1. Access control software can be run from only one computer.
a. True
b. False
2. Door access can be allowed or denied based upon the:
a. time of day.
b. specific door.
c. day of year.
d. Any of the above
e. None of the above
3. Access software can be accessed over a:
a. LAN.
b. standard POTS line.
c. Internet.
d. Any of the above
e. None of the above
4. Which operating system is required to run access control software?
a. Windows 98
b. Windows 2000
c. Windows XP
d. Depends upon the software
5. All access readers in a system must be the same type.
a. True
b. False
6. Activity reports can be generated based upon:
a. doors.
b. employee name.
c. date and time.
d. type of activity.
e. Any of the above
7. If a card is valid on one reader, then it also will be valid on all readers in the system.
a. True
b. False
8. You cannot mix fingerprint and retina biometric readers within a single system.
a. True
b. False
9. Smart cards can utilize which reader type?
a. Contact
b. Contactless
c. Combination contact and contactless
d. All of the above
10. All biometric readers require a dedicated enrollment reader.
a. True
b. False
11. Which of the following reader technologies can be incorporated on a smart card?
a. Standard proximity
b. Wiegand
c. Bar code
d. Any of the above
e. None of the above
12. All smart cards have the same memory capacity.
a. True
b. False
13. Integrating access with alarm or elevator control can only be accomplished by using output relays.
a. True
b. False
14. Access control software can include an integrated Photo ID software package.
a. True
b. False
15. Which of the following would be included for a typical door with a magnetic lock?
a. Access reader
b. Request-to-exit device
c. Emergency fire alarm override
d. All of the above
e. None of the above
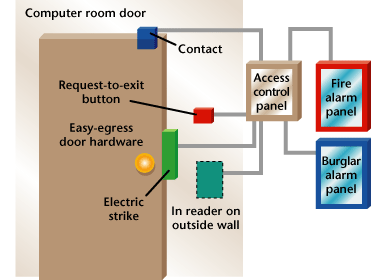
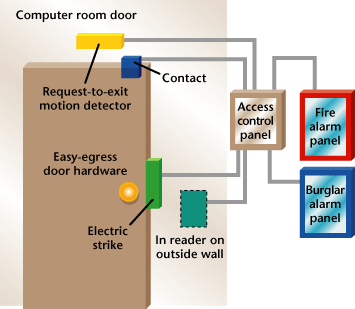
What’s Wrong with This?
Wally `Larman installed an access control system for a client that included the computer room door. As the work was progressing, the customer requested that the door-held and door-forced alarms be connected to his existing BA system so that he would be alerted if someone improperly opened or failed to close a door. Wally installed the devices as shown in this diagram, but frequently when someone left the computer room, a door-forced alarm was generated. Can you see what Wally did wrong and what he must do to correct the problem?1. b – Depending upon the manufacturer, access control software can be managed from multiple computers.
2. d – All these factors can be used to decide if access will be allowed or denied. Typically, systems allow the creation of multiple access levels or groups that can be assigned to users.
3. d – Again depending upon the manufacturer’s access control software, any of these communication protocols may be possible. You should check with the manufacturer that you use to determine which they support.
4. d – Every system has different requirements for operating system, drive size, memory etc. You should check with the manufacturer that you use to determine what they require.
5. b – Most systems allow you to mix reader types and technologies.
6. e
7. b – The access software allows you to program which cards are valid at each reader.
8. b
9. d
10. b – Although an enrollment reader may make it easier to add users, many manufacturers do not require a dedicated enrollment reader.
11. d – Smart cards can have other reader technologies incorporated into the card. This can be important when various reader technologies are existing or when dealing with multiple vendors.
12. b
13. b – Depending upon the manufacturer, it is possible to use a data connection to integrate access with other applications.
14. a
15. d – All these devices should be installed on a door with a magnetic lock to provide maximum security and safety.