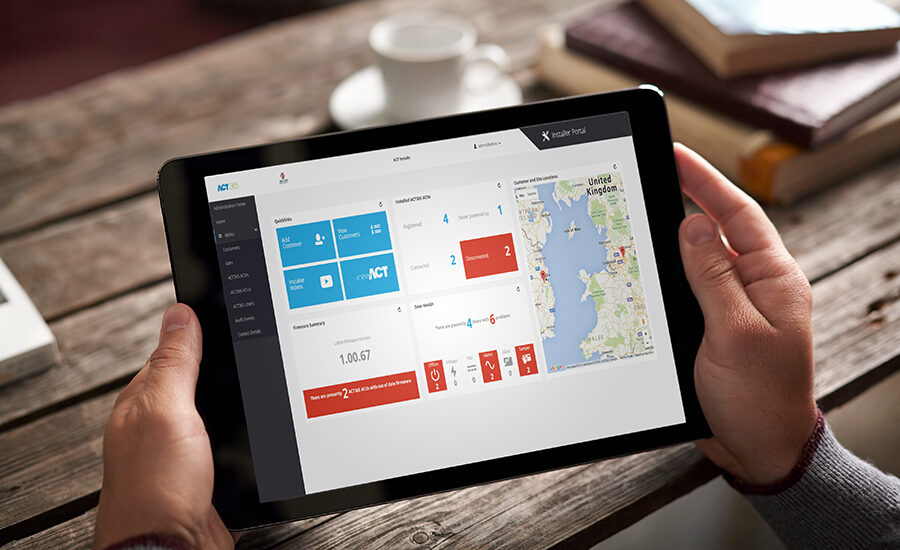
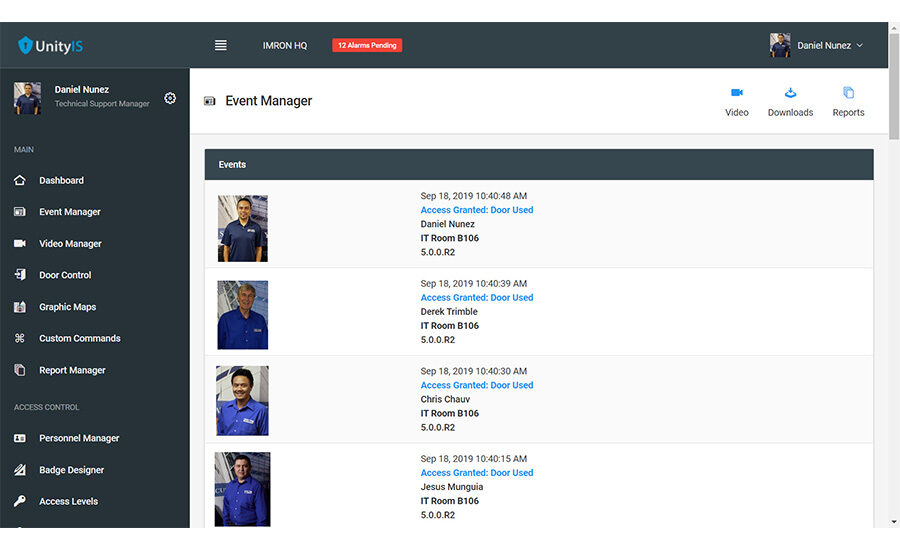
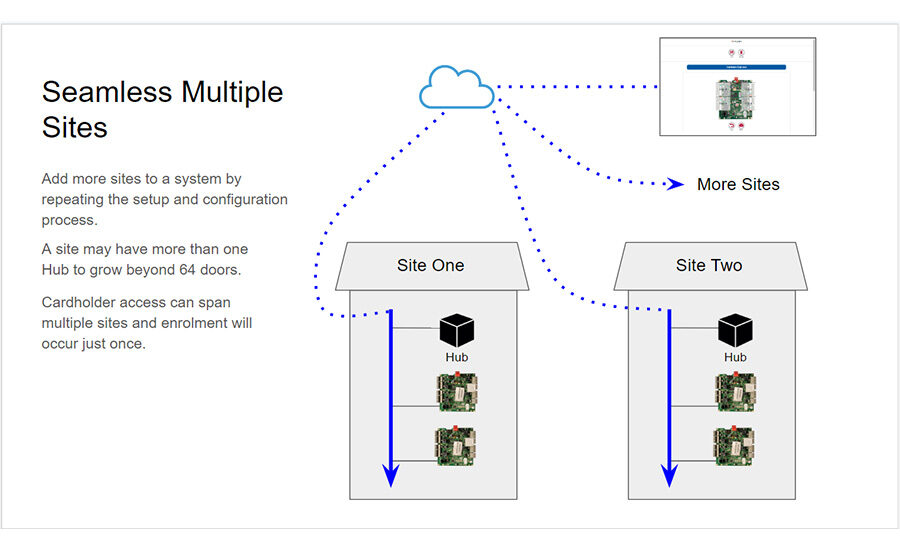
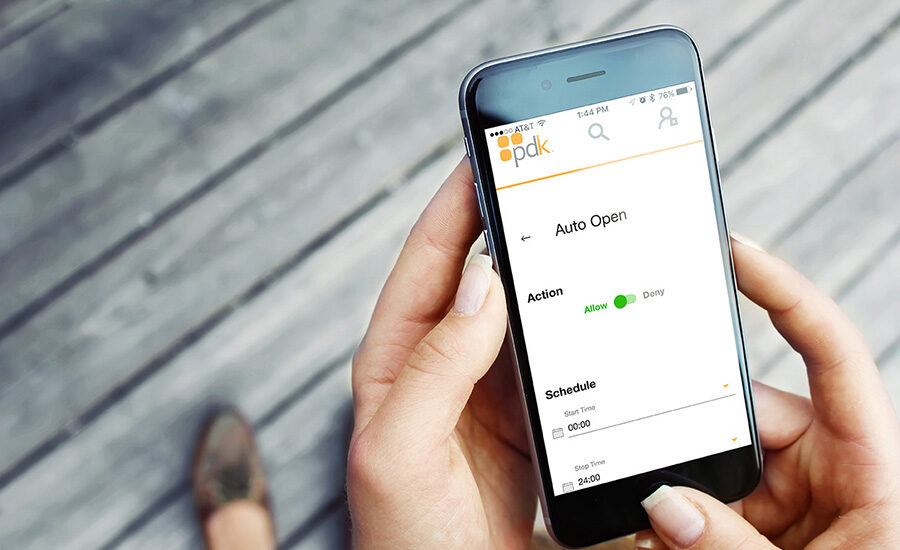
To understand how cloud-based access control can help boost your business, you first have to define what it is — and what it isn’t. While cloud-based “as-a-service” business models are beginning to proliferate across the security industry, when it comes to access control, the terms “hosted” and “managed” seem to be more common; and while these can be cloud-based, they are not necessarily the same thing as cloud-based Access Control as a Service.
“Everybody is used to the term “VSaaS” [for video as a service], but you don’t see ACaaS as much,” says Martin Renkis, general manager, cloud solutions, global security products, Johnson Controls, Milwaukee. “There is a big difference between ACaaS and hosted or managed access … Hosted or managed access control could be the same as taking your current system you have in your building that is residing on a server, unplugging it, walking it down the street to a data center and plugging it in … All you are doing is moving the hardware off-site.”
Renkis ties true cloud-based access control to the “digital transformation” age.
“What I call a cloud solution is unlimited in scale and I can instantly add or delete services on-demand. That is the number one differentiator between a true cloud-play and a hosted/managed play. True cloud is dynamically scalable.”
Brach Bengtzen, marketing manager at ProdataKey, Draper, Utah, adds, “A true cloud-based access control platform has full functionality from any web-enabled device, anytime, anywhere. That means anything that can be done from a desktop also can be completed from a mobile device, and from a fully functional mobile app. In addition, the system will be able to be updated over the cloud, with no on-site configuration or assistance needed.”
