Where most people see a beach, Tim Chandler, with the help of video surveillance equipment, analytics and the cloud, sees a wealth of information — including data that can help coastal towns, environmental and government agencies, and beach goers make more informed decisions. Chandler is the general manager in the United States and head of global marketing and sales for CoastalCOMS, Laguna Niguel, Calif., an innovative integrator and solutions provider that is using analytics to safeguard shorelines, support research, and offer business intelligence (BI) to coastal communities.
“Today’s technology has advanced to a point where we are able to provide our customers with unprecedented abilities to gather real-time information and images to better understand conditions, coordinate responses, and make decisions in changing water environments around the world,” Chandler says.
Thinking outside the box, the company uses cloud-hosted networks of public and privately owned remote surveillance cameras and employs a set of sophisticated in-house video analytics and complex event processors developed for beach risk assessment and information gathering.
“These aren’t just surveillance cameras [that we offer]; they are the foundation of a comprehensive system of monitoring and analysis that gives real-time information on beach conditions as well as the ability to monitor changes and risks over time and plan accordingly,” says Chris Lane, research and development manager, CoastalCOMS.
In a maturing environment that is driving BI forward on the wheels of partnerships, complementary technologies, and the solid approach of stepping past “data for the sake of data” and working instead to provide the right data to the right person at the right time, many companies are doing more with BI than ever before — seizing the opportunity.
It has been said that the freedom to move forward to new opportunities and to produce results comes from living in the present not the past. For some that means acknowledging that BI is on its way in, and not on its way out. In the past, a security system may have functioned only as a security system, and for the time being that is still generally the case; however, today’s security systems are capable of more — and are being asked to do more by end users. Those living in the present can see the trend.
“There is a paradigm shift happening now in our business. The classic example of this is in the railroad business. They were dominant players in the 19th Century, but somehow failed to get in on the ground floor with automobiles and airlines. Why? They thought of themselves as being in the railroad business. Since they didn’t see that as a subset of the larger transportation industry, they got left behind,” cautions Mark Collett, general manager of Sony Electronics’ Security Systems Divisions, San Diego.
“Today, security is the ‘killer app’ for BI. But BI, too, is too limiting. Even seeing this as the visual information business may be too narrow, especially when the visual information our cameras gather can be integrated with other information systems,” Collett says.
In marketing terminology, a killer application (often shortened to killer app) is any computer program that is so necessary or desirable that it proves the core value of some larger technology, such as computer hardware, software, or an operating system — in this case, a security system. In other words, customers are willing to purchase the hardware or software just to run that application. A killer app can substantially increase sales of the platform on which it runs.
Keith Marett, vice president of marketing and communications, Avigilon, Vancouver, British Columbia, Canada, says his company is actively helping its partners and customers develop strategies to use HD surveillance for BI purposes.
“While HD surveillance will necessarily continue to be used in preventing and solving crimes, more and more we’re seeing its application in a non-traditional sense to help businesses save money and operate their businesses more efficiently like Airberg [Search “UK Food Exporter Secures Facility/Cargo and Saves Money Via BI” at www.sdmmag.com]. In the beginning, we had a handful of customers coming to us with ideas on how to use HD surveillance for BI. That got us thinking and we retrained our sales staff to approach our HD surveillance solutions in a BI framework. It’s a great revenue stream for not only us but the industry as well,” Marett says.
For most companies, the growth is not explosive, but rather simply a steady increase.
“While we’re definitely seeing an uptick in the need for BI, it’s not usually the thing most customers are requesting from us from the start. But we have had situations where, for example, highway management companies wanted a solution that combined things like weather reports with an instant view of specific areas, basically combining weather and video solutions, or in other cases having license plate recognition (LPR) tied in with police crime programs to track stolen cars. That’s all part of the ongoing integrated trend of BI,” describes Al Figueiredo, COO, Intelligent Security Systems (ISS), Woodbridge, N.J.
As BI increasingly proves its worth with results, the budgets available for surveillance systems/BI will grow, predicts Jason Schimpf, director of partner relations, Arecont Vision, Glendale, Calif.
“We are seeing customers who have part of, or most of, their budget coming from the ‘intelligence’ side of their business. With megapixel video enabling the video side of ‘intelligence,’ end users are making business cases that reduce shrink, which ultimately increases their bottom line, and the video allows them to improve people flow, product placement, manufacturing layout, warehouse transport efficiencies, etc., which directly affects their top line. Now, the benefit is coming from the top and bottom line,” Schimpf describes.
