THE SHIFT TO IP
This focus on communication works hand-in-hand with the recent shift in technology toward IP.
“We’re seeing a large shift toward VoIP for access control and door intercoms,” says Bill Heideman, CEO, Viking Electronics Inc., Hudson, Wis. “We’re still selling and supporting analog systems, but it’s easy to see why VoIP devices represent the future of access control and intercoms. A VoIP door intercom can be connected directly to the organization’s compatible IP-PBX using SIP protocol, or through an inexpensive, cloud-based VoIP fee-based provider. VoIP services like Callcentric or VoIP.ms cost as little as $0.85 per month and $0.01 per minute. So a small to medium-sized business can install VoIP access control devices without an IP-PBX and pay just a few dollars per month.”
This shift toward IP has also allowed technologies such as useable video to be implemented into intercoms and door stations. In the past, the audio and push-to-talk was the main business case, Gregory says; and while video has been put into those intercoms before, it isn’t what we have today. “We’ve taken a lot of our imaging quality — whether it’s wide dynamic range, dynamic capture or forensic capture — that has made its way into our intercoms, so that you have very good video in all lighting conditions.”
Gregory says other technologies such as Axis Zipstream and H264 are in these products as well, and they are helping with the management and overall storage of larger amounts of data. Additionally, newer technologies such as noise filtering are making these products more effective. “If you look at the door station [Axis] came up with a couple years ago, that’s got a couple different types of intelligent noise filtering where we’ve actually got video of a guy holding a chainsaw right next to it, and you can still clearly hear the person speaking into the intercom.”
Voice over IP also allows for session initiation protocol (SIP), which “almost makes your door station act like a telephone — once it’s set up and configured, you could literally pick up the Cisco IP phone on your desk and it would ring the intercom out there,” Gregory says. He adds this technology gives users flexibility in routing calls and having different groups, or setting it up so that certain events can trigger certain responses.
UNIFIED COMMUNICATIONS
Used effectively, Anderson says, these IP-connected technologies could result in a reduction of workforce and increased efficiency and customer service. He also points out the benefit of unified communications, offering as an example a recent trip to a hospital in a large city. “I parked in the lower level of the parking garage. Here are the different communication devices I personally observed in place: 1. parking garage wall; 2. parking elevator; 3. open space blue lights; 4. door intercom; 5. phone system at reception; 6. overhead paging; 7. elevator in the hospital; 8. dental department intercom; 9. surgery department intercom; and 10. the radios used by security and operations.” All these devices work together to form the concentric ring, Anderson described.
The key to driving this unification of communication, Anderson says, is understanding how long it takes to communicate with the entire organization during an all hazards event. “We now ask in our meetings how long it takes to make an emergency announcement to all on a campus during an all hazards event. When things happen in seconds, minutes are too long. The idea of buying and deploying disparate systems that are not interconnected is over.”
This necessity to communicate quickly is precipitated in part by current events. Heideman says some drivers that companies cite for adding intercoms are vandalism, a violent workplace incident or a recent entry attempt by a terminated employee or ex-partner, and an uptick in criminal activity in the area. “Sales of access control devices and door box intercoms equipped with integral video cameras are on the rise,” Heideman says. “Organizations are employing the devices to help with visitor identification and to provide surveillance.”
FINDING THE RIGHT FIT
Intercoms are not a one-size-fits-all technology, however. In order to design the right overall security system implementing intercoms, integrators must understand what the customer’s main objective is in installing it, Anderson says. “Why is it even there? Stopping the bad guy? Mitigation of risk? Or something as simple as reducing costs. If you look at the parking industry they are very advanced in how they handle and manage access and payments using a centralized approach to handling intercom calls.” (See sidebar “Centralizing Intercoms” page 82.)
Locking the outside doors is the first step to secure a building, Czerwinski says, and video intercoms will help employees make informed decisions about visitors requesting entry. But, he warns, any employee with the ability to access the system needs to understand and follow procedures before unlocking the door. “One of the biggest concerns of this technology is that employees won’t follow established organizational security procedures and unlock doors without fully establishing a visitor’s identity and/or reason to enter.”
To avoid this pitfall, integrators can provide training for the system — including the app — so employees feel confident using it. “An integrator may also help set up security protocols to ensure employees carefully identify visitors and their reasons for entry into the facility,” Czerwinski says. “If there is any doubt about a request, it should be transferred to corporate security to handle or, in more extreme circumstances, first responders should be called to investigate. It’s important every organization has clear guidelines.”
Anderson agrees, adding, “Without emergency operations planning or incident action plans, no technology, intercoms, video, access control, bollards, will stop anything. Planning, training and drilling are a must.”
In order to help customers get the most out of their intercoms, Anderson offers the following questions integrators should ask: 1. What is the why — to control entry? To reduce costs? To provide greater efficiency? 2. Are you looking for an outcome based solution? And 3. Will this be a part of a targeted risk mitigation?
“Knowing the why is everything,” Anderson says. Different customers will have different challenges, and may have different mandates they must comply with as well, and it is the integrator’s job to find these things out. For example, he says, there are several laws and statutes that are applicable in these areas that many integrators are not even aware of, such as OSHA-3148, OSHA-3152, the General Duty Clause, the Clery Act, and the Interagency Security Committee’s shooter mandates and best practices. Knowing these laws and statutes is a must before any planning and designing even begins.
