In today’s interconnected security industry, there are more cameras, IoT, and edge devices “talking” to each other than ever before. Modern IP cameras have powerful processing, networking, and storage capabilities that make them incredibly versatile, while cloud technology enables more data storage, and the internet connects them all.
But there’s a downside to all this progress: more devices, cloud usage, open source software components, and internet connection also means more exposure to cyber risk.
More IoT devices, a larger cloud presence, and ransomware converge to create a bigger cybersecurity threat in video surveillance, says David Brent, senior cyber and data security training engineer for North America, Bosch, Fairport, N.Y. Hacks are on the rise because of more remote work, and with an estimated 38.1 billion IoT devices now on the web, with public-facing IP addresses and open lines, hackers can do a lot of damage, he says.
“When left unsecured, IoT devices such as network cameras inevitably increase the attack surface,” says Dr. Peter Kim, global technical consultant at IDIS America, Coppell, Texas. “The sheer volume of IoT devices that have been added to an organization’s network, often without involvement of the IT department, has certainly increased concerns and vigilance.”
The transition from analog to IP in video surveillance has contributed to increased cyber risk. “Ever since IP-based systems and cameras started dominating the video surveillance industry, we have seen a growing rate of cyber-related issues,” says Guy Arazi, director of product development at Vicon, Hauppage, N.Y. “Cybersecurity issues are also affecting the general IT side of the house, but the transition from analog to IP in the video surveillance industry may have created a knowledge gap that does not exist on the network-savvy IT world.”
Edge devices such as cameras, network video recorders, and encoders are more prone to hacking, Arazi says. While the primarily Windows- and Linux-based servers running official operating systems are regularly updated by the OS manufacturer to address loopholes and security gaps, IoT-type devices depend on the specific manufacturer following up and providing firmware updates — which don’t always arrive fast enough and typically don’t auto-update, he adds.
More complex devices that can do more are especially prone to hacking. “The challenge in the industry is the components used in video surveillance systems have traditionally been neglected and not upgraded as steadfastly as other components in a corporate IT system,” says Dean Drako, founder, president and CEO, Eagle Eye Networks, Austin, Texas. “A video surveillance upgrade process would require taking down the system, which might be different in every building and not necessarily wired into corporate IT, so it’s often neglected.”
Cameras have always been a target because they give an attacker a way to view what is going on at a certain site, says Steffen De Muynck, senior product manager, Teledyne FLIR Security, Wilsonville, Ore. “This information in the wrong hands can be used to facilitate breaking and entering, blackmailing, and much more,” he says. More insidiously, “The security cameras can also be used as a stepping board to attack other assets in the network of a customer, or can be used to form a botnet that can simultaneously attack a specific target,” he adds.
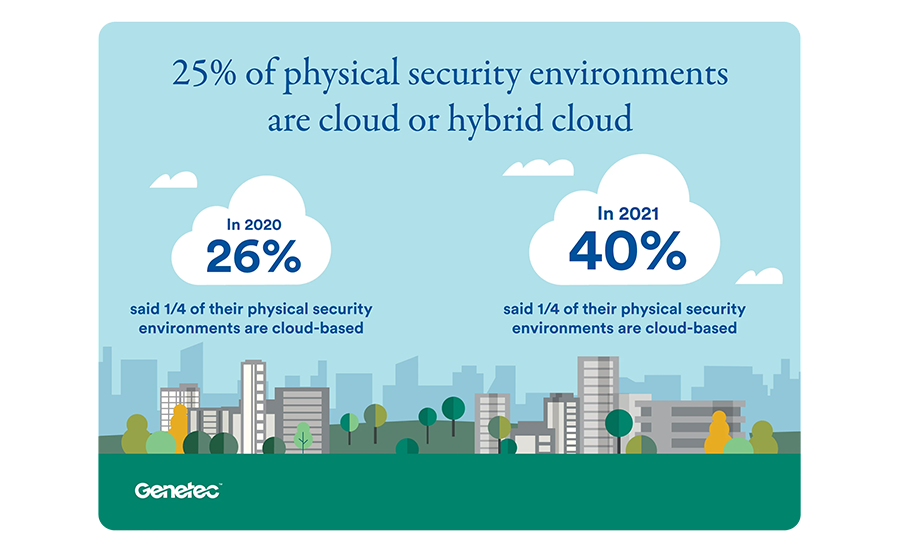
More businesses are reporting that a quarter of their physical security environments are in the cloud or a cloud hybrid, according to Genetec's "State of Physical Security 2021" report. // IMAGE COURTESY GENETEC
Over the last several years, there have been some dramatic examples specific to the security industry, with several top manufacturers grappling with hacks that arose from IP camera breaches. One of the most recent attacks required the manufacturer to shut down all systems to limit the fallout. And one of the biggest security camera hacks exposed footage from more than 150,000 connected cameras in use inside schools, jail cells, hospital ICUs, and major corporations.
