NETWORK FUNDAMENTALS ARE PREREQUISITE KNOWLEDGE
I am a bit confused about the various devices used in networks. Can you shed some light on this?As the use of network-based systems increases, security company managers must make sure that their technicians have a firm grasp on the components and interconnection tech-niques that are employed in typical data networks. In many cases the network already will be in place or it will be maintained by others, but because IP cameras and digital recorders have network connections it is important to understand the basics of network topography.
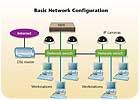
The diagram, Basic Network Configuration, at right, shows a simple network utilizing a DSL Internet connection and two switches for device connections. All cables used are CAT5e or better.
A hub is probably the most common connection point for devices in network. Hubs are commonly used to connect devices to a LAN or segments of a LAN. A hub contains multiple ports (4,8,16, etc.) for device connection. When a packet arrives at one port, it is copied to all of the other ports so that all segments of the LAN can see all packets. A passive hub serves simply as a conduit for the data, enabling it to go from one device (or segment) to another. So-called “intelligent” hubs include an additional feature that enables an administrator to monitor the traffic passing through the hub and to configure each port in the hub. Intelligent hubs are also called manageable hubs.
A switch is a network device that filters and forwards packets between LAN segments. Network switches appear and are used nearly identically to network hubs, but a switch generally contains more intelligence than a hub. Unlike hubs, network switches are capable of inspecting data packets as they are received, determining the source and destination device of that packet, and forwarding it appropriately. By delivering each message only to the connected device it was intended for, a network switch conserves network bandwidth and offers generally better performance than a hub.
A router is a device that forwards data packets among networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP’s network. Routers are located at gateways, the places where two or more networks connect. Routers use headers and forwarding tables to determine the best path for forwarding the packets, and they use protocols to communicate with each other and configure the best route between any two hosts. By maintaining configuration information in a routing table, wired or wireless routers also have the ability to filter traffic, either incoming or outgoing, based on the IP addresses of senders and receivers. Some routers allow the network manager to update the routing table from a Web-based browser interface. Broadband routers combine the functions of a router with those of a network switch and a firewall in a single unit.
I have an NVR connected to a LAN and want to connect it to the Internet. How can I do this?
Connecting an NVR to the Internet follows the same procedure that is used for any other computer. The only difficult part is to set the right parameters in the firewall.
In order to have this simplified you need a plan of exactly what you want to do. If you want to have a remote view client using the Internet to access the NVR, then you’ll need to find what ports are used by the remote view software used to access the NVR.
If you want to have cameras on sites other than your LAN, then you’ll also need to know what ports are used by cameras to transmit video and receive pan-tilt-zoom (PTZ) data, if necessary.
After the necessary information is collected, the only task left is to program the router with all of the information so it will know how the packets are sent. The easiest way, but also the most unsecured way is to set the NVR as a DMZ host. This will allow unfiltered incoming and outgoing traffic for the NVR. The recommended and more secure way is open on your firewall only the necessary ports for the NVR to function as you desire. Each manufacturer decides what port to use for its own equipment and application, which makes impossible to have a standard set of port assignments.
Bear in mind that when an NVR is connected to the Internet via a LAN it actually has one IP address, which is used to access it from the local network, and a second “external” IP address, which is used to connect over the Internet. Typically, the NVR is programmed with the local IP address.
MESH MAY BE BEST FOR WIRELESS IP
Can I use wireless devices to connect IP cameras?Wireless IP cameras are always a good solution to installing cameras in places where it is almost impossible or very expensive to run cables. Because IP cameras can operate using standard network devices, any wireless node or device is capable of transmitting the signals.
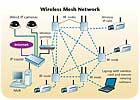
One of the most common technologies used today for large wireless video surveillance systems is mesh wireless technology. Whether installed as part of a local security system or a large citywide project, mesh technology enhances the economics of video surveillance and makes it deployable on a cost-effective basis. Mesh technology allows the installation of video networks, quickly, at a fraction of the cost of traditional wired IP video solutions. Many large video security applications for manufacturing, schools, or industrial plants have often been viewed as uneconomic due to long cable runs or environmental considerations, but mesh-based alternatives can deliver quality digital video surveillance at a fraction of the cost of conventional wired systems, quickly, and with good scalability.
The diagram, Wireless Mesh Network, above, is a basic illustration of a wireless mesh network established for video surveillance. This same network can be configured for monitoring alarm systems, VoIP, and even Internet service at the remote locations, which can help offset the initial cost of installing the devices.
