There exists a common misconception among small to medium-sized organizations regarding their susceptibility to cyber-attacks. This thinking leads to a false sense of security and will only lead to future breaches because attackers don't care about the size of your company — they only care about the data.
Integrators are a prime target just like MSPs and MSSPs, since they have access to many clients. This one-to-many setup allows attackers to spend more time on a single integrator that can provide access to many clients’ data in a single breach or attack.
I’m going to touch on the top things that I have seen integrators do that could lead to breaches.
1. Sharing of corporate passwords for devices — I have seen numerous integrators resort to sharing root or admin passwords across clients. Sharing passwords allows an attacker to crack one password, which then gives them access to all clients that share that password. Once an attacker has one password, they are then able to move from the integrator’s network into their clients and steal more data. If this is discovered as part of the incident response that the breach was due to a connection with the integrator, it can lead to cyber insurance claims and potential lawsuits.
2. Weak passwords — This is a recurring issue that I have seen impact more than just integrators. Passwords need to be complex and have a minimum of eight characters with a special character and number mixed in. Many places that I have worked with have something simple for access to devices, such as Company123!! as the password. If multi-factor authentication is enforced on the devices then this becomes less of an issue.
3. Having physical security systems on the same internal network — Incorporating physical security systems within the same internal network introduces another vulnerability and system for the client to make sure is patched appropriately. Adhering to best practices involves placing these systems on a separate network (VLAN) and allowing only certain internal IP addresses to establish a connection. This will keep malicious insiders from connecting to the systems and making changes or taking control of the system and causing issues.
4. Allowing any external IP to connect — Many integrators poke a hole in the client firewall to allow remote access to manage the on-prem devices. Knowing that the integrators are not firewall experts, we cannot expect them to know the vulnerability they could be introducing to the client’s network. Integrators should work closely with internal IT teams or the clients’ MSP to make sure that they are only allowing the integrator’s external IP addresses to connect to the system that is on the internal network. Thus keeping the rest of the internet and potential attackers from seeing the third-party system. With that said, if an integrator is breached and the above is true then having this in place won’t matter.
An example of leaving cameras open to the world and the internet is shown below. These cameras could have been installed by integrators or by individuals themselves without limiting access to these devices. Many tools on the internet can do what is shown below.
The search query in the tool used is in the screenshot below. A subscription to the service is needed to use the filters to narrow searches.
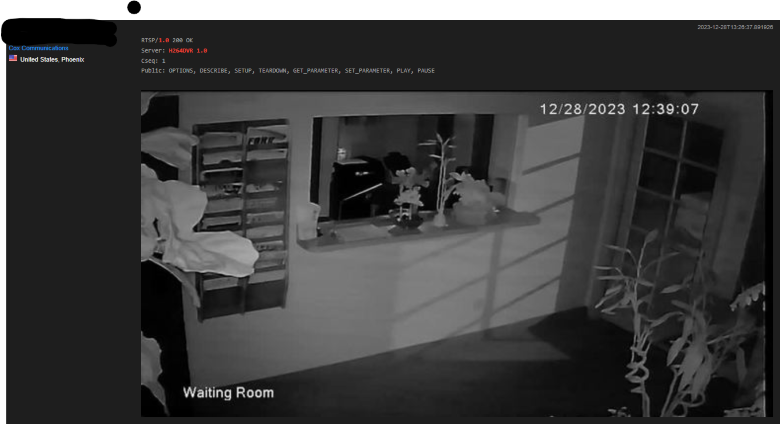
The resulting image for this search is for a possible healthcare facility in Arizona. Would you want to visit this healthcare facility knowing that you could be seen on the internet? Based on the timestamp of this image, and that it is black and white, this was scanned by shodan at 12:39 AM, so no one was in the office.
Evident from the provided screenshots, it becomes apparent how effortlessly an attacker can gain valuable information from the internet. Tools such as that used to gain camera access above were designed to help companies enhance their security posture. There inevitably exist individuals who will abuse technology for malicious purposes leading to breaches and loss of personal or corporate information.
These are just some of the standard best practices to keep in mind when it comes to cybersecurity. Avoid falling into the trap of thinking, “It can't happen to us; we’re too small to attract malicious attention.” Your company size does not determine vulnerability. You may be small, but the data and access to customers’ data you possess categorize you as a more substantial target than you might realize.







