
Early in the convergence of information technology (IT) and physical security, a common piece of advice for success was to “speak IT’s language” when it was necessary to get the IT director involved. It was essentially a courtesy nod — similar to learning “hello” and “good-bye” when visiting a foreign country. With disparate backgrounds, IT entrenched in standardization and rapidly changing technologies and physical security dominated by a proprietary mindset and slowly changing products, the two industries were similar to two foreign countries with two different languages before convergence began. That is not the case today, as convergence between IT and physical security keeps accelerating and the boundaries continue to shrink.
Today, to be successful, speaking the language of IT isn’t just about including a few buzzwords — it’s also about incorporating the discipline’s best practices and requirements into documented methodologies, skill sets and strategic visions. Anything less might fail to translate…into business. The intersected approach is enabling interaction between physical security and IT as peers rather than visitors.
More Than Buzzwords
There’s a big difference between saying “hello” and having a two-way conversation. That’s the transition successful integrators have made to move from simple communication to interaction as peers.
“A few years ago you could teach a security professional a few key IT ‘buzzwords’ and get by. But today, you need to have IT professionals at the table,” says Paul Thomas, president, Northland Control Systems, Fremont, Calif.
As John Nemerofsky, vice president, sales and marketing, Niscayah Inc., Duluth, Ga. explains, “Of course speaking IT’s language is important. However, speaking the language is just superficial and will only get you in the door. Good IT directors will test your knowledge when you are introduced as a security integrator to determine if you are technologically savvy or just a ‘device hanger.’”
How are integrators successfully leaving the label of ‘device hanger’ behind? One way is through training and hiring the right personnel.
“At Northland, we address all aspects of IT in-house with our own staff. By hiring personnel with strong backgrounds and experience, we are able to close the gap between IT and security and deliver exactly what the customer is looking for,” Thomas says.
Northland Control Systems’ North American 2009 revenues were $14.5 million, generated predominantly by a small, select group of Silicon Valley Fortune 150 customers, including Apple, Autodesk, eBay, Kaiser Permanente, Oracle, Microsoft, Palm, Stanford University, Symantec, and VeriSign. Apple? Oracle? Microsoft? Northland is succeeding in the heart of IT country.
Thomas attributes success in communicating as peers by employing the right personnel.
“To really ‘speak the language’ of an IT director, we feel it is critical to employ personnel with the proper background and education,” Thomas explains. “We do not merely throw around buzzwords, but actually have degreed IT professionals that know what they are talking about. We’re able to openly communicate as peers.
“Northland currently has MCSE- and CCNA-certified staff, in addition to being factory trained at the highest levels possible,” Thomas says. “We will continue to train in areas we see the industry shifting towards. Blending seasoned engineers with many years of real world experience with professional IT engineers has been very successful. Our focus lately has been on candidates with IT and strong database-centric backgrounds. Having both disciplines allows us to better serve our customers’ ever-evolving needs.”
Certified staff is a growing requirement that’s not going away; it counts heavily to IT departments.
“IT personnel are less likely than security leaders to be tolerant of ‘practical experience’ as a substitute for formal certifications — more and more we are seeing certification requirements as a pre-requisite to be a service provider,” observes Jason Oakley, chief executive officer, North American Video (NAV), Brick, N.J.
Steve Collen, senior director of business development for the Physical Security Business Unit at Cisco, San Jose, Calif., takes it further, stating that certification is what separates the good from the great.
“To get from average to excellent, integrators must have respected certifications in place such as those individuals that have CCNA or CCNE, and they must have a good number of them. They have to make the investment to have a dedicated, certified IT team while providing physical security.”
John Kostelac, sales and engineering manager, Northwestern Ohio Security Systems, Lima, Ohio, explains his company’s approach to certifications: “General networking certifications we look for are CCNA and N+. N+ certification is almost mandatory for technicians. CCNA is a little harder to come by, but nice if you can get one or two Cisco-certified people on board. Then on the physical security side we are looking for ASIS certifications and primarily CPP. If you are CPP certified it helps justify to the client that you know what you are talking about. We also encourage NICET certifications. Product specific certifications are the next item and those just depend on the products you choose to sell. For example, since we elect to sell Milestone, a majority of our technicians have been to Milestone training to get certified on their different VMS platforms,” Kostelac says.
In addition to emphasizing certification, successful integrators are also proactive about interaction with IT. And therein lays another key to success in the IT world — getting IT involved right away.
Proactive Conversations
Leaving out IT from the initial stages of a project is a huge mistake. Most integrators list immediate involvement of IT as a critical part of winning business and completing projects successfully.
Nemerofsky says, “Our approach is simple. If we are awarded a contract by a physical security manager, we encourage him/her to get IT involved in the design and implementation of the project. If IT is intimately involved up front, the physical system integration with IT networks becomes transparent and simplified.”
