
A physical security information management system can allow easy tracking of an object, such as a person, vehicle or asset as it moves through a network of security and surveillance cameras.
The abundance of inexpensive digital security cameras, NVRs, access control devices, alarms, sensors and more that security dealers and systems integrators are selling to their customers are adding to the customer’s data fire hose, compounding the data management challenge of today’s security-conscious organization.
Rising to meet this challenge is physical security information management (PSIM). It is the coordination of security and surveillance applications by a situation management system, thereby providing a single point of aggregation, assessment and recommended response for all security-related information.
A PSIM solution correlates security and surveillance data from multiple devices to isolate and identify significant events. It also delivers intuitive access to live and recorded video to support immediate investigation of security alerts.
Additionally, such a system can recommend actions that should be taken and provide controlled sharing of important information across users and devices. In short, it enables security personnel to manage situations or events instead of the underlying systems and technology.
4A International projects the overall security technologies market will reach approximately $70 billion globally, rising 15 percent annually. These technologies include video surveillance, detectors, alarm and fire monitoring equipment, biometrics access, electronic surveillance, bar code scanning, RFID and armoring, among others.
The PSIM market potential is estimated at 10 percent to 15 percent of this total number, or approximately $10 billion by 2012. It is estimated that revenues from independent software vendors in the PSIM space will triple in 2008 and each year following.
This article describes how PSIM solutions that can be recommended by security dealers and systems integrators to their customers will help those customers if they are challenged with analyzing and responding to all the alerts and events coming from the variety of security and surveillance systems.
If dealer/integrators’ customers are dealing with an overwhelming number of false alarms making it difficult to find the real emergencies and threats, or if they are tired of doing autopsies on situations rather than proactively responding in real time, dealer/integrators should advise end users’ adoption of PSIM systems.
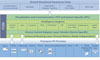
A variety of informational sources must be combined to achieve the situational awareness on which users can base a real-time security decision.
DRAWING AN IT PARALLEL
A relevant, simple analogy can be drawn to IT network technology. The physical security market has the same problems as the IT security market, with a few distinct differences.For example, the physical security equipment market is much larger than the IT security market, with over $50 billion in annual spending and approximately 10 percent of that annual budget going to point products. Furthermore, because the industry lacks standards in general, physical security products typically are built with vendor-specific protocols.
Security event management (SEM) and security information management (SIM) are used in the IT security field, and have served as the data collection and correlation engine that enables an IT security manager to manage network “noise” — ferreting out false alarms and false positives from true events that require attention and response.
SIM enables organizations to pull data from firewalls, intrusion detection and prevention systems, anti-virus software and log files to create a clearer view of network activity and how to respond swiftly and effectively.
In both the IT and physical security markets, many point products and systems are deployed with their own management consoles and reporting mechanisms. This makes it difficult to manage situations that span multiple products. The IT security industry has developed and deployed SIM products to address this problem.
Companies are now applying these concepts to the physical security field, producing greater insight into what is going on in a customer’s environment to provide real-time situational management and awareness.
By correlating and analyzing the data feeds and alarms from various sources, a PSIM solution can provide the context that enables the right response to real threats and security events and disregards those that are false alarms or unimportant.
Additionally, a PSIM solution can go a step further, using video technology to put “eyes” on a situation to either verify the emergency and monitor actions, or to validate that no threat is present.
For example, a single car in a parking lot late at night may not be a cause for concern, nor a rattling door handle. But if these two are combined with a motion detector alarm in a transformer room that typically is only accessed by maintenance personnel at mid-day, action may be recommended.
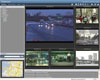
Some PSIM solutions, such as this one, use a geometry engine within the software to calculate the nearest/best cameras based on camera locations and presets.
HOW DOES PSIM WORK?
PSIM technology is based on a unified management platform that ties disparate physical and logical systems (video surveillance, recording, analytics, sensors, access control and more) together to arm security personnel with immediately useful information and the means to use security and surveillance tools to respond to current security events. This is accomplished by:- Enabling the integration of multiple, often siloed products and systems, including various video protocols/formats and sensor/device management systems into a single seamless management platform;
- Capturing and correlating real-time events from multiple systems;
Automatically presenting real-time and recorded geographically relevant video to validate threats;
- Providing real-time collaboration, escalation and notification by integrating with existing communications infrastructure; and
- Providing an easy-to-use user interface that includes geographical information systems (GIS) to graphically manage and represent data and current status.
Specifically, PSIM solutions help solve key technology issues that organizations face as they strive to meet their primary mission of protecting people, assets and infrastructure, such as:
- Analog to digital migration – Organizations have to manage a large installed base of analog (90 percent-plus) along with the fast-emerging IP digital solutions;
- Multiple management systems – Every product and system has a proprietary standalone management console;
- Data overload – There are too many cameras to monitor and too many data sources to track;
- Disparate equipment and systems – Systems such as surveillance, access control, information security and more, to date, have been built in silos and do not interoperate;
- Proactive mitigation – Forensics only helps “solve” the crime and does not accomplish the primary mission of preventing it;
- A mix of legacy equipment and networks – Fork-lift upgrades are unrealistic and are simply unacceptable;
- Archive and storage – Legacy tape systems are not suitable for fast data retrieval or event correlation; and
- Lack of standards – Command and control systems do not operate on known standards.
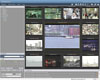
The output is combined from several cameras into a single view in the user interface, displaying active and candidate cameras while presenting the path on a map or building drawing.
THE BENEFITS OF A SOUND PSIM STRATEGY
Having the ability to manage, analyze, correlate and validate data from both physical and IT security sources enables an organization to secure its people, property and assets more effectively.PSIM also applies policies and procedures to this data to produce a recommended plan of action for a given event, and ties into the communications infrastructure to distribute the information to the appropriate parties. This reduces the strain on security personnel during a situation and can provide important decision support for first responders.
PSIM solutions and processes enable organizations to effectively manage the influx of data from multiple physical security systems as well as those from IT security systems, enabling users to identify threats, trends and security incidents more quickly and easily.
Additionally, these solutions enable security dealers and systems integrators to recommend that organizations plan security purchases better and install systems for improved integration and information sharing.
This will allow personnel to monitor and manage security systems better and deploy resources more efficiently while measuring success with more accurate, timely and relevant reports. The result can save time, money and in some situations, lives.
An effective PSIM solution:
- Enables all security equipment in the network to be managed by a unified user interface – simplifying management, decreasing reaction time and reducing training costs;
- Supplies security teams with the necessary information to plan for and intelligently anticipate the next security threat;
- Quickly detects when threats are beginning and alerts relevant personnel through a variety of communications channels; and
- Provides a view of the security threat and coordinates a rapid and informed response to threats by security and operations personnel.
PSIM solutions should be evaluated on criteria such as being standards-based; having an open architecture that can integrate data from any detection, monitoring or control system; and a hybrid design that supports both analog and digital video technology.
An open platform approach is a terrific starting point for an overall security system, but often a customer’s enterprises or security operations centers already have invested heavily in proprietary systems. In these cases, facilities should have the right core architecture to ease the integration of various systems.
By providing the right information, policies and communication options to security personnel, security dealers and systems integrators can ensure that their customers’ security personnel make concurrently faster and more accurate assessments of live situations before the security team becomes a forensic team.