“Not properly securing IP cameras and other devices by allowing them to be directly accessible from the internet is the biggest source of cyber risk in video surveillance,” says Chuck Davis, vice president, global information security at Hikvision, City of Industry, Calif.
Bud Broomhead, CEO of Viakoo, Mountain View, Calif., agrees. “The IP cameras themselves are the biggest source of cyber risk. In reality, these are powerful Linux servers, sometimes hanging outside a building with exposed ports — of course, threat actors see them as the low-hanging fruit when breaching an organization.”
The Pandemic Plays a Part
Just as it affected so many other areas of life, the global pandemic and an increase in remote work upped the ante on video surveillance cyber risk — and cybersecurity in general.
According to Genetec’s “State of Physical Security 2021: Adapting to an Uncertain Future,” cybersecurity will be a top priority for businesses in 2022. Thirty-six percent of respondents globally are looking to invest in cybersecurity-related tools to improve their physical security environment in the next 12 months.
In last year’s report, organizations named their top challenge as managing employee and visitor safety. This year, visitor management dropped to No. 5, with cybersecurity taking over as the No. 1 challenge. A reason for this is that more employees are working remotely, and as a result, more organizations are seeing an increase in cyber-crime.
“Throughout the COVID pandemic, the world saw an exponential rise in the frequency of ransomware attacks, with many aimed at schools and universities,” Kim says. “In some cases, their video was connected to networks, and many chose to rebuild, including backups, rather than paying ransomware demands. … This meant they not only suffered severe impacts to learning continuity over weeks and even months, but they were left without surveillance monitoring or recording, leaving them vulnerable to physical security threats or the ability to meet insurance requirements, health and safety obligations, duty of care and related compliances.”
Weaseling Into the System
While there are several ways hackers can wreak havoc once they’ve weaseled into a system, the primary threat comes from using access from cameras to move laterally into the corporate network.
To hackers, video surveillance systems are not an end in themselves, but rather a “vector to potentially get into the network and thereby get access to other things; that’s the real threat or concern around cybersecurity for video surveillance,” Drako says. “It’s an access point to the network where they can sift around and try to find other things that are not properly secured, like laptops or customer databases, where they can encrypt everything for ransomware.”
Once the bad guys get in, things can get really ugly. “Backdoors allow hackers to strike using a range of Mitre malware variants, which then issue system commands,” Kim says. “Others, such as Minikatz and ELoader, are designed to steal usernames and passwords, while REvil is a ransomware family designed to encrypt data and drives to extort payments. And these are just some of the most popular types of malware and ransomware we’ve seen increasingly used in the last couple of years in various guises.”
While the malwares’ names may change, the games are mostly the same. Ransomware, which hackers install on a computer or device after gaining access through a successful phishing attack, is still the No. 1 threat, Hikvision’s Davis says. “Ransomware quietly encrypts all of the files and folders on your computer, and any data on connected USB or mounted shared drives, and then uploads the decryption key to the threat actor who tricked you into installing the ransomware,” he says. “You’ll only receive the decryption key from the ransomware threat actor after paying the ransom fee.”
The scam is so popular that ransomware as a service (RaaS) is now a viable business model on the dark web, with organizations like Conti Group structured and running it like a legitimate business, Brent says. (A recent article in ThreatPost describes the group as offering bonuses, employee of the month, performance reviews, and top-notch training — with many of its employees believing it’s a legitimate business.)
Often hackers gain access through spear phishing, accessing a company’s org chart and impersonating executives to get users to click on links in what looks like a legitimate request. Impersonation of corporate executives in email can help hackers misdirect money by using stolen information about the executive to make the spear phishing emails look real, Drako says.
And then there’s the growing threat of deep fakes, which involve malicious editing of video acquired from surveillance systems, Kim says. “Malicious editing represents one of the fastest-developing threats to the credibility and value of video surveillance solutions. … Malicious actors can weaponize an organization’s own recorded footage against them. Every interaction and incident recorded by a video security camera on a site can now easily be altered if the integrity of that footage is not protected with the right technology and falls into the wrong hands.”
Fixing the Vulnerabilities
The only upside to all this criminal activity is that high-profile breaches have made customers more aware of the need to put cybersecurity first when purchasing or upgrading a video surveillance system — and it’s made manufacturers more vigilant about troubleshooting their products.
“In recent years, system and network administrators have become more informed about certain vulnerabilities associated with current video surveillance systems, and have raised the security level accordingly,” Arazi says. “This, combined with steps taken by the manufacturers, has resulted in safer practices and ultimately a more secure system.”