“Now that security management professionals have begun to realize the power of BI, the industry has seen them become more and more innovative and more widespread in their use of BI. One corporation, for example, uses each morning’s access control data to determine how many meals to prepare in its own company cafeteria. Since this practice has come into play, the company has reduced a significant amount of waste and hence reduced food costs. In another example, a school used access cards as a monetary instrument in its cafeteria. The meals the children selected were recorded and parents were able to track good and bad dietary habits, to safeguard those children with food allergies and to better understand meal costs. BI was also used in a school environment to provide learning opportunities for children, including tracking carbon footprint and monitoring other environmental concerns,” says Aaron Kuzmeskus, global director, Security Solutions, Schneider Electric, North Andover, Mass.
Rob Muehlbauer, business development programs manager, North America, Axis Communications Inc., Chelmsford, Mass., offers other examples of future applications. “I went to my local bank and the ATM was down. If there was a camera in that ATM, the bank could count how many people drove by and realize how much money it lost during that down time. It is a great example of how a BI application could measure system down time and provide valuable information. Every day there are more and more examples of uses of video surveillance outside the traditional realm.
“We are still in the early stages of development for BI. Today, we work with partners like Exacq Technologies, Aimetis and ipConfigure, to bring solutions to market and increase the awareness so end users and customers can see the value of it and understand what video data has to offer,” Muehlbauer says.
Many end users already have the data collection devices (cameras, storage, card readers, controllers) installed but have not taken advantage of the data that is being generated and stored, observes Bill Bozeman, president and chief executive officer, PSA Security Network, Westminster, Colo.
“Analytics, storage, access control databases and other security control devices provide a goldmine of data for improving and providing business BI. Most responsible for security systems management use the information security devices gather for forensic work, never utilizing the full potential of the data the devices are collecting. A strong case could be made that security decision-makers on both sides of the fence are often at fault for underutilizing the power of the collected security data,” Bozeman says.
“The end users are often reactionary with regards to security data and in other cases do not truly understand the capabilities of the systems they supervise and are responsible for. Security manufacturers and integrators are focused on getting systems sold, installed, getting paid — often not understanding or taking the initiative to assist the end user with an overall security plan that takes full advantage of the data they possess,” he adds.
Creative Uses
The good news is that as the awareness increases, as the marketing increases, as the education increases, more ideas will flow into the industry.
New ideas is one of the reasons Axis is planning to broaden its platform even further by reaching out to universities to develop on its AXIS Camera Application Platform, an open application platform that enables development of third-party applications (like those offering BI) that can be downloaded and installed on Axis network cameras and video encoders.
“In the future, we are going to add resources for students and universities. In fact, we are starting with a pilot program before the end of this year with a major college in the Boston area. I met with them while setting up the program and within the two hours I met with five professors that all came up with their own viable ideas for the BI and non-surveillance uses that can be derived from the cameras in the span of a conversation. That is just one university and one set of meetings. Extrapolate that out to all the universities across the globe and I think there is tremendous opportunity for the development of these BI ideas and solutions that go beyond surveillance,” Muehlbauer shares.
Axis is also in talks with the Boston Innovation Center about ways to utilize cameras that will be in the facility. Officials recently celebrated the groundbreaking of the $5.5 million Boston Innovation Center, which is expected to be a hub for entrepreneurs to meet and exchange ideas, to convene programs and events, and to build the city’s innovation economy.
“We’re talking with them to provide our cameras to run hack-a-thons — where you shut in developers for a full day or even a weekend and they just look at developing applications that provide solutions for a specific problem.
“Can you imagine the solutions that can come out of having random, brilliant software developers coming together and asking, ‘What can I do with this camera/platform?’– while looking at it from that non-security lens?” says Domenic Locapo, Axis’ PR specialist.
Relevant Intelligence
As the technology gets more advanced, the goal remains simple: getting meaningful data to the customers.
“I don’t want to underestimate the level of effort that went into developing our BI environments from our IT guys because that is extensive in and of itself, but so much of the heavy lifting with our BI solutions are less about the technology part, and more about the understanding of what data is relevant to solve problems or create efficiencies on both ends of the spectrum — ours and the customer’s,” relates Don Young, chief information officer, Protection 1, Romeoville, Ill.
Getting the right data to the right person also includes getting it on the right device, adds Reinier Tuinzing, strategic alliance manager, Americas, Milestone Systems, Beaverton, Ore.
“For example, the first responders need the relevant data, delivered to a specified/authorized user, at the moment they need it, on the device they are in front of at that time, whether it’s a smartphone, a mobile PC in their car/truck or the security center video wall.”