Intercoms, when designed and executed correctly, can be one of the most effective methods of deterring violent or unwanted situations, from a disgruntled ex-employee entering a building to a noncustodial parent trying to pick up a child from school, Czerwinski says.
And while no technology can stop all crime, Anderson concedes, it will mitigate risk, adding Winston Churchill’s words: “Let our advance worrying become advance thinking and planning.”
Helping Customers Prevent Violent Incidents
Experienced integrators already know which questions to ask to evaluate the theft-risk profile and design a system to protect inventory, data and assets. But many small to medium-sized businesses and organizations have never conducted a risk assessment for workplace violence, mass shooting or terrorist attack.
As a first step, integrators should ask if the business or organization has a written workplace violence protection plan — many states require one. The plans encourage employees to report any safety issues that could result in injury, as well as troubling coworker behavior, including threats and verbal aggression.
The plans assign responsibility to specific management team members and detail steps to be taken for each type of issue. Most plans also include requirements for documenting the initial report and each protective step taken, along with dates and times of notices to police and human resources. Integrators should examine the plan and review the documented history to evaluate whether past actions are consistent with current industry practices and area threat levels.
Specifically, integrators should ask what actions the plan specifies for reports of:
- changes in coworker behavior;
- verbal or written threats against coworkers or management;
- notification of an employee relationship breakup in which the employee has a reasonable fear of harm in the workplace; and
- notification of a restraining order against an ex-partner or coworker.
These notices require proactive actions by the employer, including a violence assessment, increased supervision and increased access control. If the organization doesn’t have perimeter access control, the integrator should propose the development of a contingency plan that could be implemented on an emergency basis if needed.
Next, the integrator should ask about plans for future expansion, building modifications or upgrades and any planned force reductions or expansion.
Finally, the integrator should ask about recent assaults, vandalism, robbery or burglaries in or near the area. Evidence of such incidents may require the installation of surveillance equipment and additional lighting. — Contributed by Bill Heideman, CEO, Viking Electronics Inc., Hudson, Wis.
Centralizing Intercoms
As intercoms increasingly migrate to IP, companies are able to reduce workforces while adding features and flexibility to their door stations and intercoms they previously didn’t have when an onsite operator was required.
The practice of someone residing in the building where the intercom is attached is long gone, says Brad Anderson, Commend USA. “Central stations, security operations centers (SOC), etc. are used to manage access control, video, burglar alarms and now intercom calls. I work with many worldwide organizations that have been reducing their SOCs and using a more regional or centralized approach very effectively.”
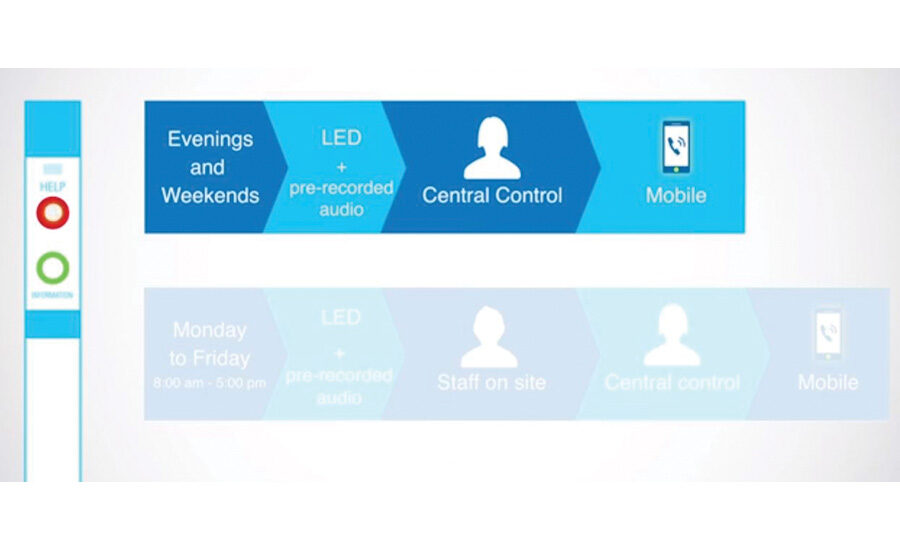
Commend USA, for example, offers what it calls SIP stations with intelligence. These stations have built-in smart action sequences, timed events based on time of day and dates, and call forwarding. The intercoms can be programmed to follow a certain sequence Monday through Friday during business hours that includes a pre-recorded audio message, then a call to onsite staff members, then to a central station, and finally to a smartphone. On evenings and weekends, the intercom would skip the onsite staff and go directly to the central station and then to a smartphone.
In fact, Bruce Czerwinski, U.S., Aiphone Corp., calls apps the biggest trend in entry controls/intercom systems. “End users must be able to maintain complete entry security if they need to leave their desks and the system’s master station. A smartphone app allows an employee to move about and still see and speak with a visitor before unlocking a door. Employers like the added productivity and convenience that apps provide employees.”
The applications for these types of connected intercoms are unlimited; allowing access to a delivery person after hours is only the beginning.
MORE ONLINE
For more on door stations and intercoms, visit SDM’s website where you will find the following articles:
“Entry Control’s Expanding Role in the Connected Environment”
“A Sound Opportunity: Residential Intercoms & Audio Systems Bounce Back Along With Construction”