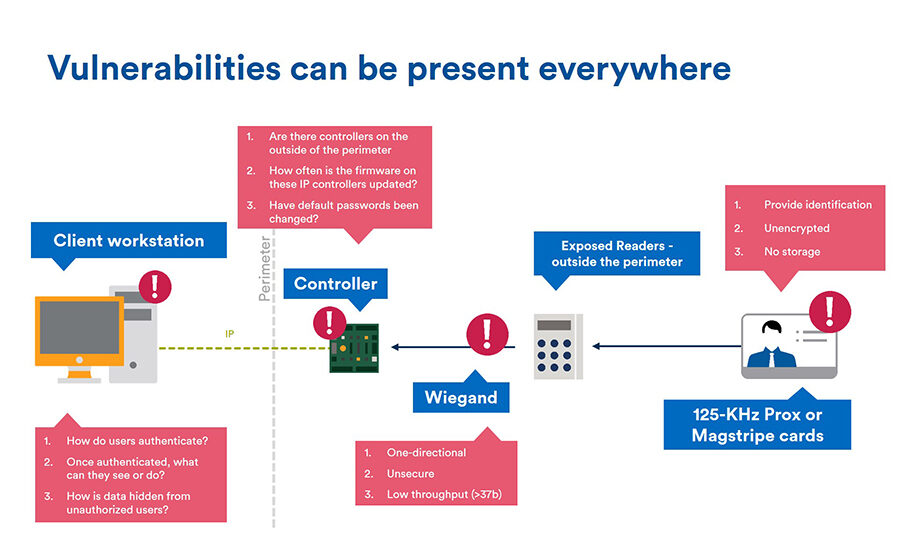
If you don’t think cyber security is an issue today you are dead wrong. But even if you think you are on top of things, chances are you — or your customers — still harbor some misconceptions, particularly when it comes to access control systems.
According to Terry Gold, founder of D6 Research, a research and consulting company dedicated to cyber security and the physical security industry, there is still a lot the security industry gets wrong, particularly when it comes to understanding actual hackers and their motivations and methods. (See online exclusive, “Think Like a Hacker to Better Understand Cyber Security.”) But he has seen promising movement.
“D6 Research has been seeing a slow but progressive change in sentiment over the past couple of years,” he says. “I sense a movement where 2018 is the year of the security industry to reach consensus that it’s no longer acceptable to be dismissive of cyber security.”
It is a progression, agrees Bill Bozeman, CPP, president and CEO, PSA Security Network, Westminster, Colo. “Originally when we started on our soapbox, it was denial. Now we are past that stage, which is good…. Everyone became aware simultaneously that this is an issue and now it is in the action level. We have gone from denial to awareness to action. We are much better off now than two years ago.”
Despite this, there is still a perception in the security industry that access control is somehow a little less at risk — and that is just not true, say the experts.
“Access control is generally one portion of an organization’s comprehensive protection plan that incorporates additional pieces, such as fire, intrusion, video surveillance and video management, to name a few,” says Eric Widlitz, vice president, North America sales, Vanderbilt, Parsippany, N.J. “However, the safety of a business is only as strong as its weakest link.”
Let’s take a look at some of the top misconceptions, with some advice for each.
1. Access control is not as vulnerable as some of the other security systems
Many people have this impression, but while it may seem that way, it’s simply not the case.
Ryan Zatolokin, business development manager, senior technologist, Axis Communications Inc., Chelmsford, Mass., says in some ways access control systems can even be more vulnerable because video systems historically get changed out for newer models more frequently than access control systems. “It is a misconception that video is more at risk. All networked devices are at risk…. Not one is inherently more at risk than the other. The concerns with access control are the same as with video — those older systems that aren’t maintained. [But] there are legacy access control systems running today that may have a Windows 95 box actually controlling a board in the closet. That to me is scary.”
Legacy systems are very vulnerable, says Matt Barnette, president, Mercury Security, part of HID Global, Long Beach, Calif. “All of these panels are network devices so by default if you are installing it on the network you are potentially opening up a gateway for someone to hack in.”