Mobile BI Solutions
“Mobile distribution advances have been driven mostly by the ‘can’t-live-without’ mentality of consumers who will spend almost anything on more convenient ways to stay connected to their favorite environments wirelessly. This culture change has helped fund some of the most significant technological innovations in years in handheld devices and tablets. These innovations have led to more recent development of applications and high availability bandwidth to support this growing appetite for data. The resulting improved delivery mechanisms have altered our way of thinking about how much data to share and when it’s appropriate to share it. For example, live dashboards and real time event reporting are now a necessity where only a few years ago they were considered optional for any BI solution,” Young writes in “Trends That Will Change Your Game Plan.” (To read the entire white paper, go to sdmmag.com.)
Just as business professionals use their smartphones and tablets for everyday office work, more and more security professionals are seeking access to their security and BI, wherever they happen to be.
“BI data inherently is meant to be shared, so if clients use a Web-based solution such as Software House’s Business Intelligence Reporting Suite (BIRS), they can view, review, export and share data on any browser-enabled device, review it, export it and share it quickly. BI is a lot of things, but it has to be portable, available and concise,” emphasizes Hal Bauer, sales engineer, Tyco Security Products, Westford, Mass.
Authors Andrew Borg, research director, enterprise communications and mobility, and David White, senior research analyst, business intelligence, Aberdeen Group, define mobile business intelligence as, “The capabilities and technologies that allow access to reports and charts while away from the desk, out of the office or in the field.”
The report also shares that “on average, managers in organizations that use mobile BI are able to make decisions in almost one-third of the time that it takes managers who don’t use mobile BI.”
How is this dramatic difference possible? “Robust mobile analytics implementations put information at the fingertips of front-line personnel — anytime, anyplace, anywhere. In the otherwise lost minutes, between meeting and appointment — or even furtive moments snatched during them — managers are able to make operational decisions that keep the organization running smoothly, without stalling. In contrast, decision-makers that only have access to conventional ‘deskbound’ BI do not have this freedom. They are restricted in the time windows available to them to make decisions. If these decisions are collaborative in nature or involve a chain of command, this problem of information and decision latency is further compounded and is likely to ultimately slow down the entire decision-making process,” Borg and White describe.
As Gadi Piran, president, OnSSI, Pearl River, N.Y., puts it, “Real-time video of enterprise operations represents agile BI in the extreme — the ability to know exactly what’s happening anywhere in an organization at any given moment.”
On the other side of the argument, Steve Van Till, president and chief executive officer, Brivo Systems, LLC, Bethesda, Md., agrees that mobility is certainly a major trend in BI in general, but has doubts about how relevant that will be in the long run or how effective those snatched moments of decision-making really can be.
“By definition, BI is an analytical tool that lends itself to deeper study and reflection, so I’m not sure how much of that will happen while people are staring at their iPhones on the highway or in the middle of a meeting or at their kids’ soccer game.
“That said, we’ve provided a mobile website to serve the needs of our more mobile customers. I think that the key value mobile BI can deliver is to summarize certain types of data for quicker decision-making. That said, I do question some of the hype surrounding just how much deep analysis will actually be performed in a mobile context,” Van Till asserts.
Powerfully Simple
Protection 1 has its own approach to BI. Instead of chasing exotic or traditional BI opportunities, following a “Voice-of-the-Customer” study, it chose to focus on offering simple BI solutions that still hit customers’ pain points and impact their bottom line. The strategy cuts through the masses of data and targets the sections that mean the most, allowing customers to make use of it.
This approach combats one of the criticisms of BI: too much data. For example, 40 percent of all respondents to an Enterprise Management Associates’ (EMA) survey said they are overwhelmed with the monitoring data they already collect. Seventy-three percent indicated they would collect even more security data, if they could make use of it. That is the challenge for the security industry — making the data mean something.
For Protection 1, this starts with providing very focused pieces of data, rather than getting sucked into the sheer amount of data and the surplus of information it can provide.
“Previously, we have seen a big gap in the industry about how people are thinking about BI, but when we held a series of ‘Voice of the Customer’ one-on-one sessions with both customers as well as prospects, what we found was what customers were missing in their security provider was basic level BI, saying ‘I get sales data every day. Why can’t I get security data the same way?’ It was a request that was literally unanimous,” recalls Jamie Haenggi, chief marketing officer, Protection 1.
“I think people quickly jump to BI being around loss prevention, crime data, return-on-investment (ROI) type information, and the prevalent video and access control BI. But there is more data we collect as an industry that can become powerful intelligence impacting a business’ bottom line and operations. As we developed those services, we coined them as Being Brilliant with the Basics, asking ourselves ‘How do you bring data intelligence or BI down to a very basic level first, so that customers can really maximize the content?’”