Thomas explains the damaging effects that can happen to a project not involving IT from the beginning.
“Unfortunately, if IT is not involved ahead of time during the design phase, it is usually not until the equipment is implemented that there are issues discovered, and IT is then involved. By then, IT is usually frustrated and less inclined to openly assist. We encourage and request IT’s involvement as early and as often as possible,” Thomas says.
Instead of focusing only on IT, top integrators suggest involving everyone from the beginning.
Mike Kobelin, vice president, sales, Aronson Security Group (ASG), Beaverton, Ore., also chairman of the board at PSA Security Network®, Westminster, Colo., says, “We strongly believe we are the responsible party to bring the various groups at our client sites together for a successful solution deployment. ASG works with facility managers, physical security managers and IT to create a holistic approach to security. Amazing as it may sound, we find that some of these different departments still operate in ‘silos’ within larger corporations. We always do all we can to create open communication between the groups and be the ‘trusted security advisor’ who brings all the parties together.”
Effectively bringing all the parties together hinges on continuous, successful communication. One way NAV ensures successful communication is by assigning a single point of contact for a customer so that the company can coordinate all of its technical and operations resources in a manner that is transparent to the customer, Oakley explains.
Good communication needs to be coupled with outstanding project management skills, advises Steve Surfaro, business development manager and security industry liaison, Axis Communications Inc., Chelmsford, Mass.
“It is up to the security integrator to be trained in ‘IT speak’ and communicate well among all the involved parties, but the integrator must also have excellent project management skills — a standardized way to help move the project along and define responsibilities — and then also define properly and interpret properly what the end user should be receiving as a delivered system,” Surfaro says.
Choose Method Over Madness
The best way to deliver a system successfully? Make it systematic. Put your processes in writing. Get a list together of initial questions to ask. Systemize any necessary interviews and define the key departments that need to be involved.
“Develop your checklists for what questions to ask and how to implement the projects. More importantly, a division of responsibilities is always prudent, especially when working with large groups. Communicate to everyone at the project table regarding who is doing what. Action items can be assigned more easily, and there is no finger-pointing because everyone understands what their primary role is and who is doing what,” Sufaro advises.
ASG has developed its security process optimization (SPO) assessment strategy to allow better insight to the total client ecosystem that allows the company to better articulate and design the technology plan. Kobelin describes the SPO as “the tool that helps us get deeper into each part of the company.”
“Through one-on-one meetings with everyone involved in the project from C-level directors that will talk to us about the financial aspects and corporate vision of security all the way down to the person who actually responds to alarms, we are able to collect what everyone knows and is looking for and use all the input from everyone to generate a comprehensive solution. As a company we can offer core services that bridge disparate organizations through our SPO practice within our Professional Services Organization,” Kobelin describes.
It is a systemized approach highly recommended by Ron Hale, chief relations officer at ISACA, a non-profit organization of more than 85,000 members that engages in the development, adoption and use of globally accepted, industry-leading knowledge and practices for information systems. However, he doesn’t just stress developing a methodology. He also recommends making sure it counts. “IT departments are looking for the integrity of the development process, so use a development methodology that the IT people recognize. If they don’t know it, it won’t carry as much weight. There is proven methodology available for coding and software development. Companies need to use it so the IT departments can see that proper security, thought, and requirements were built into the systems.”
Being exact leads to matched expectations and success, and success leads to more success, especially if you capture it into a methodology. Dave Tyson is chief information security officer (CISO) of Pacific Gas & Electric Company (PG&E), one of the largest combined natural gas and electric utilities in the United States. He is also a member of the ASIS board of directors, who has previously served on the Professional Certification Board of ASIS and the Information Security Council. Tyson says: “Each successful project plays into your value. Capture that information you gain from each one into a road map or a methodology and then you are able to repeat it over time. With a method you can use over and over again, you have a verifiable, repeatable process that you can use as an argument.
“All the big consulting companies sell the same services as everyone else — but they rely on their systematic approach and sell it as a higher value. Customers pay more money for their services because they have a proven methodology and they can say, ‘This is what you will get from us, and you don’t have to take our word for it — we can prove it.’”
Integrators must also prove they understand the network, and they must possess the ability to explain to IT what their proposed system will do and how the hardware and software they are choosing will affect the network. Implementation must be discussed with IT as well, because as Tyson bluntly puts it, the implementation is the vulnerability. “If you deploy a product badly, it doesn’t matter how good the security initially is, the system can be beaten quite easily,” he says.
