
Stand-alone locks also can be integrated with
logical security when they utilize card access.

Manufacturers have been doing their part by creating such systems, but systems integrators are still in the early stages of developing the markets for them. Some single sign-on systems are in beta testing, and the integrators did not want to release information about installations yet. But forward-thinking security companies think the market for converged physical/logical security systems will be quick to develop once the return-on-investment (ROI) can be demonstrated.
Arthur Bourque, president and CEO of Surveillance Specialties Ltd. (SURV), Wilmington, Mass., has been approaching his customers about single sign-on systems.
“We think the demand is weak,” Bourque concedes. “Most of our customers who are in the physical security world aren’t aware it is out there. When you sit and talk to them about it, their eyes get big. They start to think about it, and they get excited about it.”
A manufacturer of single sign-on systems reports that its integrators are selling and installing systems for customers who are using the access portion, but not the logical sign-on part of the system. Bourque has an idea about why that is happening.
“The problem we have is that most physical security managers don’t have leverage over the IT department,” he laments. “So it requires a separate selling job to the IT guys, and IT guys have had some experience with single sign-on which has not been good, and in some cases really horrible. Even the IT guys we have on our staff had heard single sign-on was fraught with disaster.

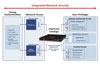
This device, part of Imprivata’s OneSign
identity and access management platform, seamlessly integrates single sign-on,
user provisioning, physical access control and event reporting to provide one
automated employee information access policy managed and enforced within a
single administrative framework.
Like many security integrators, SURV tests technology before recommending it to its customers. The company has installed a single sign-on system in its offices and has had a good experience with it.
“We’ve had it running here and we love it,” Bourque enthuses. “It’s just so convenient to have it. We’re using it with finger readers. You log on, hit control-alt-delete, put your finger on the reader and the rest is history.”
The advantages of single sign-on are several. With a single database to access a building and a computer network, the costs of maintaining multiple databases, cards and separate security networks that might exist can be consolidated. Some savings in manpower also might be realized.
Having a single database can reduce auditing costs and eliminate duplications and misidentifications, such as James Smith and Jim Smith in two different databases having duplicate credentials but being the same person when the databases are merged.
More importantly, it can be used to quickly and effectively remove privileges for physical and logical access from locations around the world when an employee leaves or an emergency occurs. If the employee leaving had obtained duplicate credentials from two different databases and the existence of the second credential was assumed to be another employee, only canceling one would be ineffective.
Merging databases has been accomplished for the City Colleges of Chicago, the third largest community college system in the country, by systems integrator SD-I, Chicago, reports Tim Portokalis, SD-I’s principal and national solution executive for infrastructure.
The colleges wanted to standardize credentials for their 8,000 employees and roughly 130,000 students and access at its 14 locations throughout the Chicago area.
“They all have unique access systems, and they wanted to standardize on that,” Portokalis explains. “There was a big push for it after the Virginia Tech shootings, but it’s an expensive upgrade.”
Consequently, the access portion of the job was canceled. For authentication, SD-I built an infrastructure based on LDAP 3, the latest open standard.
Regarding the cost of single sign-on systems, Bourque admits he has nothing with which to compare the cost of the system his company is using.
“I thought it was remarkably inexpensive,” he asserts. “We were shocked at what the price was, particularly with the interface. When we looked at the added level of security, we were really surprised at how inexpensive it was.”
On the network side, strong authentication is
required to access a company’s computer network and user privileges.
WHAT’S MY PASSWORD?
Using smart cards or biometrics to log on can save the expense of resetting forgotten passwords, which in a large corporation can amount to $25 to $40 per incident, asserts Jeff Ciraulo, vice president of marketing at Envoy Data Corp., Gilbert, Ariz. That cost includes the lost time of the unproductive employee and the time of the employee who resets the password.Bourque has had similar feedback from his customers, with whom he has had some success interesting them in a single sign-on system. “The customer told us that the single most frequent call to their help desk is for people who have lost or can’t remember their passwords and need help getting signed on,” he relates.
Using single sign-on would result in a 60 percent reduction in manpower and contract help desk personnel, the customer calculated.
“With the reduction in cost just from a staffing perspective and elimination of the significant number of after-hours calls they pay for on a per-call basis plus a retainer will pay for itself in the first 18 months,” Bourque maintains. “In their case, it was the ROI they found attractive with this system.”
