In the post-pandemic era of Amazon, Uber Eats and DoorDash, visitor management has risen in prominence. Whether it’s a third-party service provider, an interviewee or a remote worker who needs to be onsite, organizations have a need to allow restricted access for one-time visitors. Not only that, but they need to track the when, where and why. Their need spans the health and safety of individuals as well as the safety of their property and information. And organizations have moved far beyond a pen and logbook system.
“Managing visitors is a vital process for organizations to ensure the safety and security of their property,” says Matthew MacIntosh, product manager, hosted solutions, AMAG Technology, Hawthorne, Calif. “It involves defining a set of procedures to regulate the entry of people who visit the property on a temporary basis. Visitors can pose a unique challenge to organizations, as they may be unknown to them. While some contractors or vendors may be familiar with the organization, most visitors are not.”
The COVID-19 pandemic changed the world; but in many ways it changed the world of visitor management for the better. “Reconsidering a visitor management solution initiated much-needed change and pioneered better workplace efficiencies, which are here to stay,” says Ana Bravo, senior manager, IAMS, HID Global, Austin, Texas. “The pandemic exposed the obvious issue when it came to managing building capacity in accordance with government restrictions. The ad-hoc visitor registration and preparations processes could no longer suffice in a time of capacity control.
“With reduced staff, smoothly running the front lobby and ensuring that all visitors were correctly pre-registered before entrance was a struggle,” Bravo continues. “There was also a demand for better insight into the actions of visitors within the buildings so that the organization could accurately create reports and monitor contact tracing. Once implemented, many viewed the benefits of visitor management and the many applications to manage building traffic efficiently and safely. Many of these changes are still in place.”
Visitor Management Products
Throughout the article, SDM will highlight some of the visitor management solutions currently on offer.

HID SAFE Visitor Manager
HID SAFE Visitor Manager automates the entire lifecycle of visitors of any organization. This completely web-based solution includes capabilities for visitor pre-registration, security and background checks, access authorization, check-in/check-out, badge printing and centralized reporting, and audit trail functions. HID SAFE Visitor Manager is an extremely flexible solution that can be easily configured for each customer’s unique visitor management requirements. This highly scalable solution allows for easy management of busy sites with high volumes of visitors.
Check-In Time
Right now, there’s quite a bit of technological momentum in the market. Concerns over time to check-in have long plagued visitor management, but Bravo highlights pre-registration and check-in with pre-approved access QR codes, contactless check-in, cross check with external and internal watchlists, real-time background checks and immediate attention to denied and restricted parties as some of the technology that is relieving that pressure point.
“Mobile applications have also become more common, allowing remote management and pre-registration of visitors to further ease the registration process,” says Andrea McCabe, solutions marketing manager — visitor and workplace solutions, acre security. “We’re also seeing cloud-based systems increasingly favored for their scalability and ease of integration. But this is only the beginning. Given the field’s rapid evolution, newer developments are likely to continue to have significant impacts on this product sector.”

Symmetry Guest
Symmetry GUEST from AMAG Technology operates on a PC, tablet or smartphone, making it easy to manage data anywhere, anytime. It also comes pre-installed in three kiosk styles. It is available as a web-hosted SaaS or on-premise solution to fit any business need. Make a visitor feel welcome by sending an email prior to their visit to put them at ease. Employees pre-register visitors using Outlook or Gmail. Visitors receive a welcome email that can include travel or arrival instructions, a map, parking or other pertinent information. Providing information ahead of time provides a great visitor experience. Upon arrival, visitors can check into a Symmetry GUEST Kiosk using a QR or barcode that was sent to the visitor’s smartphone. The host employee is notified by email or text when their visitor arrives and can greet them. Streamlining the process means less wait time and happier visitors.
And Greg Tomasko, applications engineer leader at Honeywell Security, Huntington, N.Y., points to another problem end users face when checking in guests. “It's a little tough with visitors because the organization can’t control what device they’re going to bring to the table. Whether it’s an Android, iPhone, iPad or a piece of paper that they printed from their iMac sitting at home from 1997, you never know what’s going to happen with visitors and you can't control that,” he says. “And we shouldn’t. So we have to kind of make it open and scalable to whatever is coming up to the building.”
MacIntosh adds, “Storing information on past visitors can also speed up the process for repeat visitors, and facial recognition technology can help receptionists find their records quickly. Self-registration kiosks are another option to limit the time visitors spend with receptionists. Automated check-in or check-out based on time, location, or user action can also help visitors quickly get to their destination without stopping in the lobby.”

HID EasyLobby
EasyLobby is designed for small to medium size organizations looking to transition from pen and paper guest books or spreadsheets to an on-premises visitor management solution. Allowing guests to self-register via tablet, automatically print visitor badges and notify hosts of guests’ arrival streamlines the visitor experience.