In fact, the growth of cloud-based access has in part been driven by the widespread adoption of smartphones, says Scott Lindley, general manager, Farpointe Data, Sunnyvale, Calif. “Cloud computing means storing and accessing your data and programs over the internet instead of using your computer’s hard drive. As such, cloud-based electronic access control — which is widely acknowledged to be easier to [deploy] plus more accessible and simpler to set up — directly connects door controllers to the internet using wireless mobile and/or wired protocols, such as Ethernet.”
David Barnard, vice president of sales and marketing, RS2 Technologies, Munster, Ind., sums up cloud-based access control in one word: “Freedom! For us, cloud-based access control enables the customer to grant or restrict access from a centralized platform at any time, from virtually anywhere using tools like a mobile device or through the web. The critical information related to access, including correlating video and other dynamics, can be captured within the same scope. The freedom to choose and define certain workflows your way and on the fly is what makes this an especially important transformation.”
RS2 recently announced the addition of ACT365 cloud-based access control and video management from its sister company Vanderbilt Industries (both ACRE companies), to its suite of solutions. Eric Widlitz, director of North American sales for Vanderbilt, Parsippany, N.J., adds to this definition: “The term ‘cloud-based’ is synonymous with flexible, scalable and easy to use/install.” (See this exclusive video interview with ACRE CEO Joe Grillo for more on the advantages of cloud access control: www.SDMmag.com/acre-talks-cloud-access.)
Bill Hobbs, vice president of sales, 3xLOGIC, Westminster, Colo., says the biggest advantages of cloud-based access control include,“Dramatically easier deployment and configuration, which results in lower deployment and RMR-creation costs; a full suite of features and benefits in an affordable package; and ease-of-use for the end customer, resulting in lower training and support costs for the dealer. All in all, the advantages are highly economically beneficial for our integration partners.”
Here are the top three reasons you should consider adding cloud-based access control, or ACaaS, to your portfolio if you haven’t already.
1 It Saves the Integrator Time & Money
For security integrators the first reason to add ACaaS is that it saves both time and money on both the front and back ends, with quicker, simpler installation, reduced truck rolls and easy remote troubleshooting.
“The biggest ‘pain point’ cloud solutions solve is that the integrator does not have to roll trucks to update and maintain on-premise software,” says John Moss, chief product officer, LenelS2, Framingham, Mass. “Additionally, integrators will see a reduction in the amount of time required for initial installation of the solution.” This is because there are no physical servers to install and maintain, he adds.
“In general, cloud is easier to deploy for dealers and integrators,” Widlitz says. “One of the main pieces of feedback we consistently get is how easy installation is and how much time is saved by the organizations. In essence, these entities can set up and pre-program a system on their test bench before installing it at the customer site.”
On the support end, not only do security integrators save time and resources by being able to update software remotely, but often they don’t even have to worry about the upgrades and patches, because they are managed by the manufacturer, he adds.
Cloud Security – What’s Best for My Business?
When security integrators embrace cloud technology they enable a long-term solution that when properly done allows a transitional approach with options for their customers. Moving to cloud starts with an understanding of operation and functionality. Education and research come next, honing in on what your customers are looking for and what the cloud solution offers to meet their physical security requirements. When posed to your potential cloud services provider, these five questions should provide guidance in deciding what’s best for you and your customers.
1. How robust and open is the platform?
The cloud platform you select should run on a single, open architecture to deliver faster, more secure and more reliable services. Many providers may piece together different products and services into what appears to be a single platform, but it may not be. Ask about real and specific customer uses and industry experience.
2. How many ways can I create recurring
revenue?
It’s important to select a versatile and scalable platform. For cloud-based access control, having both panel and cost-effective panel-less options bring more than one solution to choose from.
3. How does the platform help manage and grow my business?
Look for a cloud platform that helps you build your managed services business — not just support, but the technology behind it. It should prepare you for the ongoing digital transformation and the future of security contracting, or everything “as a service.” The most robust platforms offer subscriber management features with e-commerce and can help you create and manage the business side of growing recurring revenue and customer billing.
4. What features help me support my
customers?