So some of his customers are considering the system, Bourque reports. “We have not implemented a full system yet,” Bourque reveals. “We’ve implemented a demo system for a customer. They’re coming back, and we’re having a meeting with them to see how they want to roll it out. They had very good success with it.”
Another advantage with smart card or biometric sign-ons is that more complex upper- and lower-case alphanumeric and non-alphanumeric passwords can be used. These can improve security and make it unnecessary for employees to leave notes to themselves with their passwords because they are too complex to remember, Ciraulo points out. Passwords also can be changed more frequently, such as every 90 days.
“You can eliminate all your passwords, not only for the network log-on, but also different passwords for different applications,” he notes.
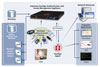
The architecture of the OneSign platform is
integrated with leading physical access control servers.
Bourque notes that tailgating can be prevented with single sign-on. “All our physical security people think it’s great; it will force their employees to badge in before they get onto the network and prevents piggybacking or tailgating, and forces people to badge in,” he emphasizes.
“The customer we’re currently rolling it out for is a biopharmaceutical customer who had some the Sarbanes-Oxley concerns raised by their auditors,” Bourque says relating to network access.
The customer went back to its auditors and showed them the single sign-on system Bourque’s company was proposing to install. The auditors said it would satisfy their requirements as a publicly traded company, he says.
“Our hospital market is where we think we have the most leverage to do this, because quite honestly, the HIPAA requirements are significant for those medical environments,” Bourque stresses. “They want to make sure the log-in procedures are followed and the patients are protected.
“We think over the course of the next couple years, it really will catch on as our physical security technology becomes more network-centric,” Bourque concludes. “This is just a logical extension of what we’re currently selling to our higher-end clients. From our perspective, it’s a win-win all the way around. I think this represents the future of technology.”
Editor’s Note: At press time, Honeywell announced that it had released results from a new convergence survey. You may read more about “Enterprise Threat Management and Security Convergence: A Benchmarking Study,” at www.honeywellintegrated.com.
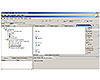
This is the request/approval process for
entering a new contractor into the Honeywell and Novell solution.
Sidebar: Tracking Employees by Combining Databases
One aspect of combining physical and logical security is being able to provide seamless tracking of employees’ whereabouts through physical facilities and logical databases.Honeywell is working with Novell, ImageWare Systems Inc., and ActivIdentity on integrating physical and logical systems to comply with Homeland Security Presidential Directive 12 (HSPD-12).
Honeywell and Novell also are working together to simplify the management of identity information and assigning privileges manually across several systems.
“The commercial customers that we’re getting the most traction from have been larger customers or customers in very regulated industries, so that includes utilities, pharmaceuticals and financial space,” reports Beth Thomas, manager of product marketing, convergence, for Honeywell, Louisville, Ky. “We’re seeing a trend starting with larger organizations.
“We do have several proof of concepts running at present, and we have a couple good systems — one is going in now in the Middle East, but it would be premature on that project to expose it,” Thomas reveals.
Honeywell’s efforts go far beyond just allowing access to a door or a computer system. “Door and computer is one part, and for some people that may be just all they need, and that’s fine — we have options in that area,” Thomas remarks.
But Honeywell’s solution is scalable, so module after module can be added to it. It can combine travel systems, data records from cell phones and other information to produce a timeline of someone’s movements through doors and data.
If the system knows an employee is in Rome but the security system in New Mexico is receiving the employee’s credentials there, a security flag would be raised, she says.
“As long as you connect the systems together, you can get the whole trail of a person’s interactions,” Thomas points out. “It can be a safety feature besides being Big Brother; it can be both good and bad. If you think of the case where some people have gone missing and it takes a while to notice and see some pattern, it can be beneficial and can locate an employee.
“It’s a very exciting area,” she concludes. “We’re getting a lot of interest in it; it’s definitely a new way of going to market for our dealers.”

Below the keypad of the stand-alone Kaba E-Plex
5900 electronic lock with CoreStreet’s Card-Connected technology is the card
reader area. The keypad is for inputting additional authentications, such as a
PIN.
Sidebar: Integrating Stand-Alone Locks
Stand-alone locks also can be integrated with logical security when they utilize card access. The same card can be used to open a single door and obtain access to the computer network inside through a card reader.Such applications are useful in remote locations in the petrochemical industry, or to lock file cabinets in the financial industry, health care, telecommunications and educational markets, says Guy Van Collie, vice president of marketing for CoreStreet Ltd., Cambridge, Mass.
