
With
this system, the user’s fingerprint template is stored on the smart card so the
live and stored fingerprints can be compared for an extra layer of security.

The architecture of access control systems must allow for
placement of readers in many different locations, such as this prox card reader
at the swimming pool of a gated community in southern California.
“Nothing happens without there being a database and a set of business rules that have been established,” says Jerry Cordasco, a security consultant located in Maplewood, N.J. Electromechanical devices preceded today’s electronic access control systems and still are used in high-impact environments. Some of these devices resemble stainless steel ashtrays that require users to put a hand inside the device and enter a code on tumblers that only the user can see.
“If your code matches the electronics board behind, it allows the door to unlock,” explains Richard Goldsobel, vice president of access, Continental Access, a division of NAPCO Security Systems, Amityville, N.Y. “It’s become a widely used device in the Navy and military applications, so it’s been a very heavy government sale item. It dates back to the 1960s. We still sell a number of them a year. We’re the only supplier left with that type of device.”
More recent access control systems take data from a card reader or biometric device and send it to the “brains” of a system, which may be located at the door in the reader, in a nearby control panel — or for networked systems it would be in the computer controlling a multi-door system. The way this is set up is called the architecture of the system.

A technician for Controlled Integrated Access, New
York, installs a control panel for a networked access
control system at Wenner Media Inc., New York,
publisher of Rolling Stone and other magazines.
That number either is or isn’t one that allows entrance at a particular door and time of day. If criteria are met and the data matches, the system will throw a relay or some other action and the door will open, says Cook.
Some numbers may include a site or facility code that precedes the card code, explains Richard Sedivy, director of marketing, DKS DoorKing Inc., Inglewood, Calif. Two cards could have the same card code but be distinguished by their site code, he adds.
Older access systems might connect card readers using the RS232 or RS485 protocol over a hard-wired serial communication system back to the door controller. In newer systems, the readers are connected to a customers’ local area network (LAN) or wide-area network (WAN) through the Ethernet or using the TCP/IP protocol.
“If you look at the networks in general, the most commonly used for an IT network is the Ethernet,” notes Mas Kosaka, president, PCSC, Torrance, Calif. “You could literally go anywhere in the world and get an [Internet] connection.
“More people understand IT,” he adds. “RS45 is pretty old and IT people really don’t like to do that, because they can’t control the network from a data flow standpoint. The Ethernet has the biggest acceptance.
“RS45 is more of a very old technology,” Kosaka maintains. “It still has its place, but a lot of installers, especially the low-voltage installers, don’t know what an RS45 network physically is, whereas if you ask an installer to install a Cat 5 or Cat 6 cable, they understand exactly what that is.”

The controllers are the brains of a distributed access
control system. This control panel can handle from two to 16 doors.
BRAIN DISTRIBUTION
Some access control systems are distributed, meaning that intelligence is in control panels near the doors they control or in readers next to the doors.“The computer’s job is to stuff information into the panel so the panel can know what to do later,” Cook says of distributed systems. “The panel’s job is to report back to the computer. That gives us a log-type scenario.”
Sedivy points out the advantages of distributed access control systems. “The nice thing about the controllers is that they’re not dependent on a PC running and being connected to it all the time and making all the decisions,” he declares. “The controller is making the decision. The only time you use the PC is to do your programming, gather your transactions and make any changes in the system.”
In a centralized system, decision-making is centralized in a single computer’s central processing unit (CPU). “Basically, the panel gathers information and transfers it back to a CPU of some kind,” Cook says. “The CPU does all the checking and rechecking, and then sends a signal back to the panel, and says, ‘Go ahead and open it up.’”
The upside of a centralized system, Cook says, is that such systems tend to be less expensive because they are software-driven. “The downside is that if the PC breaks or if it runs into a problem, you lose your entire system all in one shot,” he adds.
Kosaka thinks that the majority of access control installations have intelligence in the controllers but also a connection to a host computer. “That’s the controller architecture,” he calls it. “In a controller type, if anything that’s connected to the controller fails, you don’t lose the entire network.”
Many variations on centralized door control exist — many vary from manufacturer to manufacturer, points out Goldsobel. One way of speeding up large access systems is to use two host controllers, perhaps each one controlling 100 panels in separate buildings of the same facility, that communicate with the same database.
“That way it also tends to be faster, because you have two host systems administering half the number of panel searches,” Goldsobel says.
Another variation employed by MDI Security Systems Inc., San Antonio, uses network local controllers (NLCs) and dual door controllers (DDCs) to reduce system costs.
“If the system has a significant number of alarms or access control that is located within the same area, from an expense standpoint it’s cheaper to go to the NLCs, which are less expensive boards,” notes Jim Lowder, MDI’s vice president of engineering and chief technical officer.
“If I’ve got an office in 50 different cities on one common network, and all I need for each office is a couple of card readers to manage my access, the DDC would be perfect, because it is half the cost of an NLC,” Lowder explains. “But if all 50 readers are in one building, I would get an NLC.”
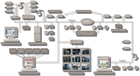
Dual door controllers (DDCs) lower the cost of this open
architecture system that integrates access control with video surveillance and
other security devices.
INTERNET CONNECTION
Another variation on the arrangement of door controller and CPU are systems in which the door controller itself is a PC that is connected to the Internet. This enables the controller to be accessed remotely over the Internet through an interface similar to a Web browser.With these systems, users can unlock doors remotely from anywhere they have an Internet connection and a computer. No software is required to be installed on the user’s computer — the software can be accessed on the Web browser.
“Because of that, there is somewhat of a revolution in the architecture of access control systems going on now,” Cordasco asserts. “What remains the same is everything at the door.”
What are called embedded Web server products by Steven Van Till, president and COO, Brivo Systems Ltd., Bethesda, Md., are being offered by several companies. “It’s kind of catching on as the way to do browser-based access control,” Van Till reports. “The embedded Web server is better suited for one site [rather] than multiple sites and for the lower end of the market.”
In these types of decentralized systems, the role of the host computer is to do the initial enrollment of employees and set up which employees can enter at various doors at certain times of day and certain days. This information is then sent to the controllers, where it is stored locally.
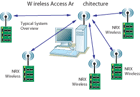
Wireless access control systems operate using a number of
different technologies, including IEEE 802.15.4, Wi-Fi (802.11b/g), BlueTooth,
ZigBee Alliance standards and MESH routing.
A CUSTOMER FOR LIFE
The software of most access control systems is a closely guarded secret. “From the door controller to the computer, and the computer software itself, they’re virtually all proprietary,” Cordasco emphasizes. “The only thing that is not proprietary is the format of data that’s transmitted from the reader to the door controller. That is typically standard Wiegand.”Because of this, many readers can be mixed and matched with different access systems, points out Matt Barnette, vice president of sales, AMAG Technology Inc., Torrance, Calif.
“I kind of equate card readers to tires on a car,” he compares. “You have your basic models and you have your high performance models. They all offer different advantages and disadvantages, but by and large, most are interchangeable.”
Manufacturers could use a 30- or 35-bit Wiegand, but they have settled on 26-bit, Sedivy notes. “Wiegand is really an open architecture. Manufacturers can put as much information in that Wiegand code as they want and use it for different things. However, the standard is 26-bit,” Sedivy says.