Consider cloud platforms that provide real-time maps with connected device status and email, as well as text alerts with reporting and instant troubleshooting capabilities. Look for features such as a dashboard or map that can show you the status of every connected door, every connected camera, how many users are online, how much bandwidth every device is using and how much data in aggregate is being stored in the cloud. Consider a solution that will let you drill down into each device remotely to see CPU and local storage utilization, health status of SD storage, RAM and individual process utilization, as well as provide remote firmware upgrades, reboots, resets and other maintenance and troubleshooting features. Your cloud platform is a money saver that can prevent truck rolls and in-person maintenance.
5. What about cyber security and how do I
protect my customers?
Every platform will say they are secure, but what backs that claim? Look for organizations with experience and resources that invest significantly in cyber security annually. Consider asking how much they spend on cyber security and data privacy every year, as well as if they have a designated cyber team and how large that team is. You and your customer’s business can be dramatically affected by a cyber attack or a data privacy leak. It’s important to learn more and challenge your cloud partner to support you. — Contributed by Martin Renkis, general manager, Cloud Solutions, Global Security Products, Johnson Controls
Renkis agrees. “As the manufacturer we will update the software. Let’s say there is a new security patch; we provide those remotely updated on the system. The majority of support is all done remotely.”
Barnard puts the time-saving element in hours, or even days, over a traditional access control system. “With more on-premise solutions it can take days to install, test and finalize the installation of both hardware and software elements. With a cloud-based solution the setup can happen within hours, and can all be done remotely, which saves integrators valuable time and resources.”
In addition to time, cloud solutions also can save on cost, says Despina Stamatelos, product marketing manager for access control, Genetec, Montreal. “Any integrator when they install on-site has to invest in servers ahead of time and wait to be paid by their customers,” she explains. Cloud eliminates that from the equation.
2 It Makes Customers Happier
End users large and small are starting to be aware of and interested in all things cloud, and access control is no exception. While it may have started in SMB, enterprise users are also now considering ACaaS, because it solves several pain points for them, from cost, to ease of use, to helping with cyber security issues.
One of the biggest benefits is the operations versus capital expense, Stamatelos says. “For the end user it is about up-front cost versus recurring on a monthly basis. They don’t have to invest in IT infrastructure or an individual to manage that. A lot of companies are downsizing so not having to manage that is a huge deal.”
In fact, Stamatelos recalls meeting with an end user at GSX this year who was trying to take everything to the cloud because they were downsizing their office space. “They loved the fact that they could take access control to the cloud,” she says.
Barnard adds, “Cost can be prohibitive when a business is investing in on-premise storage-related and access control hardware, as well as software to provide real-time updates. That up-front infrastructure investment cost is reduced significantly when businesses shift to a cloud-based, service-based solution through a dealer or integrator partner.”
Cloud also helps keep the end user current, says Vince Deiuliis, director of marketing and national accounts, Keri Systems Inc., San Jose, Calif. “There is more emphasis on having the latest software, automatically. With the browser/mobile apps, the user is not restricted to being at the physical location to manage their system. It also removes the chore of local server maintenance from the end user.”
And since much of cloud-based access control is mobile-based, an increasingly popular added benefit to the customer is the ability to use mobile credentials, saving money and aggravation of issuing and tracking physical cards.
“These solutions are giving users the ‘digital cohesion’ of opening doors with their smartphone apps, as well as authenticating to enterprise data resources or accessing a building’s applications and services,” says Stephen Carney, vice president of product marketing for physical access control at HID Global, Austin, Texas.
“From the customer’s perspective some of the biggest pain points are plastic cards,” Renkis adds. “It’s not just about inventory, but about the security risk.”
Cards can be duplicated, and that is just the tip of the iceberg when it comes to the cyber risk many particularly older traditional access control systems can potentially pose.
Many experts agree that cloud technology is at least as secure, if not more secure than the typical on-premises solution.
While both types need to be cyber-secured equally, there is one advantage to cloud architecture, Stamatelos says. “With access control in the cloud, any time we have an upgrade we simply push it to the customer so they are always up-to-date.”
Renkis takes it even further. “I would posit that cloud-based solutions are significantly more secure than on-premise solutions. The amount of investment that Johnson Controls makes in cyber security — along with our partners like Microsoft, Google and Amazon — is significantly more than any single company is going to be doing on its own. Let’s say you have a small company. Would you trust your IT team or JCI, along with Google and Amazon, who are working on hardening this every day?”
