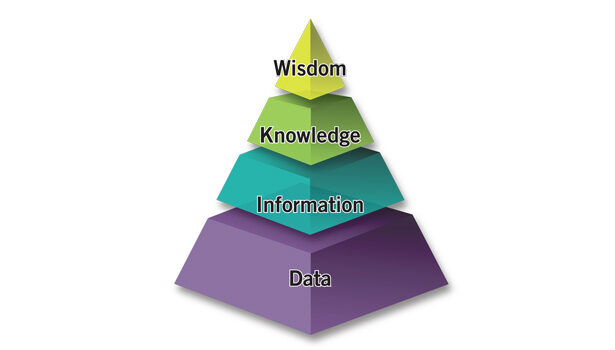
Think of the countless access control systems around the globe recording every entry and exit; the innumerable cameras silently collecting video; the point of sale systems recording billions of transactions. There is a flow of raw data constantly streaming from them all. That non-stop data collected from security systems can be converted into information, including business intelligence. That information helps businesses evaluate and optimize operations, improve marketing, meet regulations, plan business requirements, and the list goes on. The information contained in the reports such as people counts, vehicle counts, object density, occupancy, traffic flow, dwell time, activity level, and more can provide businesses with significant knowledge, adding a compelling argument for security systems’ value in a time when value and perceived return on investment (ROI) mean more than ever.
“Today’s business intelligence is the product of carefully planned strategic solutions that deliver meaningful information on multiple platforms. IP-based video surveillance solutions can work alone or integrate with other business systems such as access control, point of sale and teleconferencing on a network to deliver this intelligence,” says Bill Taylor, president, Panasonic System Networks Company of America, Secaucus, N.J.
The ability to transform more data into information is due to advancements in analytics and video management software (VMS) and is also a valuable by-product of the industry’s transition to IP-based systems. Ones and zeros become information with more ease.
“In the last decade video data started to be digitized and stored on hard drives. Once analog video images are stored on a computer they become data. That data, if organized by VMS, becomes information,” explains Steve Hunt, principal at Neohapsis, Cambridge, Mass.
“The use of computer software and networking has created tectonic shifts in the way security is done. We’ve seen more software, more computing power, more networking and more information in the past five years than we saw in the previous 20. It has been an amazing event witnessing the convergence of physical security with the technology of IT and computer software networking. That brings us to the business intelligence advantage. Once you IP-enable something you start creating a whole lot of data. If you have the right systems processes or technologies in place you’re generating a whole lot of information. That information can achieve the type of usefulness so it is actually considered intelligence,” Hunt says.
Al Shipp, chief executive officer, 3VR, San Francisco, advises keeping the value of data in mind for the future, even if it won’t be immediately used today.
“Most organizations only have a limited view of their enterprise, resulting in an inability to centrally manage or mine their video resources for information that would result in enhanced security, operational efficiency or customer service. [Keep] one simple concept in mind: Provide a solution that solves enterprise-wide physical security problems today but can also be utilized to provide actionable intelligence for their operations, marketing and merchandizing organizations to maximize the return on their video investments tomorrow,” Shipp says.
The future is bright, as the shift to IP from analog is allowing systems to capture data that wasn’t possible before.
IP is the enabler for business intelligence opportunities, says Hedgie Bartol, retail business development manager at Axis Communications Inc., Chelmsford, Mass.
“An analog device is a dumb device that captures a video image. It does one thing. Today you wouldn’t go out and buy a word processor, you would buy a PC where you can not only do word processing, but you can do spreadsheets, presentations, etc. — anything you need as soon as the requirement arises. An analog camera captures an analog image, but a network camera collects usable data instead of just a picture. And you can do so many other things with the data as the need arises,” Bartol says.
The door to new possibilities like business intelligence has been emerging for some time.
“Manufacturers have been talking about developing these technologies and using available data for years now, and the reality is beginning to catch up in a meaningful way. The marketing piece is definitely there, and the early adopters are already putting these types of systems in place. As IP-based solutions continue to gain traction and the technology continues to evolve, we will see more and more such solutions being deployed, providing more business intelligence to users,” Taylor expects.