His company has partnered with Kaba, Winston-Salem, N.C., to offer a stand-alone lock that meets FIPS-201 requirements and another that employs a smart card to enable the user to carry audit information back to the network rather than having to download the information into a laptop or handheld computer or PDA.
“It allows you to deploy these locks to doors at a fraction of the cost of wiring them and at substantially less cost than putting in a wireless infrastructure,” explains Todd Freeman, CoreStreet’s manager of physical security product lines.
The patented technology, which is named Card-Connected, is being tested by Niscayah (formerly Securitas Security Systems), Duluth, Ga.
“In a traditional access environment, you basically have 95 percent of the doors in the building un-supervised, and those are on a mechanical lock or a regular piece of door hardware,” points out Marty Guay, Niscayah’s COO. “Five percent of the building has access, and typically access is for the perimeter of the building, for areas of the building, but not for specific offices of the building.”
Two of Niscayah’s Fortune 500 customers, one in the petrochemical industry and another in tele-communications, are beta-testing the Card-Connected system, Guay reveals.
“A few of our customers right now are very much onboard with the proof of concept,” Guay reports. “Now it’s really proving out the content in the reality of their businesses.
“They very much understand the implications of providing more security to their enterprise at a much reduced cost,” he concedes. “To wire everything in a refinery is very cost-intensive, but to have a card-connected solution is very interesting.”
Guay estimates the cost of the stand-alone, Card-Connected solution can be half that of installing wired access to a door. He mentions CEO’s offices and those affected by HIPAA requirements as being candidates for this type of system.
Tying the Card-Connected system into logical access to the computer network makes access to the building another proof of authenticity for access to the network, Guay explains.
“So your same cards can be multi-application cards with the same access rights,” Van Collie notes. “You can log into a workstation or obtain access to a VPN network. The smart card reader is attached to the inputs or outputs on a computer.”
For more information, visitwww.corestreet.com/solutions/prod_tech/card/.
Sidebar: Selling Single Sign-on
Selling a system for single sign-on to physical and logical security requires a good understanding of both disciplines, points out Franco van Heijningen, vice president of technology and personnel development for Niscayah, Duluth, Ga.“It’s a crossover product, which means you have to understand both industries fairly well in order to sell it,” van Heijningen emphasizes. “You need to find a situation where you have somebody from the IT department in the room who immediately understands what you’re trying to sell them.”
Single sign-on systems also require a skilled sales force to explain their benefits. “You also need to train your sales force to be able to communicate at that level with the right people,” van Heijningen advises. “The box doesn’t sell itself — it needs to be presented in the right fashion.”
Niscayah has installed single sign-on systems for several clients. “I don’t think you can designate a type of client or a type of vertical that is more or less interested in something like that,” van Heijningen says of single sign-on. “Clients are 99 to 100 times interested in this feature to their system. If you’re not in the building, you can’t physically log in.”
With this technology, van Heijningen maintains a client’s size doesn’t matter. “This is what I’m seeing,” he asserts. “If I’m getting in front of the client and I’m pitching this tool, they are very interested in this new opportunity.”
Single sign-on systems can have multiple uses that increase their value, van Heijningen emphasizes. “If you leave the office and forget to sign off, I can’t log you in because you’re still in the building, which creates another opportunity to make sure people are using the sign-in and out feature,” he points out.
“In case of an emergency, in a mustering situation, you know who is really in the building or not,” he points out. “I promote this not as a single product with a single feature — it’s a single product with multiple features that can be used throughout an organization.”
Sidebar: Where to Learn More
Interested in learning more about single sign-on technology? Check out the following companies:ASSA ABLOY
www.assaabloy.com
46 506 485 10 (in Sweden)
Bioscrypt
www.bioscrypt.com
(905) 940-7750
Cisco Systems
www.cisco.com
(800) 553-6387
CoreStreet Ltd.
www.corestreet.com
http://www.corestreet.com/solutions/prod_tech/card/
(617) 661-3554
Envoy Data Corp.
www.envoydata.com
http://www.envoydata.com/security_products/1Point/1Point_overview.htm
www.1pointsecurity.com
(800) 368-6971
Hunt Business Intelligence
(Formerly 4A International)
www.securitydreamer.com
(847) 733-0200
Honeywell
www.honeywell.com
(800) 573-0154
Imprivata
www.imprivata.com
http://www.imprivata.com/content414.html
(781) 674-2700