Any MESH server can be paired with a LANBot server. Each
holds all the data required to operate the system, while any changes are
auto-synchronized. The MESH LANBot sits latent until a primary server fails.
The LANBot then takes over all processing. LANBot servers provide a similar
functionality to RAID 5 but at a greatly reduced cost.
Although end users are in favor of standardizing access control systems, “From the manufacturers’ standpoint, it’s a little different,” Cordasco declares. “Once you have that system in, you have a customer for life, because it is cost-prohibitive for a customer to pull out, because they’d have to change the whole system.”
The cards, wiring, readers, door contacts and hardware, and request to exist (REX) might be compatible among different systems, but the door controller, control panels, computer system and software would probably have to be changed by an end user switching access systems.
Manufacturers did not list standardization as something they see in the future of their products, but Barnette sees in access control’s future the continued movement of intelligence to the access side.
“The intelligence is being pushed more and more to the edge of the network,” he points out. “We’re making the access control panels smaller, faster and more powerful.
“Consequently, they also are becoming less expensive, so we can miniaturize them and put them farther out to where you are building a lot of the electronics in the reader device,” Barnette asserts.
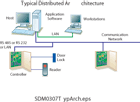
A typical distributed access control system puts the
intelligence in the controllers and control panels rather than the host
computer.
Carlos Lopez-Reyna, product marketing manager for Honeywell’s Pro-Watch software security management system, points out, “You still need a focusing point for all that intelligence, so the host is evolving into a manager of all that intelligence. It also provides you with communication to outside systems.”
Maintains Anspach, “When we think about what’s going on at the door, there seems to be some real value around ease of deployment and use. There’s also some security concerns with this device at the door. How easy is it to get access?”
With the system from Viscount Systems, Burnaby, B.C., the door readers have an encrypted database at the door. “If you have a secured database but with no external data connection to the device, as long as it’s encrypted, there’s not much chance somebody could do something with it,” says Stephen Pineau, Viscount’s CEO.
Proponents of control panels, host computers and Web sites rely on the data being physically farther from the door. In the end, the market will decide, and technology advancements may render the question moot.

Dealers can provide concierge services with Web browsers (on
the right) for their customers who are using a hosting center. The center can
be accessed similarly by end users themselves.
Sidebar: Access Control System Managed by Third Party
Some manufacturers offer Web-hosted access control, in which a company’s access control system is managed by a third party. In this category is Brivo Systems LLC, Bethesda, Md., which offers this service to its customers for a monthly fee. The architecture of the access control system is similar to others. Access intelligence is in the controller and authorized persons are allowed access based on the database in the controller.“Where it begins to differ is in terms of reporting that event to some other entity,” explains Steven Van Till, president and COO, Brivo Systems Ltd., Bethesda Md. “Ours goes out over a wireless cellular network, if they have a wireless control panel, or it goes out over the Internet, and the record goes back to the central database in a data center in northern Virginia.
“That part is unique to Brivo, that it is reported to the data center and through a central repository, rather than through a local server or PC on the same premises as the control panel and the facility itself,” Van Till maintains.
The center provides a Web graphical user interface (GUI) for customers’ browsers; stores all configuration and event data for all accounts and control panels in an Oracle database; and manages communications with control panels through the Internet and/or cellular carriers, all for a monthly fee.
Sidebar: Back to the Future
Although many systems eschew access control from a host computer in favor of decentralizing it in control panels, Viscount Systems, Burnaby, B.C., is swimming against the stream.“The original architecture that people thought access should work on is very similar to what we do,” maintains Stephen Pineau, Viscount’s CEO. “The problem was host computers didn’t have the horsepower or ability to perform properly. The only reason control panels exist is because the host computer couldn’t do enough to make a lot of doors work. The answer is back to the future.”
Viscount Systems’ centralized design aims to diminish computer failures, using backup servers and uninterruptible power supplies (UPS), Pineau maintains.
With control panels, backup power equipment must be installed for each panel, he notes. “With a host computer system, you can use a single UPS to back everything up,” he points out.