At one end of the spectrum is a large manufacturer, which has 55 locations that operate autonomously but have a real-time feed into a centralized database. At the other end of the spectrum is a major utility company that is upgrading its 70-location system so that it will be controlled by a database driven by an interface with the company’s human resources system. Our third example is a large financial firm whose chief concern was that its new central command station could back up access control systems at five satellite locations.
Manufacturer Implements Centralized Database for 55 Locations
A couple of years ago, a large manufacturer made the decision to create a centralized database for stand-alone access control systems that were spread across 55 U.S. locations.“People at the company realized that if they had a workplace violence issue and wanted to disable someone’s card, they had no way to verify that the person was suspended in all of the systems,†says Mark Riddell, manager of technical support for Siemens. To handle the access control system upgrade, the client turned to Siemens, which had acquired Sensormatic, the company that originally installed most of the stand-alone systems in the 1990s.
A key goal of the upgrade, which was completed in the fall of 2003, was to retain the existing stand-alone access control systems, which were from two different manufacturers. Today, these systems continue to operate autonomously, but each now has a real-time feed to a centralized database. From the central database, authorized users can see which employees have access to each facility, although they cannot determine specific details, such as the hours when an employee is allowed access. As part of the project, however, a common set of procedures was established that each location is required to follow.
The project took about a year-and-a-half to complete and required extensive custom software development. Developers created what Riddell calls “communication agents†that run on each access control host computer and provide database hooks into the system. Any changes made on any of the host computers are automatically communicated to the central database, riding on the client’s corporate computer network.
Siemens’ development team spent several months creating and testing the custom software before conducting a pilot test involving several sites. Based on the results of the pilot, the team did a bit of re-engineering before embarking on a full-scale implementation, which took about four months. A two-person team spent two days at each location, installing the communication agent and a dedicated workstation and ensuring that the system was properly connected to the corporate computer network. As each new location was brought online, the cardholder information from the access control database was uploaded to the central database, where a record was created for each cardholder. The system had the intelligence to recognize when the same cardholder had access privileges at multiple locations and stored all of the information about that cardholder in a single record.
One of the challenges in completing the project was to satisfy all the requirements of the client’s information technology personnel so that the access control system could be connected to the corporate computer network. “The client has corporate IT standards about operating systems and as a result, we had to go through a deviation process,†says Riddell, who adds that some individual locations also required a deviation process.
Siemens actually owns the dedicated workstations that were installed to support the system and is responsible for maintaining them. Project participants came to that agreement so that Siemens would be responsible for the software loaded on the workstations. To support this requirement, says Riddell, Siemens developed a workstation management system that works within the client’s management system. The workstation management system communicates to Siemens over a wide area link between Siemens and a central client location.
Other plans include bringing locations outside the U.S. onto the centralized system and tying the system in with the corporate human resource system.
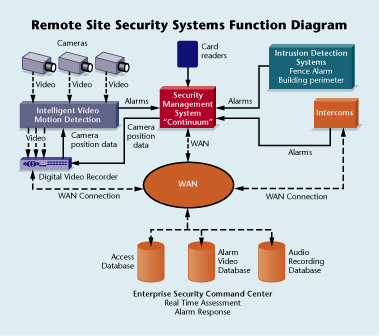
Utility Company Upgrades, Integrates Access with Intrusion
Before undertaking a major upgrade, a large Northeastern utility company had stand-alone access control systems spread across more than 50 locations.“Each location maintained its own system and most had independent databases,†says Barton Kartoz, business development manager for Andover Controls, which handled the upgrade project for the client. “Under those conditions, if an employee leaves the company, it’s not guaranteed that his record will be deleted from every database. If someone wanted to get access to a site, he or she had to figure out the right person to talk to.†The utility company also had about a dozen locations that lacked access control.
The goal of the upgrade project included access control for 70 locations. Requirements for the new system included a single database and integration with multiple intrusion protection systems.
The project was undertaken in three phases, the third of which is still in progress. Phase 1, started in the fall of 2002 and completed in 2003, was to install Andover’s Continuum access control, and various intrusion detection solutions in locations that did not previously have security systems. Initially these systems were resident on the client’s WAN. However, after Phase 1 was completed, the client’s IT department created a virtual private network (VPN) for the security system. This VPN segments the security systems from the remainder of the network, but permits sharing of existing wide area bandwidth. To support the Phase 1 projects, Andover built a temporary command center for the client.