ANALOG VERSUS IP CAMERAS
What is the difference between an analog camera and an IP camera?An analog camera at high resolution (4CIF) has a significant problem with interlacing. This is because with an analog video signal, even when connected to a DVR, all images are made up of lines, and each image is formed from two interlaced fields. When an image has a lot of movement, the image will become blurry. A network camera employs progressive scan technology that better suits depicting moving objects clearly. This more advanced image capture technology means that the whole image is captured at one time, thus providing crystal clear images even with a high degree of motion.
Getting power to an analog camera has always been a major obstacle and cost. The IEEE 802.3af standard for Power over Ethernet (PoE) has proven to be quite successful due to the tremendous cost savings it offers. Not available for analog cameras, PoE means that networking devices get power from a PoE-enabled switch over the same standard CAT5 cable that transmits data and video.
Analog cameras are limited by the NTSC/PAL specifications, with a resolution corresponding to 0.4 megapixels at 4CIF. For newer high-resolution computer screens and digital cameras, end users now require resolution in the higher megapixel range – a requirement that end users are starting to demand for surveillance applications, as well. A network camera’s higher resolution provides more detail and can cover larger areas. This ensures the security system investment will not be wasted because a perpetrator’s face or what he is carrying cannot be discerned. Also, the network camera’s increased resolution enables functions such as digital PTZ.
In a world in which far too much video is being recorded for anyone to ever monitor or search, intelligent video is the next great trend. To accommodate such demands, the advanced network cameras can have standard built-in motion detection and alarm management so the camera decides when to send video, at what frame rate and resolution, and when to alert a specific operator for monitoring and/or response.
With an analog camera, the video signal is transported over a coaxial cable without any encryption or authentication. In this way, anyone can tap into the video or worse, replace the signal from a camera with another video signal. Analog cameras also require additional cables for power and possibly PTZ functions. IP cameras can use a single data cable such as CAT5e for video, power, and PTZ. They also can encrypt the video being sent over the network to make sure it cannot be viewed or tampered with. The system also can be set up to authenticate the connection using encrypted certificates that only accept a specific network camera, thus eliminating the possibility of anyone hacking into the line. The network camera also can add encrypted watermarks to the video data stream with information on image, time, location, users, alarms and more, in order to secure an evidence trail.

CAT5 CABLING DETAILS
What is the proper way to run and terminate CAT5 cables?CAT5 cable contains four pairs of copper wire. CAT5 supports Fast (100 Mbps) Ethernet and comparable alternatives such as ATM. As with all other types of twisted pair EIA/TIA cabling, CAT5 cable runs are limited to a maximum recommended run rate of 100m (328 feet). CAT5 cable usually contains four pairs of copper wire. Fast Ethernet communications only utilize two pairs. Another specification for CAT5 cable, CAT5 enhanced (CAT5e), supports short-run Gigabit Ethernet (1000 Mbps) networking by utilizing all four wire pairs and is backward-compatible with ordinary CAT5. Though newer cable technologies like CAT6 and CAT7 may be available, CAT5e cable remains the popular choice, because it is both affordable and fast enough for today’s LANs.
When terminating CAT5e or any other data cable you must only use terminators that are designed specifically to work with that class of cable. You also should maintain the integrity of the twists and pairs as much as possible. RJ-45, short for Registered Jack-45, is an eight-wire connector used commonly to connect computers onto a local area network (LAN), especially Ethernets. RJ-45 connectors look similar to the ubiquitous RJ-11 connectors used for connecting telephone equipment, but they are somewhat wider. The diagram, Typical RJ-45 Wiring, shows the pin out and color code for a standard RJ-45 cable.
NETWORK TERMS FURTHER EXPLAINED
What do the terms “gateway” and “subnet mask” mean?A gateway is a node on a network that serves as an entrance to another network. In enterprise systems, the gateway is generally the computer that routes the traffic from a workstation to the outside network that is serving the Web pages. In a home, the gateway is the ISP that connects the user to the Internet. In enterprises, the gateway node often acts as a proxy server and a firewall. The gateway also is associated with both a router, which uses headers and forwarding tables to determine where packets are sent, and a switch, which provides the actual path for the packet in and out of the gateway.
A subnet is a logical grouping of connected network devices. Nodes on a subnet tend to be located in close physical proximity to each other on a LAN. Network designers employ subnets as a way to partition networks into logical segments for greater ease of administration. When subnets are properly implemented, both the performance and security of networks can be improved. In IP networking, devices on a subnet share contiguous ranges of IP address numbers. A mask known as the subnet mask or network mask defines the boundaries of an IP subnet. The correspondence between subnet masks and IP address ranges follows defined mathematical formulas. IT professionals use subnet calculators to map between masks and addresses.