Every network system that is installed provides another blank slate for business intelligence applications, says Paul Smith, vice president of Americas sales, DVTel Inc., Ridgefield Park, N.J.
“The world is moving to network-based systems and as more and more of these systems are deployed, that opens the opportunity to bring in these other benefits like business intelligence — much more so than analog systems ever offered. The more network systems that get deployed, the more platforms that exist for software developers to do with those platforms and create more and more applications,” he predicts.
Journey to Opportunity
After 9/11, the industry experienced tremendous influx of technologies like analytics and video management software that are part of the chain that produces business intelligence today.
“Go back to 9/11 and look at what happened to the security industry after 9/11. There was an incredible spike in demand for the highest level of technology. The industry wasn’t prepared for it — no one could have been prepared for that kind of change in business,” remembers Kevin McCaughey, vice president of security solutions, Buildings Business, Schneider Electric, Carrollton, Texas. “A lot of new technology came out of it: some effective, some less effective. Today, the less effective ones have been weeded out and we are at a point in the security industry where the technology that is available is proven technology. The software is much more mature and the opportunity to produce intelligence-based information is now there,” McCaughey says.
“There’s another gap that today’s technologies is helping close — the ROI gap,” McCaughey points out.
“We’ve closed the technology gap that emerged after 9/11, but in the process of doing that we developed the ROI gap. Customers and end users don’t know how to utilize the full system and aren’t getting the full return on investment from their systems. That is why it takes a combination of us, the manufacturers, the consultants, the end users who know their businesses best — all working with the customers to solve problems and maximize everything these systems can do,” McCaughey says.
“Analytics saw a huge increase in development after 9/11, but it also got a bad rap when the high expectations for it weren’t met. In a true security application, using an object-left-behind application to detect a bomb, a one percent failure rate is a big deal, but if you shift from a military-type application to business intelligence you have new parameters. The fail rate is very different for traffic patterns and dwell times,” observes Jackie Andersen, retail business development manager at Axis Communications.
As Smith succinctly summarizes, using analytics for business intelligence gives you some slack on accuracy because you aren’t playing with lives. But to increase accuracy, he advises companies take an approach like that of ioImage, a video analytics company acquired by DVTel, and choose to do fewer things, but do them effectively so there are no dashed expectations.
In addition to effectiveness, increased interoperability is opening more business intelligence opportunities as well and is key to transforming data into information.
“Turning the data from security systems into actual information is the key to making the solution work,” Taylor says. “System interoperability is critical; you can be certain to accomplish this with a system from a single vendor; short of that, an excellent integrator and strong partnerships between providers will create the interoperability needed to make this solution a reality,” he says.
Andersen adds, “Information is what leads to intelligence and you can combine more information when you are working with an open system. Not only that, you can combine more available solutions. We allow 800 partners around the globe to create new solutions through our AXIS Camera Application Platform, the open application platform that creates unique possibilities to meet specific end user needs by enabling download of third-party applications to Axis network cameras and encoders. That is a lot of flexibility in the solutions that can be tied to the camera.”
“Today, end users are becoming educated on the benefits of IP video surveillance beyond security, primarily by providers who are marketing their products and services with that message,” says Gadi Piran, president and chief technology officer (CTO), OnSSI, Pearl River, N.Y.
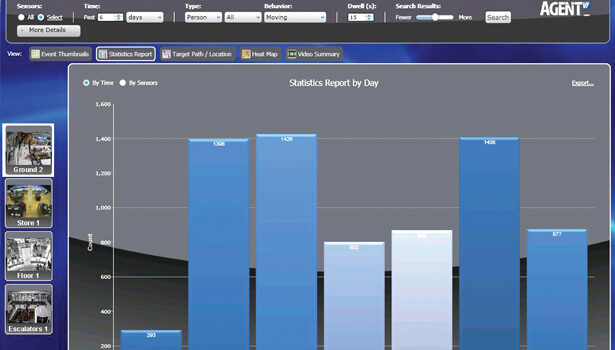
Zvika Ashani, CTO, Agent Video Intelligence (Agent Vi), Rosh Ha’ayin, Israel, says his company is seeing an increase in customer requirements for the technology.