John Szczygiel, executive vice president and COO for Brivo, Bethesda, Md., says his company’s solution automatically monitors for a variety of conditions, such as communication failures and malicious activity. “All of the remote services enabled by our cloud infrastructure generate happier end users and less maintenance costs for our integrators.”
3 It Creates RMR & Opens New Business Opportunities
Perhaps the greatest reason many security integrators are starting to explore cloud-based access control is for the recurring monthly revenue (RMR) potential it brings. But beyond that, it can also open up new markets.
“At the core of the advantage for the dealer or integrator is the opportunity to harness additional revenue with a recurring revenue business model,” Widlitz says. “The recurring revenue allows these partners to better predict incoming revenue, which can help with planning resources and other allocations. Second, the cloud brings a new market to the forefront, as the solution is suited to small- to medium-based businesses without a robust IT department or support network. For a long time this segment of the market was overlooked in favor of large-scale enterprise customers and projects. With the addition of cloud within an integrator’s portfolio, a broader base of business can be secured.”
While it is true enterprise customers are interested in cloud, the largest base of cloud business is still the SMB market, and within that, the opportunities to offer even more services abound.
“Integrators can benefit from the ability to remotely manage a client’s support requests and troubleshoot as needed,” says Cody Flood, senior director of sales, Arcules, Irvine, Calif. “This seamless service, without the expense of an on-site visit, helps integrators establish a strong and trustworthy long-term relationship with the end user.”
An RMR-based model also helps in predicting revenue, Stamatelos says. “Budget cycles are long and it can take a long time to get paid. Cloud increases cash flow because you get paid on a monthly basis … You have the security of knowing you have RMR on a monthly basis.”
Renkis calls cloud-based access control a “business model helper,” although he acknowledges it does present some challenges. “The right cloud platform has subscription and revenue management and gives them a tool to make money. We are helping them run their businesses better and make more money in selling subscriptions and manage that revenue.
“On the challenges side, moving to a subscription-based model is a business conversation with the dealer or integrator. They have to change how they look at things and that can be painful.” (See “Cloud Security — What’s Best for My Business?” on page 50 for more on making this switch.)
While adding or shifting to a cloud-based access control model may not be easy, it is worth it to at least try, say the experts.
“It’s critical for integrators that are selling and managing cloud-based access control systems to invest in learning as much as possible about how the cloud works and how it can benefit your customers,” Flood says.
Stamatelos agrees. “They need to start educating themselves and start learning the benefits of access control in the cloud and how it can benefit them and their customers,” she says. “They should understand the market is going to the cloud and we will see an increase in the next few years.”
Fawzia A. Atcha, Ph.D., vice president of IMRON Corp., Irvine Calif., predicts that cloud-based access control will overtake on-premise solutions as the former continues to gain traction. “In the meantime, when a dealer or integrator includes a cloud-based solution in their offerings to an end user, this opens up choices that the end users may not have had otherwise. End users want to spend as little time as possible on maintaining, configuring and accessing software in defining and utilizing access control points. Minimizing this process and providing ease-of-use will undoubtedly garner awareness and interest.”
The most important thing, Widlitz says, is to not be afraid of cloud and to seek out partners who can help. “Try it! A lot of people seem to be either afraid of cloud-based solutions or intimidated by shifting to the RMR model, but all of this can be easily addressed with the right manufacturer partner … All of the dealers and integrators who have invested in our cloud-based access control solution have bought it again … The feedback we have gotten is across the board positive and that it is overall more cost-effective for all parties involved.”
More Online
For more on cloud-based access control visit SDM’s website, where you will find the following articles:
“The Bigger Picture of Enterprise Access Control”
www.SDMmag.com/the-bigger-picture-of-enterprise-access-control
“The State of the Access Control Market in 2019”
www.SDMmag.com/state-of-the-market-access-control-2019
“How to Find Managed Access Success”
www.SDMmag.com/how-to-find-managed-access-success
“What Do You Know About Cloud-Based Access Control?”
www.SDMmag.com/what-do-you-know-about-cloud-based-access-control