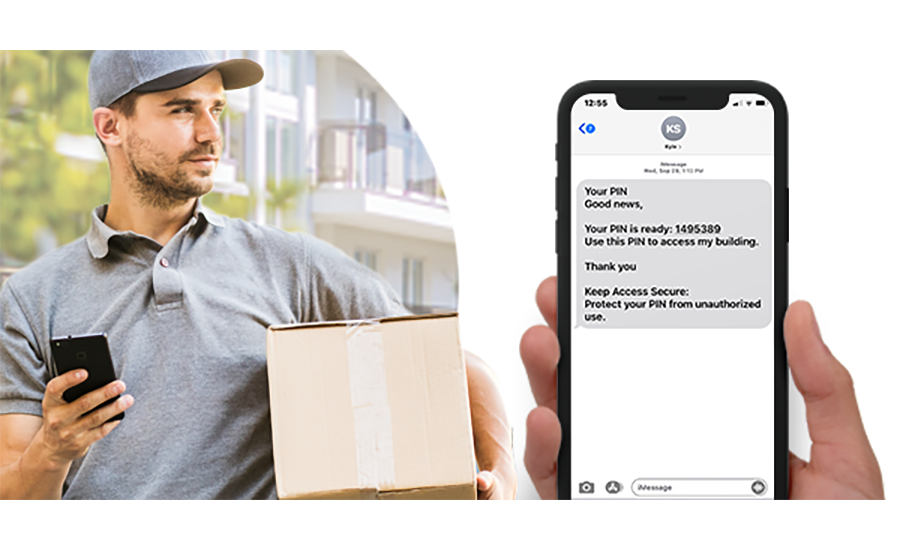
dormakaba Resident Visitor Management
dormakaba’s Resident Visitor Management is a PIN code, RFID transmitter, and mobile key solution that gives residents the flexibility they require when it comes to ingress for guests and service providers. The solution gives property managers the control they need and residents the flexibility they require.
One of the most familiar recent technological advancements in any industry is artificial intelligence (AI). While AI has found its way to this market, how is it being utilized? “One example is the advancement of facial recognition technology, which is making the check-in process smoother and more efficient,” MacIntosh says. “Additionally, analytics tools are providing organizations with valuable insights into how their building is utilized, such as which floors or departments are experiencing the most traffic and when the busiest times are. This information allows them to make informed staffing decisions.”
Collecting Data
Whether it’s understanding traffic, utilization of facilities, contact tracing or if it’s agreements, documents and compliance, data collection is a valuable component of visitor management. In fact, McCabe says, “Data collection is a fundamental component of visitor management, and technological advancements are being designed to improve the precision and efficiency of this process.
“For example, digital sign-in sheets have replaced traditional paper logs, offering instantaneous data input into organizational databases,” McCabe continues. “Smart badges equipped with RFID and NFC technologies enable real-time tracking of visitor movements and interactions; while IoT devices capture metrics like visitor flow and dwell times. Mobile applications can also collect additional data directly from visitors, including feedback and post-visit surveys and facial recognition and biometric technologies offer ways to gather analytical data for pattern recognition.”
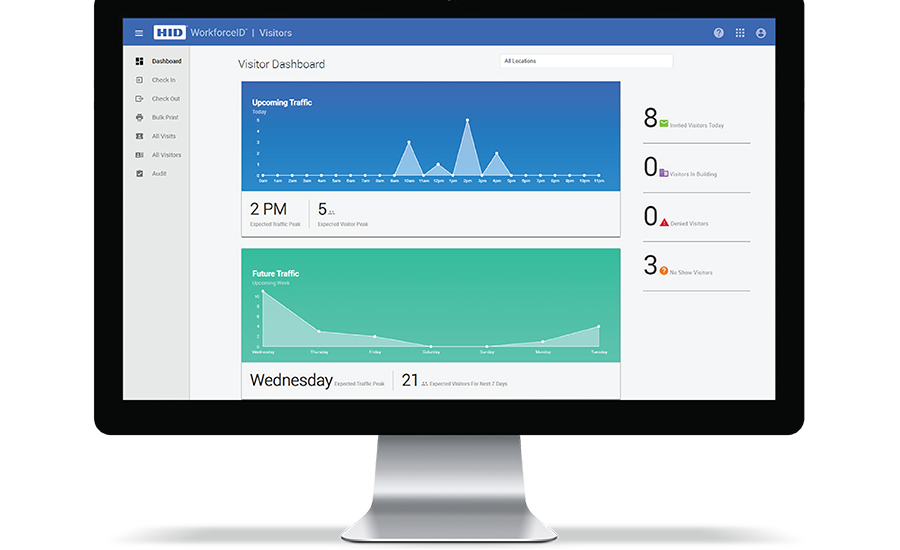
HID Visitor Manager
HID Visitor Manager enables a touchless visitor experience and creates a great first impression as an easy-to-use cloud-based solution. Visitor Manager allows users to welcome visitors with flexible workflows and an intuitive experience, and takes the administrative burden off your staff. It also makes a great first impression and extends identity management beyond visitors to contractors and vendors.