“Previously, the main focus we saw for video analytics was event detection: alerts for security breaches, vehicles parked at the entrance to a building too long, etc. While we still see growth in that security-focused area, we are seeing an increase in customer requirements for business intelligence applications. People are seeing this technology actually works, that deployments are being successful, and that the cost of cameras, hardware, and software is going down,” Ashani shares.
The lower price point is driven by increased innovation from manufacturers and integrators are also focused on capitalizing on the technology.
“On a sales and marketing level, the relationship between security and business intelligence is growing as manufacturers and integrators see an opportunity to provide more value while increasing their own sales,” Taylor says.
Adoption is increasing because the technology is at a tipping point, Andersen comments. “Previously, there was some fear of the unknown. Now end users are asking, ‘How do I harness business intelligence?’”
Her colleague, Bartol, adds, “The iceberg is emerging and we’re starting to see what is below the surface. We are starting to get a peak at what the analytic market can really offer regarding business intelligence solutions and beyond.
So what are integrators doing?
“Many installers and contractors have matured their businesses. They have recognized that the way they can be more different is to have business discussions with customers. Those installers are not just growing business by winning more bids, but they are talking to customers about how to use the technology for greater good in the business. They are moving beyond security technology for security only and extending the investment,” McCaughey says.
That mentality benefits end users, but more importantly, it protects the relationship the integrator has with the end users, says Marc Holtenhoff, chief executive officer (CEO), Aimetis, Waterloo, Ontario, Canada.
Holtenhoff sees integrators in danger of getting leap-frogged by end users who want the technology and will go to the company that can provide it.
“Systems integrators who are selling the technology they have always sold that are not a champion of educating themselves and their customers on the new technologies will be left behind. End users will attend trade shows and learn about the technology via multiple avenues today. If they want it and they are looking for partners, especially if they are big enough, they will leap frog the systems integrator and then the integrator is reacting and scrambling. That is where a systems integrator who has been proactively addressing the technology will be ready.”
When creating business intelligence solutions, the advantage also belongs to the integrator who focuses on solving the end users’ problem without getting caught in the technology.
Focus on what you want to know, Piran advises.
“You must first determine what it is you are looking for, then develop your criteria and analyze the information gathered,” Piran suggests.
And don’t forget the growing list of systems it can be tied to.
“Business intelligence comes in many forms depending on the application needs you are trying to solve. It’s in the way you integrate behavioral analytics, point of sale (POS), ATM, EAC, time and attendance and many more data feeds. Success is in how you correlate your various data streams to tie in the video and bring real value and actionable intelligence to the customer,” describes Rich Mellott, president, Digiop, Indianapolis.
People, process, and then technology, advises McCaughey. “Our company follows that philosophy and technology comes last by design. Looking at the jobs our customers have to do — whether that is a university, hospital, plant, etc. it gives us an opportunity to apply technology in a better way. Anyone can offer technology, but there is a higher return on investment for customers and it gives us a chance to extract more from technology when we design and choose technology to support their needs from the start. We can introduce technologies and solutions, but it is most effective if we have a conversation with the customer about what their challenges are — facility by facility, business by business.”
Retail is the vertical market that instinctively comes to mind when thinking of markets taking advantage of business intelligence from security systems — but it isn’t the only market. Hunt cautions against limiting the applications for business intelligence.
“There is something for every industry. In energy or chemical markets, I’ve seen companies start to track which employees are spending how much time in what proximity to dangerous chemicals. By tracking that information, the companies are able to meet Occupational Safety & Health Administration (OSHA) requirements. There are examples in every industry, way beyond retail, if you are willing to look for them,” Hunt says.