So prove your deployment and then separate it from everyone else’s. “When you show IT directors you have a proven plan for a successful deployment, you have their attention,” Tyson explains. “Having a proven methodology, showing the benefit your past customers have received from their systems, demonstrating how risk has been reduced in other systems, detailing the steps that will be gone through, stating what the testing sequences are, listing the validation process used, showing code quality checks — all that needs to be in the methodology and presented to IT,” Tyson says. “Showing me the steps that ensure my system will be secure is a powerful argument I listen to.”
Intentional Products
Product selection is another powerful argument. In fact, Kostelac lists product selection as one of biggest factors separating Northwestern Ohio Security Systems from its competition.
“Product selection is a key concept for us. It is a key thing not only for us to gain a competitive advantage and to win business, but also to save ourselves time and position ourselves better. It is critical is to get on board with future-focused manufacturers, be forward thinking and try to foresee what products are going to be ‘All-Stars.’ If you are ramped up on the product selection, and by that I mean you are trained on it, you have earned additional prices breaks on it, and you have developed manufacturer relationships on it by starting today, then in the future you are in a much better position than your competitors. It pays to pick the right products at the right time that the IT department knows.”
Carefully selecting products with future IT projects in mind can go a long to way to addressing concerns IT directors may have.
Kostelac has seen a marked change in the company’s product selection the last six years, and he’s simultaneously seen a marked change in IT directors’ reactions.
“In the past we would sell a proprietary DVR, which IT would have more of a problem with since they want more control of what is going on the network. Now the products that we lead with are intentionally IT-friendly products. They take the products with more open arms because they are familiar with the products we are mentioning.”
Nemerofsky also fingers proprietary products as a good way to lose business. It is a leading concern of IT directors, and to win business, integrators need to makes the changes necessary to put the concerns to rest.
“IT personnel do not like traditional proprietary devices connected to the network, such as DVRs that cannot be secured against intrusion, viruses, etc.,” Nemerofsky says. “With that in mind, we try to select devices that are both open market available and somewhat non-proprietary in nature so the client’s IT group can protect the devices directly, or we seek to ensure that the devices are protected by building in maintenance and inspections to ensure that firmware and software upgrades are installed as released, virus definitions are continuously updated and firewalls are secure.”
Many integrators also advise against selecting too many products. Northland’s philosophy “is to partner with one or two manufacturers in each discipline. This allows us to have the strongest technical team because they are not diluted across the learning curve of several products.”
Collen agrees with the emphasis on product selection.
“For the physical security integrator who wants to become a leader and build their reputation they should be proactively focused on product selection, paying attention to the security included in the products and identifying the exposures their products bring to the network and what should done about them — whether they are mandated to address the exposures or not.
Organizations such as PSIA and ONVIF are helping create standards to bring physical security products closer to the interoperability and openness IT likes to see.
Raul Calderon, vice president of marketing, Arecont Vision, and a PSIA board member says it is a process in motion, though by no means complete, and it is an important change for the security industry.
“The IT world has been standardized and open since its inception, whereas the security world has been very proprietary. PSIA, ONVIF — no matter the standard — I think moving forward with the standardization process the industry is going through today, while painful, serves the best interest of the industry at large. The developing standards will make it that much easier to select products without worrying about interoperability, compatibility and standardization, and working with standards bodies will translate well to IT.”
Tyson further insists that success lies in combining products with data.
“The physical security folks that are going to successfully make this transition are going to have to have new metrics to track the performance of their technology so they can argue in the language of product differentiation about how much their product reduces risk or how it performs against customers’ expectations. If they can do that, they can win the argument. The product choice alone isn’t enough. It is the data you present with it that sets you apart.”
Address Concerns…and Then Some
In addition to addressing common items like bandwidth consumption, network security and maintenance of equipment, Thomas says Northland Control Systems works to eliminate “the unknown” in projects for IT directors.
“I think their concerns lie within the unknown: unknowns such as; ‘What impact will it have on the existing infrastructure?’ ‘What vulnerabilities may be exposed by the product?’ ‘Who has access to the equipment?’ and ‘Who will manage it going forward?’” says Thomas, listing a few. “By better educating IT on the ‘ins and outs’ of the product, they become more familiar and comfortable with it. We allow them to express their concerns and address them either by configuring the product a specific way or using an entirely different one in some cases.”
When addressing concerns, Hale emphasizes demonstrating visibility. Communicating that you are prepared to let IT see products right away is effective.
“They want to have visibility to all devices on the network and the ability to see that the operating system has been configured with their security policies. They need the ability to see into and have control over things. They may not always need control — but they do need to understand the operating system and what is happening there and make sure it is structured in a way that is consistent with their policies. You have to be ready to show that to them and prove that it doesn’t open any vulnerabilities,” Hale says.
It is an approach highly recommended by Tyson. Prepare for the “what if” questions and eliminate the question marks.