Phase 2 replaced the temporary command center with a permanent one that was capable of handling all 70 locations. The new 2,000-square foot command center, constructed in 2003, includes four operator stations. Each station has one card access and two CCTV workstations. In addition, all security system images can be displayed on a plasma wall. “We brought the command center completely online before we cut it in,†Kartoz says.
In Phase 3, which began in 2003 and will be complete in 2006, existing and new access control systems are being installed in more than 50 locations using the standardized solutions employed in Phases 1 and 2.
Andover did not attempt to migrate the access control databases from the previous stand-alone systems, but instead used a feed provided by the client’s human resources department as the basis for the card user database.
As part of the project, the client had to establish policies governing which employees would have various levels of access based on their job classification. Andover built a template to automate that process based on the client’s policies.
As part of the upgrade, Andover also installed an IP intercom system at each location to replace traditional stand-alone systems. The IP intercom can communicate with local personnel or forward to the company command center via the WAN.
The project required a high degree of software customization in order to integrate the access control system with other systems, including the intrusion protection systems, the video surveillance, the IP intercom system, and the video wall in the command center.
One advantage of integrating the alarm and access control systems is that authorized employees now can bypass portions of the system as their cards are read, which can help prevent false alarms.
Kartoz believes one of the reasons the project was so successful is that Andover was enlisted to design the system as well as build it.

Financial Services Firm Gets Centralized Command, Site Flexibility
When a large financial services firm realized a couple of years ago that it had outgrown its existing access control system, it also realized that it had the opportunity to introduce a higher level of security to its operations. The company had a 23-story office tower and five satellite locations that could now be interconnected as part of the upgrade. “The old system was site-limited and the client had outgrown the addressing scheme,†says Mark Norris, director of the center of excellence for Interface Security Systems, which handled the upgrade. “The enterprise solution we recommended centered on a NexWatch platform that could accommodate and secure multiple buildings that were geographically separated at one central command center, while offering the flexibility of managing each site individually.â€The client made the decision to create a central command center to which all of the access control systems would be connected and which could serve as a backup to security personnel at each location. “Today remote management and control is even more critical,†says Matt Stopa, the Interface regional manager who was involved with the project. If a situation were to arise with a terrorist or disgruntled employee at one of the remote locations, the client wanted personnel at the command center to be able to step in to help. Even further backup would be provided via a connection into Interface’s own central monitoring facility.
Last year Interface completed the central command center and at press time was in the process of replacing the access control systems and connecting the new systems to a network and to workstations in guard stations at each location. The client wanted to retain existing card readers, which included 125 at the office tower and two or three at each satellite location. Once all of the new access control equipment is in place and the database has been recreated (via a custom software development) on the new system, the new system will be burned in. Only then will Interface begin to swing the card readers over to the new system on a door-by-door basis, with both the old and new systems operating in parallel until the job is completed. Existing cards will work with the new system.
“People won’t see much disruption,†Stopa says. “They won’t even know if they’re operating on the old or new system.†This is a dramatic change from what clients used to experience when they did this kind of upgrade. In the past, says Stopa, Interface would have personnel at each client location for an entire weekend, working nearly around the clock to program the system using a snail-like 96-100 baud modem. The new system, which runs over Ethernet, can leverage that high-speed connectivity to reduce programming times to a fraction of what was required previously.
As part of the project, the access control system also is being integrated with the client’s video surveillance system. “Integrating video and access control together is important to large-scale clients,†Norris says. That integration will enable an image from a camera at a protected entrance to be displayed when an employee presents a card at that entrance. Ultimately the intrusion protection system also will be tied in to enable alarm verification via the video system.
Despite all the benefits that centralization can provide, however, Norris cautions against going too far in that direction. “At one point the thinking was that we would eliminate all remote workstations. But security personnel at local sites are best suited to run their own systems. No one knows their own place better. The temptation to over-consolidate can be one that bites you later.â€
WHAT THE CLIENT LIKES BEST:
Being able to manage all cardholders from a central locationAccurate documentation of what was done, which can lower the long-term life cycle cost of the system
Being able to back up satellite offices from a central command center