At Milestone Systems, Beaverton, Ore., Tim Palmquist, vice president of sales operations, agrees that for every obvious example of business intelligence, there are also companies using security system data for novel information that solves a problem for them.
“When you look at specific examples of business intelligence gained from security systems, retail is an obvious candidate, and often the one that comes to mind first. There are so many benefits that companies can get, but that is not the only market using business intelligence. Other types of less obvious trends in the marketplace include a lot of work in manufacturing. Production lines really benefit. Businesses use the information to improve training, eliminate inefficiencies, and ensure regulations are being met.
“Hospitals are using it, while in food safety we see companies monitoring hygiene, checking how procedures are followed and watching food preparation happening, ensuring everyone is clean, in the proper places, etc. We also use information to optimize the training processes for companies.
“I’ve also seen some things I never thought would want to be analyzed, but have proven to be invaluable for companies. Things like how often an escalator is being used or how long the wait time is for elevators. Different things that don’t seem super intuitive but are the right things for the company,” Palmquist lists.
Business intelligence can bring value to many verticals, says Mellott.
“Banking, schools, manufacturing, hospitals/health care and many more verticals apply: Just think about the data and information that ties to business or operational functions and if it correlates to something on a video screen or a video subject you have value to bring to the equation,” he advises.
Banking is a growing vertical.
3VR’s Nick Wooler, director of product marketing, describes a banking solution that is making video usable and searchable for clients every day.
“We enable customer to directly integrate with point-of-sale, ATM and other transaction systems. Therefore, when a bank is investigating check fraud on a specific account, it can type in the account number into the 3VR interface and find the video events from when that specific account was accessed. With this indexed footage readily available in seconds, businesses can instantly search for precise instances rather than manually reviewing hours of surveillance footage.”
Still, there’s a reason people think of retail right away when discussing business intelligence from security systems, especially video surveillance systems. There’s a natural fit between the data collected by the security systems and the information that can be extracted from it.
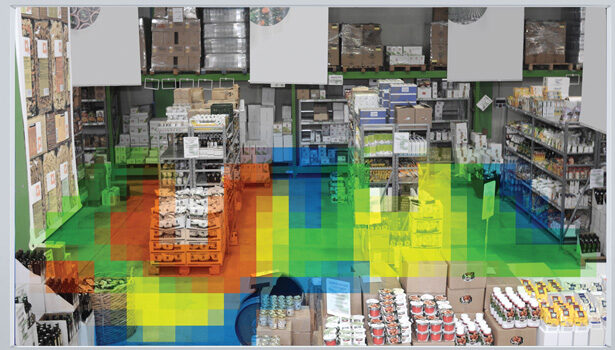
The retail solution from Agent Vi demonstrates how many ways you can analyze customer behavior and provide actionable insights that increase customer satisfaction, expand sales opportunities, optimize store performance, and ultimately, drive profitability. See the photo caption on page 56 for only a few of the possibilities.
Untapped Potential
An important point is that as more and more network-based systems get deployed, they become a platform for someone else’s creativity, says Smith.
“We are planting seeds today to allow ourselves and other software developers to come up with more solutions and more ways of providing business intelligence. Think about it. Apple came up with the iPhone, but how many people have written apps? It is like we are putting the iPhone out there and now countless other people from other domains — marketing, operation, business intelligence, etc. — can develop great ideas in the upcoming years using our security systems and VMS software as a base for other systems, applications, and enhancements to things like business intelligence,” says Smith.
Real growth in the business intelligence field will occur when the industry breaks out of the rut, advises Andersen.
“We tend to revert to the ‘intellectual well’ time and time again and we need to stop doing that. Instead of just getting the job done on auto pilot, we need to open our eyes to the solutions that are out there. Ask questions. We’re no longer locked into proprietary solutions and we can perform analytics on almost anything,” she says.
Bartol summarizes, “We don’t know what we don’t know sometimes. The human imagination can produce magic and provide yet undiscovered solutions.”
