“You have to be able to demonstrate that it’s cost-effective, but that takes a second place to reliability,†insists one respondent.
That person manages a building in Oakland, Calif., one of whose tenants does data transfers for multiple clients. Perimeter doors to gain access to the building only require a proximity card. The data-transfer company uses a universal card system in its offices because of the system’s cost-efficiency, but it requires a fingerprint scanner to enter the data labs.
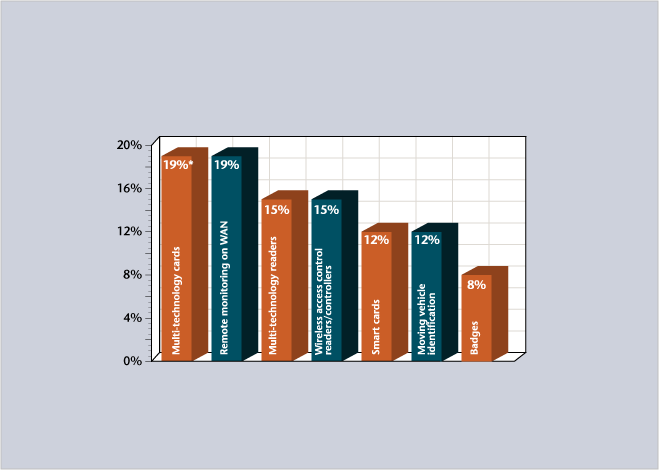
* percentage of respondents
Source: Informal SDM Online Survey of Security Magazine’s End-User Subscribers, June 2005
Two different bar codes on a single card for the approximately 400 employees of the automotive plant are programmed into the system so it only grants entry to those whose cards are authorized. One masked bar code provides entry to the plant and the other unmasked code is used to enter different areas inside the plant. “We haven’t had a single card duplicated over the 10 years we’ve been using 2D bar codes,†Baldassare maintains.
Proximity cards are the access technology of choice at Honda Federal Credit Union, Marysville, Ohio, reports Steven Snyder, corporate facilities group manager.
“We apply security limits to each person, which allows them or doesn’t allow them access based on time and day,†he notes. “Not everybody needs access to the main data or engineering room or even the main room for mortgage files.â€
This system was instituted two years ago so employees would not need to use other cards for the older part of the building. The company also is using hand geometry scanning for customer access to one of its two safety deposit box facilities.
“When you set up a safety deposit box, we put your information into our computer, and then we have you scan your hand three different times, and it hits 96 different points on your hand,†Snyder explains.
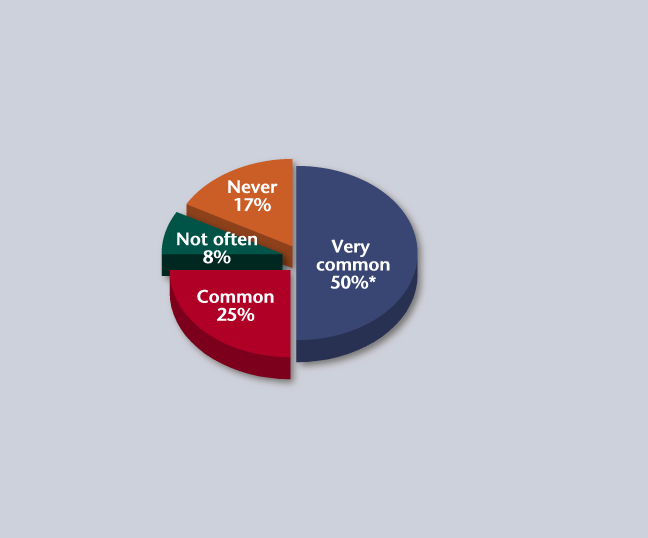
* percentage of respondents
Source: Informal SDM Online Survey of Security Magazine’s End-User Subscribers, June 2005
“The system allows you to go into your box, and you’re the only one who has a copy of that key, and it keeps a record of who has been in,†he describes. Fingerprint and retinal scanners were considered but rejected.
“People just do not like to have things shined in their eyes,†Snyder says of retinal scanners. “It’s just a psychological point.â€
Eric Pickering, president of security consultant Crescent Sentry, New Orleans, says his customers have overcome any apprehension about biometrics, adding that many of them have installed biometric readers in conjunction with outside perimeter detection to control access. The biometrics they have used include hand geometry and fingerprint readers, but he believes that hand geometry readers achieve higher rates of recognition.
Multi-technology proximity readers are used by Cingular Wireless Corp., Atlanta. The company is using them in its thousands of nationwide retail outlets, which have from eight to 16 employees working in each, reports Wes Wallace, regional security director in Dallas for the central region.
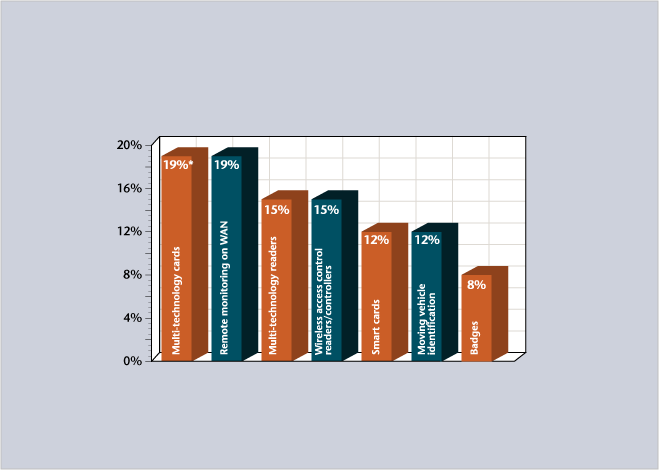
* percentage of respondents
Source: Informal SDM Online Survey of Security Magazine’s End-User Subscribers, June 2005
What’s Around the Corner?