Haenggi adds, “There’s so much data that we get today that is not used to manage the operations as efficiently and effectively as it can be. I think one of the things Don Young has done a phenomenal job within the industry — and particularly the past two years at Protection 1 — is really understanding how to take the mounds of data that are generated out of the simple burglar alarm system — something as simple as that — and still use it to really understand and manage your operations,” Haenggi says.
Today, Protection 1 offers intelligence in a variety of formats including:
Benchmarking — This helps the customer understand their activity versus their peers as well as creates a template for performance improvement for both customer and Protection 1. Action plans are created and then tracked over time to help customers bring their security program to a “best in class” level.
Dashboards — A quick and easy way for a customer to see key metrics for their security program. The approach to delivering this data is unique in that first, it is customized to what matters to the customer and second, they do not have to log into a portal to get their information; instead, it is delivered right to their email or mobile device.
“For example, one client that we’re working with took a different approach with their camera system because of the data that we were able to provide for them. Instead of requiring this huge investment in cameras across all of their locations, we started putting them only in certain locations based on data that we had. As a result their shrink dropped dramatically, which then gave them more money to reinvest in the other areas,” Haenggi shares.
Product Inventory — Reports that let customers know what equipment is installed where (down to the location at the site), warranty periods, expected product life, and maintenance plans — all so they can plan and budget for their security program.
“Having a detailed product inventory allows business the ability to proactively manage their budget from a security standpoint. It’s a different way to use BI that’s really around operations,” Haenggi explains.
SiteView – Images of equipment installed at national account locations are stored on eSuite, Protection 1’s customer Web portal, giving customers an even better understanding of what security equipment is installed at their sites, both in item data and in pictures.
“Our research sessions with national end users have told us time and again that keeping track of what equipment is installed where is a huge challenge,” said Bob Dale, senior vice president of national account sales. “We want to make that part of their job easier.”
Partnerships
According to Bauer, solutions such as Software House’s Business Intelligence Reporting Suite (BIRS) have actually acted as catalysts for changing the relationship between departments within a customer’s organization. “HR, logical IT, facilities are all cross-reporting or even cross-exporting data with BI systems because BI or rather ‘security BI’ touches all aspects of the industry and security operations. The market demands are significantly different on the fringes; meaning that the government and DoD market may want more alarm and activity-based critical information, while petro-chem industries want emergency response critical data, while corporate clients may want reports to indicate how many people use a building or area to calculate the cost of square foot real-estate.
“But all industries want reports on serviceability of the systems and statistics. Taking a service and serviceability approach to the data, such as with the BIRS solution, allows companies to use the security intelligence to feed other systems outside the security realm and truly share data within the enterprise,” Bauer describes.
Consolidating data also intensifies the focus on the partnership environments. When bringing in more departments and more of the company, integrators have to work together on a completely different level to bring all those people into the conversation and produce what everyone needs.
“Our company has recently embarked on some new practices that enable our sales professionals and energy and security experts to better collaborate with — and really listen to — the needs of customers and apply business intelligence to those needs,” Kuzmeskus says. Schneider puts together 3D business cases or 3DBCs, created in a software called 3DView, to help customers visualize the pain points, the changes, and the future solution. (See next page for an example.) “We collaboratively discuss ‘must haves’ and formulate a jointly designed solution that often includes additional capabilities that the customer did not realize were possible. In many cases, business intelligence can move a customer from the point of solving a rudimentary problem to revamping a core process that in turn nets a competitive advantage. That leads to long-term business sustainability,” he says.
BI is long term.
This is a discipline that is “never truly done,” Bauer believes.
“Once you develop the solution based on a client’s need, by the time you deliver it you may have to retune it to respond to a change in their requirement; 30 days later that need may change again and the solution may need another retune. That is the nature of intelligence and where the challenge and opportunities exist for consultants, integrators and manufacturers of security and BI solutions,” Bauer says.
Still, it is a challenge that has definite possibilities, strengthened by end users’ requests, that holds the promise of long-term relationships for integrators.
Gartner’s report,“Magic Quadrant for Business Intelligence Platforms,” predicts that the market for BI platforms will remain one of the fastest-growing software markets despite sluggish economic growth in most regions. Organizations will keep turning to BI as a vital tool for smarter, more agile and efficient business.
“It’s a sign of the strategic importance of BI that investment remains strong,” states Ian Bertram, managing vice president at Gartner, in the report.
Whether it is the retail analytics, people counting, and operational features that might more quickly spring to mind, or the simple, but powerful solutions demonstrated by companies such as Protection 1, there is momentum in this sector as more integrators make a splash, embracing the data produced by security systems and using it to its fullest potential. As a result, more yet-unimagined solutions are sure to come. As motivational speaker Dr. Larry Iverson says, “It is amazing where you can go when you stop stepping on the brakes.”