Video and data are a magical combination.
“Together video and data provide the customer with truly powerful tools. Business intelligence will make this industry much more viable to the overall business and transcend the security market landscape we live in today,” says Mellott.
|
An Integrator’s Perspective
Phil Aronson, chief executive officer of Aronson Security Group (ASG), Seattle, offers his perspective on business intelligence and how his company approaches the solution. SDM: What does your company offer that facilitates business intelligence? Aronson: Aronson Security Group (ASG) provides professional consulting and integration services to a global market. Our approach is unique. By integrating business process optimization into the security organization, we are able to quickly identify time and cost savings in the security organization that can then be used for innovative technologies and services that add value to the business. Our use of portal technology to capture critical documentation around organizational resilience and the security operation provides the foundation for Continuous Quality Improvement (CQI) measures to be deployed. We use this same approach in capturing the critical data that we generate in designing, managing and servicing the implementation of security technology. SDM: What trends are you seeing in business intelligence? Aronson: More and more executives agree that they are missing a number of key factors in measuring and articulating their value. The critical challenge for them is creating a new scorecard for measuring security’s impact on the business. This is where many consultants and integrators go wrong: It is not what they are asking for that should drive you; it is what they need. Many security executives have not been driven to contribute to the business value, only to protect it. We show them how to do both. SDM: What comments do you have in general about the value of business intelligence gleaned from security systems, and security systems’ ability to provide that data? Aronson: The physical access control systems (PACS) lack the data aggregation and reporting tools to make business intelligence or performance visible. We believe this is a tremendous area for differentiation in the future.
Increase Video Surveillance’s Value for Facility Managers and Building Owners Honeywell, Louisville, Ky., and integration software maker Tridium Inc., Richmond, Va., introduced a software tool that allows integrators and security dealers to more easily incorporate digital video surveillance capabilities into larger building control systems, thus increasing the value of the overall investment in a video system that would typically only be used for safety and security purposes. The new Rapid Eye™ Driver enables Tridium’s Niagara Framework to communicate with Honeywell’s line of Rapid Eye digital video recorders (DVR), used across various industries to record, store and search for video evidence. By integrating the Rapid Eye DVR with traditional building automation technology such as environmental controls, energy management and lighting systems, the Rapid Eye Driver allows facility managers to easily integrate building events with video recordings. Managers, for example, can perform tasks such as diagnosing heating, ventilation and air conditioning (HVAC) maintenance issues or detect water leaks using video. “Rapid Eye Driver gives integrators more flexibility to create these interconnected systems and provide more value for building owners and operators,” says Scott Harkins, general manager, Honeywell Systems.
System Monitors Security and Customers’ Experiences Founded in 1962, Vivara is Brazil’s largest jewelry store chain, with more than 100 retail outlets throughout the country in 24 of Brazil’s 26 states. The company installed Aimetis Symphony™, an intelligent IP video management software from Aimetis, to remotely monitor its stores with video and audio in real time from a central location. Vivara contracted with Ferraz Solutions to implement the surveillance system and provide ongoing support, including staffing in the monitoring center. Ferraz Solutions implemented several fixed and pan/tilt/zoom network cameras from Vivotek and Aimetis Symphony video management software in each store. Corporate staff in a central site can watch and observe the stores in real time, regardless of the distance (some are 2,500 miles away) to see if staff are properly trained/attending to the needs of customers and ensure that jewelry is being displayed properly. Microphones are installed separately from but integrated with the cameras that record staff/customer dialogue to enhance the analysis. This has saved Vivara from the significant costs associated with traveling thousands of miles to observe and improve the customer experience and store performance. Moreover, Vivara will be using Symphony’s people-counting and motion-tracking/thermal zone capabilities to enhance sales. Using people counting, the store can determine how many individuals are entering and exiting the stores on certain days and at certain times of the day to plan for staffing, sale dates, etc. The motion tracking/thermal zone capabilities enable the store to determine locations within the store that customers frequent. |