“Showing you have thought out the integration and all the ramifications for putting your system on the network goes a long way to proving competency and deliverability. Companies that are prepared to answer the “what if” questions will be the ones to earn projects,” he says.
It helps if you walk in with a plan on how to do that. An offensive, well-thought out argument dispels the tension points. Showing you have vetted the system, will work with the IT department and are taking the risks seriously goes even further.
In fact, it is a big differentiator, according to Tyson.
“Integrators have been competing with each other for years on the same story, saying things like, ‘We hire better people, we have better methodologies, we are just better.’ Here is a real opportunity to unmistakably define the difference and have proof, not just words.
“If an integrator can say all the usual standard things (‘We’ve been doing it 20 years, we employ the best people,’ etc.) but also say, ‘We are going to help you understand how to integrate this into your environment securely and make you fully aware of the risks and let you factor that into your IT processes to make sure you are not at risk, and work with you’ — just that statement alone in my mind as a buyer is a differentiator for me and would get my attention,” says Tyson.
It is a powerful way to walk in and say far more than “Hello.”
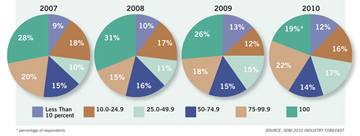
New Installations Using Company IT/Networking Expertise
As part of SDM’s 2010 Industry Forecast Study, integrators were asked, ‘In what percentage of new installations or projects does your company use your expertise in information technology/networking?’ Across the years, their responses have fluctuated.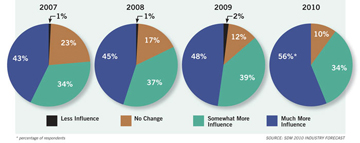
What Will Be the Effect of Information Technology (IT)/Networking on Sales in the Following Year?
Ninety percent of respondents to SDM’s 2010 Industry Forecast Study indicated an increased influence from IT to some degree, a percentage that’s been steadily growing since SDM began asking the question in 2000. In 2010, only 10 percent anticipated no change.
In 2010, How Many People Does Your Company Employ in the Field of IT or Management Information Systems (MIS)
Respondents to SDM’s 2010 Industry Forecast Study revealed most companies employ an average of six employees in the field of IT or MIS.Certifications to Consider
Steve Surfaro, business development manager and security industry liaison, Axis Communications Inc., and Paul Thomas, president, Northland Control Systems, suggest considering the following certifications.
Converged Network Security, IT and Physical Security Risk Management
• CISSP (Certified Information Systems Security Professional) — ISC2’s top credential in logical access control, converged IT, physical security and risk management; updated frequently; has wide appeal.
• MCSE (Microsoft Certified Systems Engineer) — Microsoft, network architecture, administration; since there are multiple iterations of this exam, the student needs to consider the time necessary to retake exams on newer versions to stay current with this credential’s fast-paced changing nature.
• CCNA (Cisco Certified Network Associate) — Cisco, network architecture, application, administration.
• CCSP (Cisco Certified Security Professional) — Cisco, network architecture, application, administration.
• CWSP (Certified Wireless Security Professional) — Cisco, network architecture, application, administration.
• CompTIA A+ — This is a general purpose course that offers education in multiple areas including network, security, and troubleshooting for IT-related problems.
• CompTIA Network+ — This course trains on installing, configuring, and troubleshooting different networking aspects.
• MCSA (Microsoft Certified Systems Administrator) — This certification is on its way out, but there are still a lot of companies still running on Windows Server 2003, so it will remain relevant a little longer.
• MCTS (Microsoft Certified Technology Specialist) or MCITP (Microsoft Certified IT Professional): Server Administrator — This certification is the Server 2008 equivalent to the MCSA for Server 2003. A good application-oriented test, in many ways easier than MCSE.
• MCITP: Enterprise Administrator — This certification is the Server 2008 equivalent to the MCSE for Server 2003. At this time there is a large following for MS Server 2003 and therefore the MCSE remains the more favorable both as current practice and foundation.
Manufacturers’ Certifications/Credentials
• Most manufacturers’ offer some form of training with credentials or certifications.
Physical Security Management
• CPP (Certified Protection Professional) — ASIS’ top industry credential, recognition for consultant, risk management professional, ability to apply physical security practices to technology, personnel and business process.
Physical Security Project Management
• SIA’s CSPM (Certified Security Project Manager) — informative and useful credential for physical security project management discipline.
• ESS (Electronic Safety and Security) — BICSI’s accreditation for converged network infrastructure, safety and physical security systems; New and gaining momentum.
• PSP (Physical Security Professional) — ASIS’ relatively new credential; but actually has more difficult credential parameters for overall technology and project management capability in the physical security domain.