Editor’s Note: This article touches on merely a few of the BI solutions the security industry is involved in, and only mentions a fraction of the companies that are doing exciting working in the space.
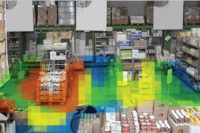
Using Queue Management to Optimize Service |
|
Companies and organizations that provide face-to-face service to customers often deal with the challenge of people standing in line for long periods of time. The ability to effectively manage queue times is critical to enhancing the customers’ experience. Some common queuing scenarios are found in the transportation sphere (airports, train stations, etc.) and in the retail environment, among others. Queue management is a good example of how video analytics can be used for gathering business intelligence. Queuing applications can be configured to store statistical data about average wait times and number of people in the queues. This data later can be displayed in chart and tabular format, and analyzed to determine personnel/staffing requirements based on average wait times at different hours of the day and for different days of the week, with a view to providing optimal service for customers while minimizing costs. For best accuracy, overhead cameras are used in order to minimize occlusions. If required, some software like Agent Vi’s video analytics solutions can be configured to send out real-time alerts whenever queue wait times exceed a user-defined threshold, allowing for an immediate response in such a scenario. — Contributed by Zvika Ashani, CTO, Agent Vi (Agent Video Intelligence) |
Watching the World’s Coastlines and Waterways With High-Tech Eyes |
|
CoastalCOMS is a clear example of just how much information can be pulled from a system, supporting researchers and operations managers by delivering live and recorded video and information about beaches, harbors and waterways correlated to video sourced from surveillance cameras and sensors around the globe. Launched in 2002, CoastalCOMS has progressed from using analog cameras to its current digital, cloud-based infrastructure. “We rode the wave from analog to digital. We really get it when people talk about the challenges of managing a network environment,” says Tim Chandler of CoastalCOMS. “Milstone’s XProtect software allows us to create ‘networks’ of coastal cameras on the fly, patterning and sourcing video from both new and existing shore-based cameras according to each customer’s needs. We then process the video in real time for different groups based on their reporting needs and workflows,” says Chandler. CoastalCOMS’ video content analytics software and cloud-hosted coastal cameras are unique in their collection of real-time beach and surf-zone data capabilities, analyzing video wave height and wave period analysis, vessel monitoring, beach visitor population, and tracking changes in the shoreline and general water states in near real-time. With access to its partner Coastalwatch.com’s cameras and many more private or municipally owned cameras in the United States and abroad, CoastalCOMS uses XProtect to centrally view and control cameras globally, layering in the ability to extract data for environmental monitoring, public education, business intelligence for beach-side businesses, tourism and recreational usage. Quantifying the number of people on beaches and studying local beach behavior can provide valuable information not only for calculating advertising requirements, but also for determining whether a beach environment is sufficient to meet the current human demand. CoastalCOMS also assists the Surfrider Foundation of San Diego with hosted surveillance, analytics and asset management platforms capable of break zone analysis and shoreline tracking to determine impact on local wave resources that contribute to local economies and tourism. The City of Galveston, Texas, Beach Patrol utilizes CoastalCOMS for surveillance of remote beaches because of the increased ability to add shoreline tracking and current monitoring in and around its network of jetties. Video streams from the CoastalCOMS camera network being used by Surf Life Saving Queensland are also available to the public on Coastalwatch.com, which provides live video images, wave height and swell information, daily surf reports and other news to the international surfing community. Critical to this agreement, when authorities need to take manual control of the cameras during a lifesaving incident, integration with CoastalCOMS XProtect solution allows the live images and HD video on their partner’s media site to be cut off via a software “kill switch” and replaced with other media content so as not to broadcast the command and control activities of emergency responders to the public.
FOCUSED ON PARTNERSHIPS As CoastalCOMS’ public/private cloud architecture has supported pilot projects in many countries including Denmark and the United Kingdom, and can be serviced jointly around the clock for most areas worldwide, the company has transitioned to partnering with local integrators to assist with equipment and camera installation. “We’re working with camera equipment vendors, resellers and security consultants and integrators in the United States, Australia, and South America, who have partnered with us to provide a unique solution for governments and larger private engineering and science organizations. “We are looking for partners that understand solution selling and the higher value that can come from that consultative sale. There is a disappearing line between VARs and integrators. Projects are moving beyond hanging cameras and building networks to understanding how the vertical application of video surveillance will work best, solve a complex problem, and provide the information needed to make informed decisions,” Chandler says. For more information visit www.coastalcoms.com and www.milestonesys.com. |