But end users are still ultimately responsible for securing their video surveillance systems. Rotating passwords, using strong user IDs and multifactor IDs, updating camera firmware or OS, patching vulnerabilities quickly, and using certificates are the basic steps customers can take to secure their cameras and video surveillance systems.
“The biggest trend I’m seeing is to bring IT security best practices into physical security systems,” says Mathieu Chevalier, principal security architect and manager, Genetec, Montreal. “The reason for this is the convergence between those worlds. More IT systems are being used for physical security protection … and cameras are becoming more like computers, with lenses that can send video back to the network.”
For their part, manufacturers are doubling down on penetration and third-party testing to help find and fix vulnerabilities. “The top trends we are seeing in securing video surveillance systems against cyber risk include the hardening of edge devices that sit on the IP network, such as cameras and other devices like speakers,” says Kirk Tashjian, product manager, video systems, Identiv, Santa Ana, Calif. “We are continuing to follow the cybersecurity trend of protecting computer hardware the same way the entire IT industry protects other infrastructures. We are also engaging third-party experts to support the hardening of computer equipment and edge devices.”
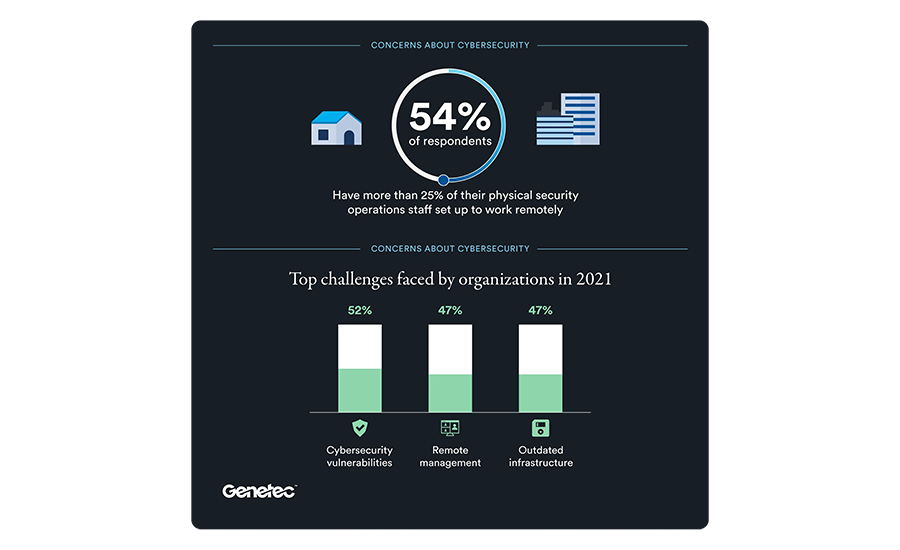
Cybersecurity was one of the top challenges named by organizations in 2021, with 52 percent of respondents pointing to cyber vulnerabilities as a prime concern, according to Genetec's "State of Physical Security 2021" report. // IMAGE COURTESY GENETEC
When selecting a vendor, end users and security integrators must do their homework on how stringent they are about cybersecurity for their products. “If I’m looking at a vendor, I want to know if they’re using secure engineering process (SEP), just from a certification standpoint,” Brent says. “If they have SEP, that means everything they do before releasing a product has been tested.” Other boxes to check are whether the vendor conducts internal and external penetration testing, who produces the product’s CVEs (common vulnerability and exposures), and if they’re using vulnerability scanners that show IP addresses and which ports are open on specific products, he adds.
Standards compliance is another way manufacturers can keep products safe. National Defense Authorization Act (NDAA) standards helped increase the cybersecurity of many government and federal loan recipient implementations by banning the use of specific Chinese products that had been prone to vulnerabilities for years, Kim says. Additionally, a proposed FCC ban that will extend that protection for smaller organizations will also help if imposed later this year, he says.
NIST 800, primarily used in corporate or government network deployments, is a technical standard set of publications that details United States government procedures, policies, and guidelines on information systems. And the Security Industry Association (SIA)’s Security Industry Cybersecurity Certification (SICC) is the first industry-focused credential specifically for cybersecurity in physical security systems, Kim says.
Additionally, the Biden administration in 2021 signed an executive order to improve cybersecurity with the specific goals of enhancing software supply chain security, improving detection of and response to cybersecurity vulnerabilities and incidents on federal government networks, and modernizing federal government cybersecurity with tools like a safety review board, says Davis of Hikvision.
However, cyber threats are constantly changing, and the industry must stay ahead of the curve on emerging threats. “It is all a risk,” Tashjian says. “Everything needs to be watched and protected, from edge devices to the computer sitting in the server rack. Following a manufacturer’s prescribed hardening guides is key to having a successful system free from the risk of cybersecurity issues.”