Pick the Right Partners — & Be One
When it comes to making sure access systems are as secure as possible, start by finding the right manufacturing partners, says Mercury’s Matt Barnette. “Make sure you are partnering with companies that are taking it seriously and providing you not only with products, but knowledge on how to secure them.”
Farpointe provides cyber security tools such as vulnerability checklists, but it goes beyond that, says Scott Lindley, president, Farpointe Data, Sunnyvale, Calif. “Farpointe Data sees its most important challenge as helping integrators stay in compliance with cyber security law. For instance, the FTC has decided it will hold the business community responsible for failing to implement good cyber practices and is now filing lawsuits against those that don’t.”
Several manufacturers today provide penetration test results as well as offer cyber-hardening guides and other documents on how to install their products in a cyber-hardened way.
But Northland Controls’ Henry Hoyne also cautions integrators to do their own due-diligence when picking products and manufacturers. “People think something is secure because the manufacturer says so, as opposed to asking for whitepapers and independent penetration tests. It is simple for any manufacturer to conduct their own pen test and possibly misrepresent their findings.”
D6’s Terry Gold agrees. “Revamp how you generally accept information and assertions made by manufacturers. Raise the bar for them to provide information that validates their claims. Trusting them is not the same as trusting their claims about their product. From a cyber security standpoint of your customer, you’re accountable for the latter.”
But it is definitely a two-way street, Barnette says. “We have taken a number of steps that include paying for third-party independent testing.… But just because we put features into a product, those still have to be enabled when installed on a customer’s site. Installers need to know how to turn on certain features and configure them on a customer’s network. Otherwise they can be an open door for a hacker to get through if the products being installed aren’t protected.”Even that might not be enough, Gold cautions. “One of the biggest misconceptions is that cyber security is primarily about network security. This is only one aspect; there are many others not even related that can undermine everything. Even if a network is completely secure, once someone gets in, then what? Strategy needs to have depth in so many areas. Attackers know this.”
Derek Arcuri, product marketing manager, Genetec Inc., Montreal, agrees. “We hear people saying, ‘So what if someone hacks my IP connected lights or HVAC? They will make my lights turn off? Big deal.’ It is a big misconception that the technology in question is the only victim. In reality it is everything that is connected to that system. Think of the entire network in terms of every single server or edge device that comes in contact with that access control system.”
Access control has been an afterthought, but that is changing, says integrator Colin DePree, sales manager, Pro-Tec Design, Minnetonka, Minn. “We are a lot further along on cyber security from the video platform perspective, but now we are starting to see OSDP and cloud-based access platforms that are forcing us to understand cyber hygiene and having those conversations [on the access control side].”
2. It is mainly someone else’s problem.
Cyber security is not a one-stop problem/solution. “Both end users and integrators tend to think it is someone else’s problem,” Zatolokin says. “They might think IT is taking care of it, or the security department is taking care of it. Often there is just not enough communication around this.”
Have the Right Conversations
Axis Communications’ Ryan Zatolokin advises integrators to go in asking the right questions. “Ask the customer, ‘Do you have an IT department? How involved are they? Do you have an IT policy? Does it have to be applied to the access control system?’”
This is both a priority and a challenge for Northland Controls’ Henry Hoyne. “When it comes to the clients, sometimes the biggest problem is not getting to the IT group early enough.”
Pro-Tec Design’s Colin DePree agrees. “If we are not dealing with the IT team at the time of sale, we require and mandate that we have access to them. We need to communicate that these are the devices, here is what the network looks like and the data that will be going across it.”
When it comes to talking to end users, the more specific the better, says D6’s Terry Gold. “Have each client define their cyber security goals. Avoid generalizations like ‘high security’ because this is subjective. Instead, define them by outcomes and results, such as specific scenarios that will be prevented.”
The integrator’s role in the cyber security equation is often to be the conduit between the manufacturer and end user, ensuring that both hardware and firmware are kept up to date, and working closely with the end user to plan ahead for future purchases toward their ultimate cyber security goal.
This includes the integrator taking on the role of ensuring that updates occur, Widlitz says. “You can’t simply install a solution, then walk away. It’s important to educate the customer on the possible vulnerabilities that exist within any system and the proper protocols needed to continuously update the software and firmware to avoid such threats.”