SDM asked end-users to predict which technologies would be desirable in the future to implement at their firms. Baldassare of Valeo Electrical Systems prefers biometrics because of his previous experience with hand geometry readers at an armored car company.Snyder of Honda Federal Credit Union thinks proximity readers still will be popular in the near future because of their cost efficiency, but he envisions them being more intelligent. He also thinks some biometrics, such as hand geometry, will be used in special applications. “That’s all going to depend on what you’re trying to secure,†he suggests.
Wallace of Cingular predicts a move to smart cards at his company in the future. “I don’t know if biometrics will ever take off because of the cost and apprehension on society’s part of big brother watching you,†he muses. “For international applications, they’ll always be there, but [in] general applications across the industry, they won’t take off.â€
He thinks end-users will stay with proximity and smart cards. “Whatever helps move people quicker and faster, because cost and functionality are key quotients in any selection process,†Wallace forecasts.
Pickering of Crescent Sentry thinks retinal and hand scanners will become more prevalent in the next few years. He has not yet installed many retinal scanners, but he thinks people will overcome their ambivalence about the technology.
“I think you’re going to see a lot of intelligent video for access control,†he predicts. “Some systems recognize people’s faces and even their walks. I also think access control is going to go residential – keys will be a thing of the past.â€
Houses with structured wiring could have their access systems tied into the home networks, Pickering forecasts.
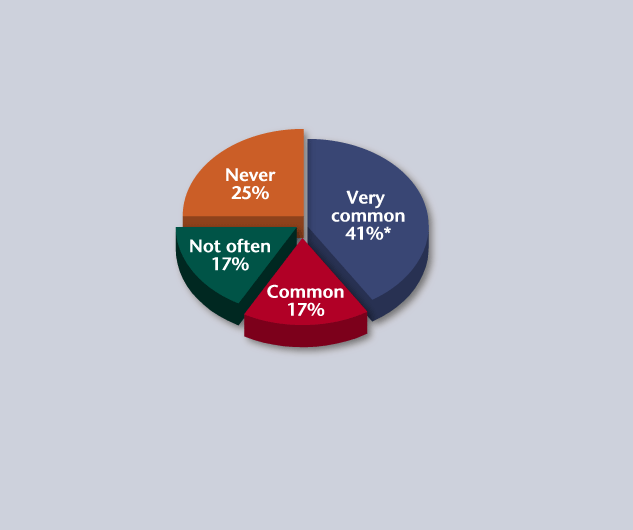
* percentage of respondents
Source: Informal SDM Online Survey of Security Magazine’s End-User Subscribers, June 2005
Among these are wireless mustering stations on Wi-Fi laptops that could detect wireless transponders, such as in RFID tags or smart cards, that are carried by employees.
“In broad strokes, some things you will see in the not-too-distant future are integration of video analytics and access control,†Boriskin predicts. He cited anti-passback or anti-tailgating features for non-turnstile doors. These would prevent badging in again until a person has badged out or not being able to badge out if the person never badged in.
He also predicts that video content analysis will be more prevalent, whereby entrance of three objects would be prevented when only two badge readings were received.
Boriskin also expects the government’s smart card initiative to result in a population of several million federal employees being outfitted with one type of smart card.
“You will then have a large foothold of smart cards in the U.S. that we really haven’t had,†he notes. “That will cause a warming trend on commercial/industrial customers, who traditionally have shied away from smart cards because they were not wanting to pick a losing horse.â€
Whatever leading-edge access technologies become prevalent in the future, reliability, cost and user comfort are sure to be part of the selection equation.
Sidebar: Service, Confidence, Reliability--What They Expect from You
Service after the sale was cited by Anthony Baldassare, chief of security for the Valeo Electrical Systems plant in Rochester, N.Y., as the most important factor in selecting an installation company to provide an access control system.“You have to make sure the people selling the product have the expertise to deliver and install it once they come in,†he emphasizes. “That’s a big issue.
“There’s no regulation of these people here in the Rochester area,†he asserts. “You’ve got people coming through, and if you’re unfortunate enough to listen to them and believe them, and if they go belly-up, you’re stuck with all this equipment. There’s no way to check the reliability or efficiency of the company. You’ve got to go by word-of-mouth and your gut feeling about how you feel about the product.â€
Price isn’t always the foremost consideration, either. “When comparing bids, I wouldn’t see a case where you would go away from a trusted vendor because somebody came in at a slightly lower price. I think the confidence issue is a big one,†comments a respondent to SDM’s informal online survey of end-users.
Reliability of the access control system was cited by another respondent. “From my mind, as somebody involved in day-to-day management of operations, I think the reliability is everything. I think access needs to be as reliable as the key to your front door, and if you provide anything less than that, you’re not taking care of your customers.â€