As for the benefits of this, MacIntosh says, “This integration can offer building utilization information and patterns of returning visitors, similar to those of employees. Such insights can help identify potential risks posed by visitors and provide a better understanding of the utilization of company resources and property.
“When considering data collection, it is important to recognize that it encompasses more than just personal information,” MacIntosh continues. “It also includes documents and questionnaires. Such data collection can serve as both a source of feedback and a tool for compliance. Furthermore, policy management enables organizations to confirm that visitors have read and consented to policies as well as signed any required legal documents, like waivers or NDAs.”
Restricting Access
While an organization can restrict access with scanners and badges — or actually chaperone its visitors through the building — AI has proven that it can provide additional help in identifying suspicious behavior. “Artificial Intelligence and machine learning algorithms are being used to identify suspicious activities while integration with IoT devices like smart cameras and badges enables real-time monitoring and data collection,” McCabe says. “Advanced algorithms play a crucial role in monitoring visitor conduct to identify any suspicious activities.”

acre’s TDS Visitor
The TDS visitor management solution from acre security is now Google Chrome Enterprise Recommended. It was selected to help businesses further maximize their Google Enterprise investments. The TDS visitor management solution seamlessly integrates with Google ChromeOS deployments, empowering organizations to strengthen their security compliance measures while making visitor management processes like registration, check-in and check-out more efficient. TDS Visitor Management also offers businesses access to the latest Chrome Enterprise features, ensuring an intuitive and user-friendly experience for visitors and employees alike. Google Chrome's Enterprise Recommended program is a distinctive initiative aimed at aiding enterprises in discovering technologies that boost web and cloud performance.
Some experts, however, caution against the replacement of the human element when implementing AI. “[You] have to be a little careful with large language models and the replacement of human intelligence because you never are 100 percent sure, once an autonomous item is there, how that human to digital interaction is going to go,” Tomasko says.
Bravo says, “Some companies expect AI to eventually manage visitors without a person behind it, but the ideal solution is an extension of [a] company and employees; visitors can be important customers whom [they] would like to offer the best experience while enhancing security. AI can assist in predicting traffic, offering analysis etc., but a visit should connect to a person and should have that human feel.”
HID SAFE Intelligent Patient Visitor Management
The HID SAFE Intelligent Patient Visitor Management (IPVM) solution allows organizations to improve the visitor and patient experience, secure sensitive areas and create an environment for your staff and your community to heal. It increases front-desk efficiency and the visitor experience with self-services tools, like check-in/check-out kiosks and web portals for inpatients, outpatients and visitors. It also adhere to CDC, local health department, Joint Commission and HIPAA rules and regulations with standard policies and reports that streamline audits. And it improves workplace safety with watchlist notifications, flexible visitation policies and prevention and response capabilities.
Visitor Management’s Value
According to Tomasko, visitor management is one of the biggest untapped options for upselling in the end user scale. But why is it so untapped? “Number one, you have to overcome the cost of doing nothing,” Tomasko says. “I can run to Staples and get a pen and a notepad in two minutes and have a visitor management system.”
And to do so — to rely solely on a log system — would be to underestimate the added value of today’s visitor management offerings. For visitors, a smooth and seamless check-in and screening process can create a great first impression. Intuitive solutions can also improve the experience for the visitor’s contact point. “Visitor management goes beyond a front desk app, this solution promotes customer satisfaction, security and compliance,” Bravo says. “It’s not enough to offer an easy tablet check in tool. A visitor management solution should be able to manage data, integrate with other internal systems, provide alerts and reports.”
Bravo continues, “Too often we see a simple app managing facilities traffic that can’t offer watchlist cross reference, pre-registration, reporting, emergency alerts or broadcast messages or are completely stand alone. These won’t help you enhance security or support compliance. It’s time to offer a true solution that can manage today’s needs and expectations.”
That’s a sentiment echoed time and time again by experts. “A robust visitor management system offers numerous advantages beyond mere data collection, serving as a tool to bolster a company’s reputation through streamlined, professional interactions,” McCabe says. “It further aids in fulfilling legal requirements by providing precise records that can be used during audits or legal proceedings. Understanding visitor patterns also enables the smarter allocation of resources, leading to cost efficiencies across the organization.”