DePree adds, “We believe updating firmware is the single biggest thing our industry can do; but sometimes we are not doing it because the client is pushing back. Five years ago firmware updates had to be something new to get value. Now those are just as important to fix any bugs, leaks and vulnerabilities.”
Legacy access control systems, in particular, are a place where integrators really need to step up, PSA’s Bill Bozeman adds. “Be on top of the latest changes and upgrades in software, and make sure the end user is up to speed. It is their responsibility to bring it to the attention of the end user and the manufacturers to provide it.”Sometimes it is a matter of not knowing what you don’t know, DePree says. “There can be a lack of urgency or knowledge of what we can do and how we can improve. Sometimes it is an over-reliance on the manufacturers, thinking it is their equipment so it is their responsibility. In reality it is all of our responsibility.”
DePree adds that the real problem is communication. “There is a partnership needed between the customer, the integrator and the manufacturer. If every single one is doing their part in cyber security, it can work. But if the manufacturer says they are doing their part yet they are not communicating or teaching or training the integrator on what they should be doing; or the integrator says they know about cyber and they put the best-rated access control system on, but don’t know what settings they should be using; or on the customer side they say they are just putting access control in and their network is secure, then all three think they are doing a good job, but in reality there has to be continuity and communication through all three of those layers. It has to be a cooperative effort.”
3.Cyber security is too complicated — or too simple.
Many security integrators are so overwhelmed by the issue of cyber security they truly don’t know where to start; while others see it as a problem that can be “fixed.” Although there is no doubt that the issue of cyber security is real and complex, there are always ways to tackle tough issues.
Start Somewhere
It is a very old saying, but, How do you eat an elephant? One bite at a time. The best advice on where to start is to start somewhere.
PSA’s Bill Bozeman advises starting with insurance — but not just any insurance. “It is unlikely it will come from an existing provider because it is rare that their offering will be adequate. We recommend our integrators go to a specialist that really understands.” (See “When All Else Fails— Why Cyber Liability Insurance Matters,” exclusively online at: www.SDMmag.com/why-cyberliability-insurance-matters .)
Simultaneously he suggests picking someone and putting them in charge of the effort. “Someone needs to take responsibility; someone needs to be in charge who wants to study the problems, go to the sessions, and get their arms around the issue for their company.”
Bozeman describes a three-step process for any company: “Look inward, then look to the customer, then look for opportunity.”
While this is good advice, Henry Hoyne of Northland Controls also cautions integrators to get to the point as quickly as possible where someone in the organization specializes in cyber knowledge. “It is unrealistic to assume your current IT team has the ability to address all things cyber. That requires specialized knowledge.”
Genetec’s Derek Arcuri suggests integrators settle in for the long haul and prepare to grow the solution over time, while making sure not to overdo it. For example, air-gapped networks are a good start, but they aren’t enough. Yet there is a danger of also going the other direction and doing too much.
“You don’t want to over-complicate it to the point you can’t keep up,” he says. “You can’t over-secure your network if you can’t maintain that philosophy. For example, you could segregate the network and secure everything in the architecture; then a few years later a younger manager takes over IT, decides it looks so complex and cleans it up. All of a sudden a waiting virus is introduced.”
Terry Gold of D6 doesn’t sugar coat anything, saying that cyber security is extremely complicated and many in the security industry don’t yet have an idea of how secure they really need to be. However, he notes that the security industry is not a pioneer in the wilderness.
“The good news is that there’s much to learn from the journey that IT went through starting 20 years ago. One of those lessons is that security is a set of principles and practices, not a product or specification. So the journey for any organization needs to start there, then translate that into physical security.”
“Sometimes people want something that will solve all their problems,” Zatolokin says. They want some specific magical feature that will make that system secure or a magic box you can put on a network to make it secure.” He has also seen the opposite reaction.
“When I talk to IT background people it is a short, concise conversation. If not, it could be a sky-is-falling conversation. Every risk can be mitigated.”
Widlitz says, “With cyber security, you must act everyday. It is not something where you can say, ‘We’re safe; we’re secure; let’s forget about it.’”
More Online
Business insurance and other forms of insurance are nothing new to most organizations. However, as risks have evolved into the cyber sphere, insurance policies and products have too. Today, there are over 100 insurance companies worldwide offering cyber liability insurance, which helps to absorb the risks for their customers who experience a breach. In fact, Hart Brown, a leading cyber security expert, estimates the global market value for written cyber liability policies to be around $2.5 billion. Yet, insurance providers such as Allianz predict that this figure could reach $20 billion by 2025.
There’s reason for this growing demand. Cyber liability insurance helps mitigate risk and uncertainty. In the event of a security breach at a client site, cyber liability insurance will give integrators peace of mind. The systems integrator company will be able to access funds to manage response and keep the business running.
Learn more in the article “When All Else Fails— Why Cyber Liability Insurance Matters,” exclusively online at: www.SDMmag.com/why-cyber-liability-insurance-matters.
Think Like a Hacker to Better Understand Cyber Security
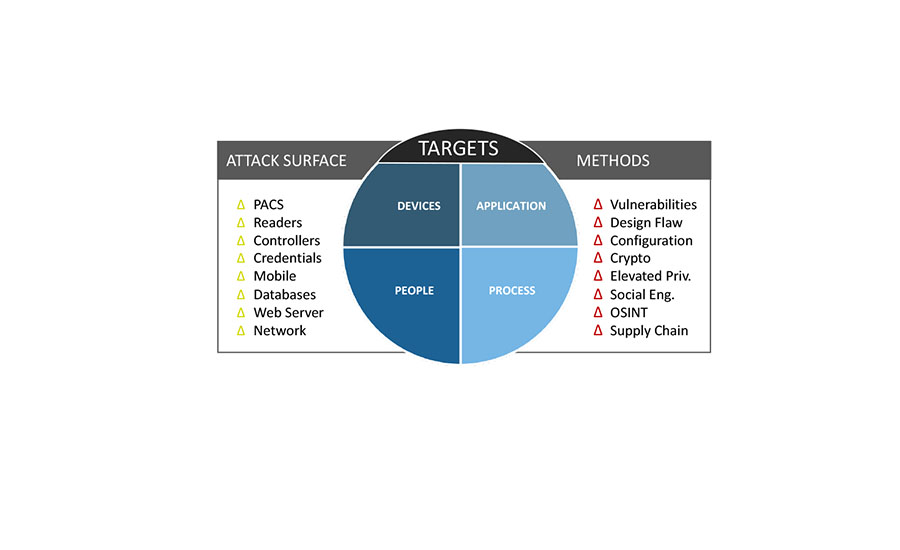
Breaches reported in the news only provide us with the simplified version. While appropriate for public consumption, it’s misleading for security practitioners to use them as the basis for actually understanding how attacks — and attackers — operate.
First, the most common misconception is that attackers go directly after their target and must compromise the network as a prerequisite. It’s a dangerous assumption, because it creates a false sense that certain applications are less desirable, out of scope, and safe.
The reality is that attacks are generally more dynamic, and hackers are pretty neutral about where they get access and how they get to their target. What might seem irrelevant (or secure) to an industry professional brings a smile to a hacker’s face.
D6 Research has built physical security threat models that incorporate thousands of combinations of how physical security can exploited. The vast majority of attacks start somewhere innocuous and end up with a major impact. An attacker can easily get onto an air-gapped network by exploiting a device, service, person, or process that the network already trusts. From there, attackers can not only figure out what else is connected to the network, but locate specific servers and gain their trust.
Ultimately, by using various techniques in their arsenal, they will elevate their role and permissions and make changes that industry systems aren’t designed to detect — and, in many cases, not even log. From here, they can start creating new users, changing records such as photos, pushing out support for new card formats or even decreasing security at the access point. It’s pretty endless, fairly common, increasingly well understood by hackers — but off the radar for security professionals. — By Terry Gold, Founder, D6 Research. For more on this topic see this D6 Whitepaper at www.d6research.com/cyberwp